Using fake certificates, attackers gain unauthorized access to corporate network resources.
Attackers use such certificates to trick the Key Distribution Center (KDC) to get into the target company’s network.
Shadow Credentials are an example of such an attack. This technique allows an attacker to take over an AD user or computer account.
Certificate-based TGT- Requests
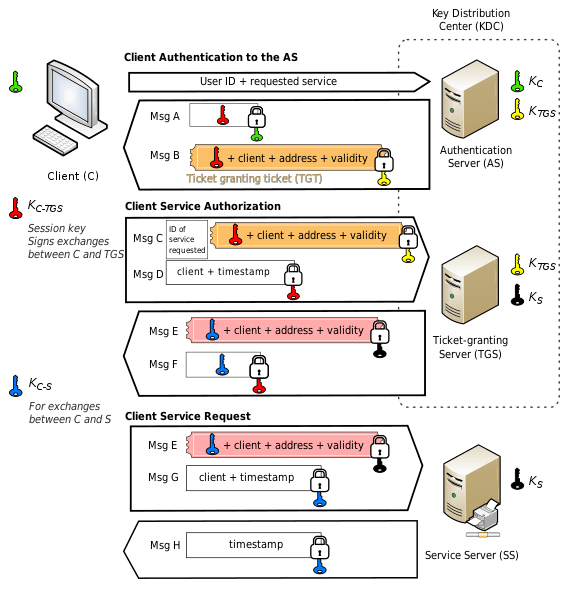
In Kerberos authentication, a Ticket Granting Ticket (TGT) is a user authentication token issued by the Key Distribution Center (KDC).
A key distribution center (KDC) in cryptography is a system that is responsible for providing keys to the users in a network that shares sensitive or private data.
TGT is used to request access tokens from the Ticket Granting Service (TGS) for specific resources/systems joined to the domain.
Essentially, a TGT is proof of successful user authentication, usually by password.
The alternate way to get TGT is by using a certificate. The KDC must trust the provided certificate, and the certificate must relate to the subject requested in the TGT.
The method is called Public Key Cryptography for Initial Authentication (PKINIT).
Having Active Directory Certificate Services (AD CS) in the corporate network to issue certificates for domain users would actually make it quite easy to set up authentication.
However, not all corporate networks have AD CS. The msDS-KeyCredentialLink attribute was invented for this reason, where the certificate can be written.
(msDS-KeyCredentialLink attribute used to link an RSA key pair with a computer or user object in order to authenticate with said key pair against the KDC to receive a Kerberos TGT)
Therefore KDC will trust this certificate and issue a TGT. But the challenge is the subject that writes the msDS-KeyCredentialLink attribute to some object will also be able to get a ticket for this object.
Illustration of the Attack
Consider logan_howard, having write access in the AD domain, writes a public key to msDS-KeyCredentialLink attribute for a domain controller object using Whisker.
Whisker is a C# tool for taking over AD users and computer accounts by manipulating their msDS-KeyCredentialLink attribute.
The subject receives the TGT issued to the domain controller.
With the TGT, the subject receives a TGS ticket to synchronize password information in the domain.
The attacker then “synchronizes” the hash from the domain administrator account to impersonate the administrator for the purpose of gaining access to data and moving laterally inside the corporate network.
As a part of the research, Securelist gets the KDC to trust a particular certificate, including stolen or forged ones. This triggered event 4768 on the domain controller.
This event may contain artifacts from the certificate used for authentication, with three fields: CertIssuerName, CertSerialNumber, and CertThumbprint.
Kaspersky created several TGT request events based on a forged certificate generated using Whisker.
The attack is relatively effective and can be detected only when a forged certificate is used. “Knowledge of the infrastructure (ideally including a list of all active keys) and monitoring will assist the security expert in this,” said Securelist, a cybersecurity and research company.
Keep yourself informed about the latest Cyber Security News by following us on GoogleNews, Linkedin, Twitter, and Facebook.
