The North Korean state-backed hacker group tracked as Lazarus has been exploiting a critical vulnerability (CVE-2022-47966) in Zoho’s ManageEngine ServiceDesk to compromise an internet backbone infrastructure provider and healthcare organizations.
The campaigns started early this year and aimed at breaching entities in the U.S. and U.K. to deploy the QuiteRAT malware and a newly discovered remote access trojan (RAT) that researchers are calling CollectionRAT.
CollectionRAT came to light after researchers analyzed the infrastructure used for the campaigns, which the threat actor had used for other attacks as well.
Attacks on internet companies
Cisco Talos researchers observed attacks against UK internet firms in early 2023, when Lazarus leveraged an exploit for CVE-2022-47966, a pre-authentication remote code execution flaw affecting multiple Zoho ManageEngine products.
“In early 2023, we observed Lazarus Group successfully compromise an internet backbone infrastructure provider in the United Kingdom to successfully deploy QuiteRAT. The actors exploited a vulnerable ManageEngine ServiceDesk instance to gain initial access,” Cisco Talos
The analysts report that Lazarus started using the exploit just five days became publicly available. Multiple hackers leveraged the exploit in attacks, as observed by Rapid7, Shadowserver, and GreyNoise, prompting CISA to issue a warning to organizations.
After exploiting the vulnerability to breach a target, Lazarus hackers dropped the QuiteRAT malware from an external URL using a curl command.
QuiteRAT, discovered in February 2023, is described as a simple yet powerful remote access trojan that appears to be a step up from the better known MagicRAT that Lazarus used in the second half of 2022 to target energy providers in the U.S., Canada, and Japan.
Researchers say that QuiteRAT’s code is leaner than MagicRAT’s, and the careful selection of Qt libraries has reduced its size from 18MB to 4MB while retaining the same set of functions.
New Lazarus malware
In a separate report today, Cisco Talos said that Lazarus hackers have a new malware called CollectionRAT. The new threat was found after researchers examined infrastructure the actor used in other attacks.
The researchers say that CollectionRAT appears related to the “EarlyRAT” family.
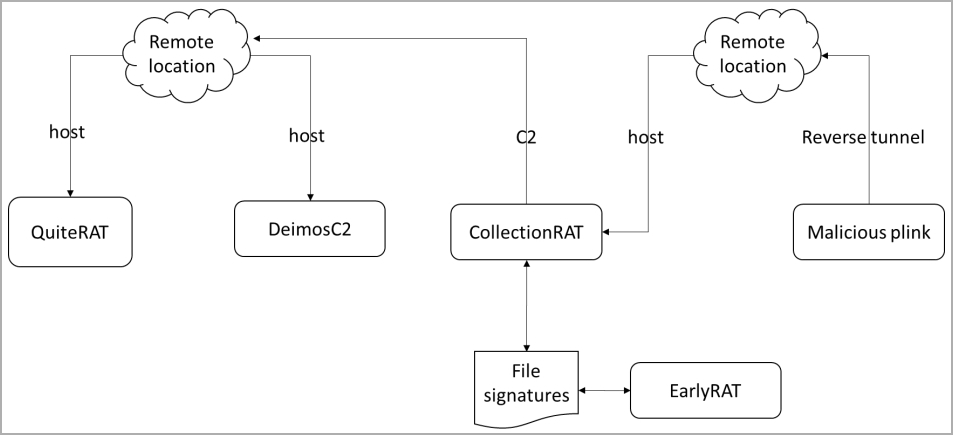
Earlier this year, Kaspersky associated EarlyRAT with Andariel (“Stonefly), believed to be a subgroup within the Lazarus team.
The capabilities of CollectionRAT include arbitrary command execution, file management, system information gathering, reverse shell creation, new process spawning, fetching and launching new payloads, and self-deletion.
Another interesting element in CollectionRAT is the incorporation of the Microsoft Foundation Class (MFC) framework, which allows it to decrypt and execute its code on the fly, evade detection, and thwart analysis.
Additional signs of evolution in Lazarus’ tactics, techniques, and procedures that Cisco Talos spotted include the extensive use of open-source tools and frameworks, such as Mimikatz for stealing credentials, PuTTY Link (Plink) for remote tunneling, and DeimosC2 for command and control communication.
This approach helps Lazarus leave fewer distinct traces behind and hence makes attribution, tracking, and the development of effective protective measures harder.




