Threat actors have discovered a new technique to insert malicious code into websites. They are currently utilizing Eval PHP, an abandoned WordPress plugin.
Mostly, website backdoors are programmed in PHP, the foundational language of the modern web. Most other popular CMS platforms, including Joomla, Magento, and WordPress (which make up over 40% of the web), are based on PHP.
PHP is a highly universal language so attackers can abuse it. Backdoors are one of the most widely used (and misused) by attackers.
Over the past few weeks, PHP code injections have been discovered. These attacks send a previously known payload that allows the attackers to execute code on the infected website remotely.
The ‘wp_posts’ table in the databases of the targeted websites is where the malicious code is introduced. As a result, it avoids standard website security procedures like file integrity monitoring, server-side scanning, etc., making it more difficult to detect.

The threat actors install Eval PHP using a compromised or newly generated administrator account to accomplish this. This enables them to use [evalphp] shortcodes to introduce PHP code into the site’s pages and posts.
The backdoor (3e9c0ca6bbe9.php) is dropped into the site root once the code has finished running. Depending on the attack, the backdoor’s name may change.
Misusing a Reputable Plugin
Researchers identified that attackers breach websites by injecting covert backdoors using Eval PHP, an outdated legitimate WordPress plugin.
Eval PHP enables site administrators to insert PHP code into posts and pages of WordPress websites, which is subsequently executed when the page is loaded in the browser.
The plugin was last updated a decade ago and is usually regarded as outdated, although it’s still available through the WordPress plugin repository.
“For the ten years leading up to the end of March 2023, this plugin rarely had one download a day.” But around March 29, 2023, we saw daily downloads spike to 7,000. After that, we have seen 3k-5k downloads every day, with over 100,000 downloads total”, says Sucuri.
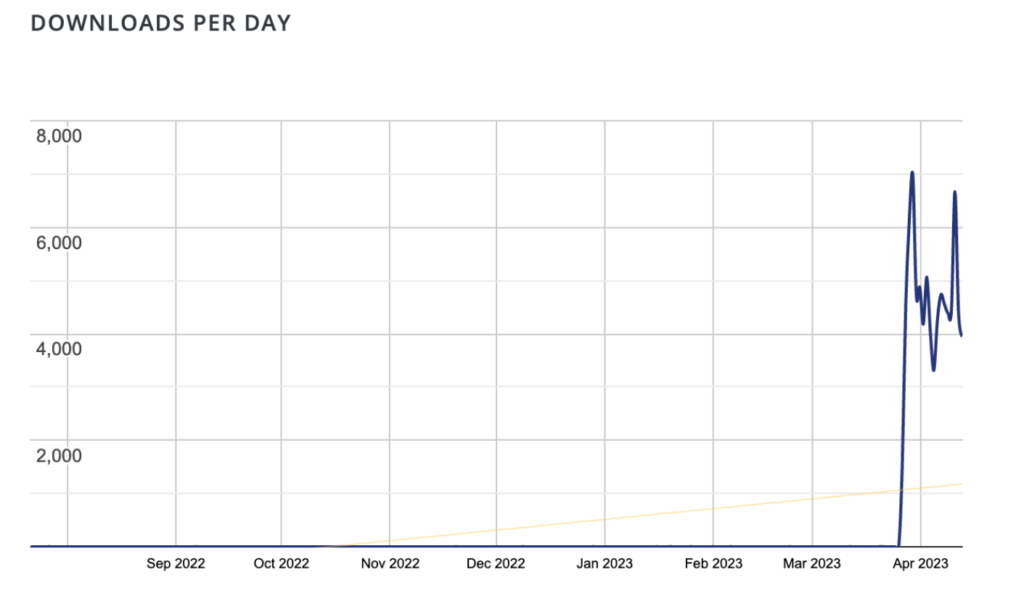
Notably, the key benefit of this approach over traditional backdoor injections is the ability to re-infect cleaned sites with Eval PHP while keeping the point of breach largely secret.
The following three IP addresses are the source of malicious requests:
- 91.193.43.151
- 79.137.206.177
- 212.113.119.6
Researchers say the backdoor sends data through cookies and GET requests without visible parameters for C2 communication instead of using POST requests to avoid detection.
“The way the Eval PHP plugin works,, it’s enough to save a page as a draft to execute the PHP code inside the [evalphp] shortcodes.
“Although the injection in question does drop a conventional backdoor into the file structure, the combination of a legitimate plugin and a backdoor dropper in a WordPress post allows them to reinfect the website and stay hidden easily—all they need to do is visit a “benign” web page,” researchers explain.
When you access the EvalPHP page in the official plugin repository, WordPress displays the following warning:
“This plugin hasn’t been tested withthe latestt three major releases of WordPress. It may no longer be maintained or supported and may have compatibility issues when used with more recent versions of WordPress.”
Researchers say this might not be sufficient for plugins vulnerable to misuse. Such plugins should be completely removed from the list, especially if they haven’t received any updates in more than ten years and have a very small number of genuine users.
Building Your Malware Defense Strategy – Download Free E-Book

