Visual Studio is a powerful integrated development environment from Microsoft and it’s primarily used for developing apps on the “.NET framework.”
It supports various programming languages which include “C#,” “VB.NET,” and “C++.”

The Cyble Research and Intelligence Labs recently identified that hackers have turned the Visual Studio code into a remote access tool.
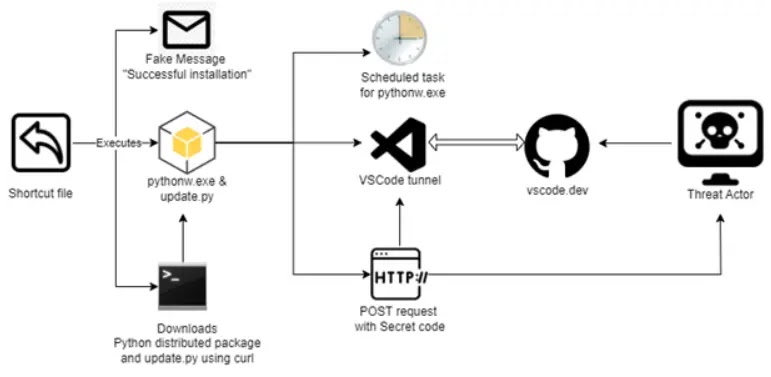
Researchers recently uncovered a sophisticated cyber attack campaign that begins with a malicious “.LNK” file.
This file is possibly distributed via “spam emails,” which shows a fake “Installation Successful” message in ‘Chinese’ while secretly downloading a “Python package” (‘python-3.12.5-embed-amd64.zip’).
A directory at “%LOCALAPPDATA%MicrosoftPython” is created by this file and then it executes an “obfuscated Python script” (‘update.py’) which is retrieved from ‘paste[.]ee’ that had zero detections on ‘VirusTotal.’
Analyse Any Suspicious Links Using ANY.RUN’s New Safe Browsing Tool: Try for Free
The malware establishes persistence by creating a scheduled task named “MicrosoftHealthcareMonitorNode” that runs every 4 hours or at logon with “SYSTEM privileges.”
If Visual Studio Code (“VSCode”) isn’t present, the malware downloads the “VSCode CLI” from Microsoft’s servers (“az764295.vo.msecnd[.]net”) and uses it to create a remote tunnel to generate an “8-character” alphanumeric activation code that enables “unauthorized remote access.”
The script then collects extensive system information from ‘critical directories’ (“C:Program Files, C:Program Files (x86),” “C:ProgramData,” “C:Users”), ‘running processes,’ ‘system language settings,’ ‘geographical location,’ ‘computer name,’ ‘username,’ ‘user domain,’ and ‘privilege levels.’
.webp)
This collected data is “Base64” encoded and exfiltrated to a “C&C server” at “requestrepo[.]com/r/2yxp98b3,” by employing tactics similar to those used by the “Stately Taurus” Chinese APT group.
After successfully intercepting the exfiltrated data the threat actors exploit unauthorized access through GitHub’s authentication system by navigating to “hxxps://github[.]com/login/device” and utilizing stolen alphanumeric activation codes.
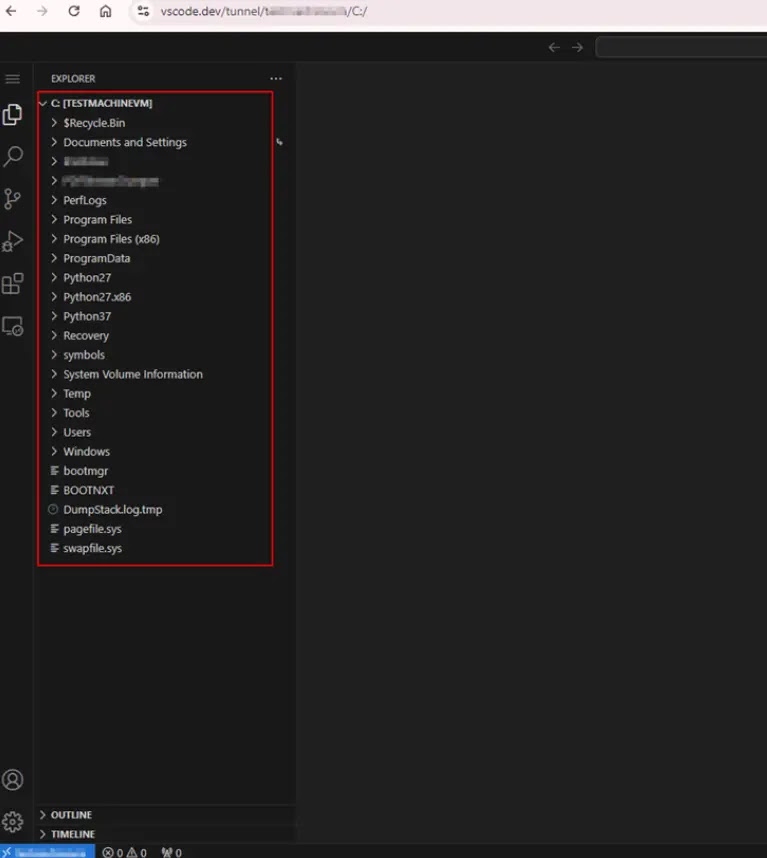
This enables them to establish a VSCode tunnel connection to the victim’s system, which grants comprehensive control over the machine’s “files,” “directories,” and “command-line interface (terminal).”
.webp)
Through this compromised VSCode tunnel connection, attackers can execute powerful hacking tools, including Mimikatz (for credential harvesting), LaZagne (for password recovery), In-Swor (for system reconnaissance), and Tscan (for network scanning).
The attack chain begins with a malicious .LNK file (Windows shortcut) containing an obfuscated Python script, bypassing traditional security measures.
Once established after that, this unauthorized access allows threat actors to perform various malicious activities:-
- Manipulating system files
- Extracting sensitive data
- Modifying system configurations
- Deploying additional malware payloads
This sophisticated attack methodology demonstrates how legitimate development tools like VSCode can be weaponized through social engineering and technical exploitation.
Recommendations
Here below we have mentioned all the recommendations:-
- Use advanced endpoint protection.
- Regularly review scheduled tasks.
- Train users on suspicious files/links.
- Limit software installation and whitelist apps.
- Monitor unusual activity and review logs.
Free Webinar on How to Protect Small Businesses Against Advanced Cyberthreats -> Free Webinar
