This article explains the inner workings of the Remcos RAT, a dangerous malware that uses advanced techniques to infect Windows systems, steal data, and gain remote control. Learn more about its attack methods, evasion tactics, and the potential impact on users.
Cybersecurity researchers at Fortinet’s FortiGuard Labs have uncovered a dangerous phishing campaign distributing a new Remcos RAT (Remote Access Trojan) variant. This powerful malware, sold commercially online, targets Microsoft Windows users and allows threat actors to remotely control infected computers.
According to Fortinet’s findings, shared with Hackread.com, this campaign was initiated with a deceptive phishing email disguised as an order notification (OLE Excel document). Upon opening the attached malicious Excel document, the CVE-2017-0199 vulnerability is exploited to download and execute an HTML Application (HTA) file.
For your information, CVE-2017-0199 is a Remote Code Execution vulnerability that exploits Microsoft Office and WordPad’s parsing of specially crafted files, allowing the MS Excel program to display the content.
This HTA file, crafted with multiple layers of obfuscation and its code written in different scripts, including JavaScript, VBScript, Base64-encoded, URL-encoded, and PowerShell, delivers the primary payload.
It then downloads a malicious executable (dllhost.exe) and executes it via a 32-bit PowerShell process to extract and deploy the Remcos RAT. The malware modifies the system registry to automatically launch itself upon system startup to ensure persistence.
Remcos connects to a C&C server and sends a registration packet containing system, user, network, and version information about the infected system, and receives commands for information gathering, file operations, remote execution, keylogging, screen recording, and webcam capture.
This new variant employs multiple persistence mechanisms, including advanced anti-analysis techniques like Vectored Exception Handling. This creates a custom exception handler to intercept/handle execution exceptions preventing debugging techniques like single-stepping.
Since it doesn’t store API names directly, Remcos uses hash values to identify APIs, extracting addresses from the Process Environment Block (PEB) by matching hash values, which makes static analysis more challenging as tools cannot easily identify the functions being called.
It also detects debuggers’ presence by checking debug registers (DR0 to DR7), monitoring API calls commonly used by debuggers, and using the ZwSetInformationThread() API to hide the current thread from debuggers. Furthermore, it uses the ZwQueryInformationProcess() API to detect if a debugger is attached to the process and take evasive actions.
Process hollowing is another technique it uses for evading detection. Researchers found that the malware suspends a newly created legitimate process (Vaccinerende.exe), injects its code into the memory, and then resumes it, making it a persistent threat.
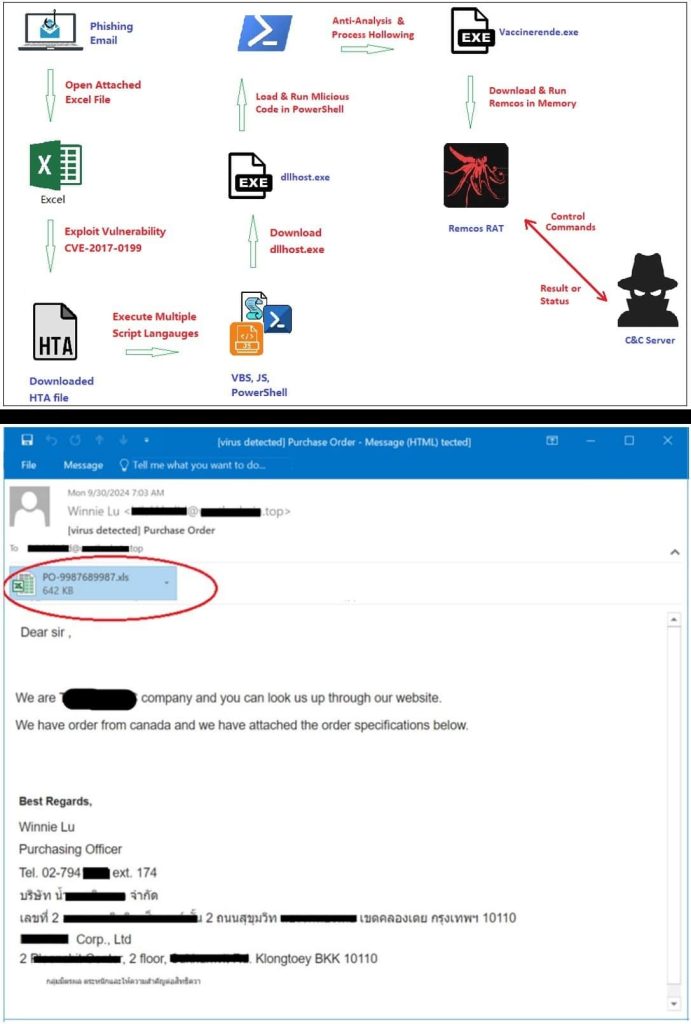
“The malicious code adds a new auto-run item to the system registry to maintain persistence and maintain control of the victim’s device when it is restarted,” researchers noted in their report.
To protect yourself, avoid clicking on links or attachments in emails unless they are legitimate, use security software and antivirus software, keep software updated with the latest patches, and consider Content Disarm and Reconstruction (CDR) service to remove embedded malicious objects from documents before opening them.
RELATED TOPICS
- P2Pinfect Botnet Now Targets Servers with Ransomware
- ValleyRAT Hits Chinese Windows Users in Multi-Stage Attack
- Rust-Based Injector Deploys Remcos RAT in Multi-Stage Attack
- SteelFox Malware Posing as Popular Software, Steal Browser Data
- Fake OnlyFans Checker Tool Infects Hackers with Lummac Stealer
