The Unit42 research team at Palo Alto Networks has recently discovered Trigona ransomware that attacks Windows with uncommon techniques and uses the Mimikatz exploitation tool for Credential Loading, Dumping, Manipulation, and injection before attempting to encrypt the files.
Trigona ransomware was first discovered in October 2022, and it was very active in December 2022. During its last discovery, it has affected almost 15 organizations in Manufacturing, Finance, Construction, marketing, and high technology industries.
As of January and February of this year, four ransom notes of Trigona were found, with two each month.
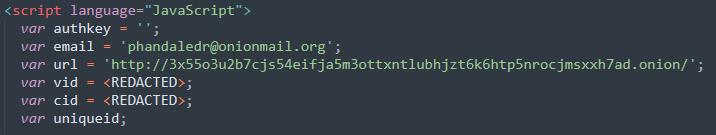
Unlike other ransomware notes, Trigona notes were not plain-text files. Instead, it is an HTML application with JS embedded. It also contains CIDs (Computer IDs) and VIDs (Victim IDs).
Trigona Ransomware Overview
A security researcher tweeted that the creators obtain initial access to a victim’s environment, conducting an active reconnaissance, malware transfer through remote monitoring and management (RMM), and user account creation and deployment.
As per reports, this ransomware has a list of command lines and is supported by TDCP_rijndael ( a Delphi AES library) for encrypting files.
The extension of the affected files is with ._locked. However, the ransom note will have a filename and extension as how_to_decrypt.hta .
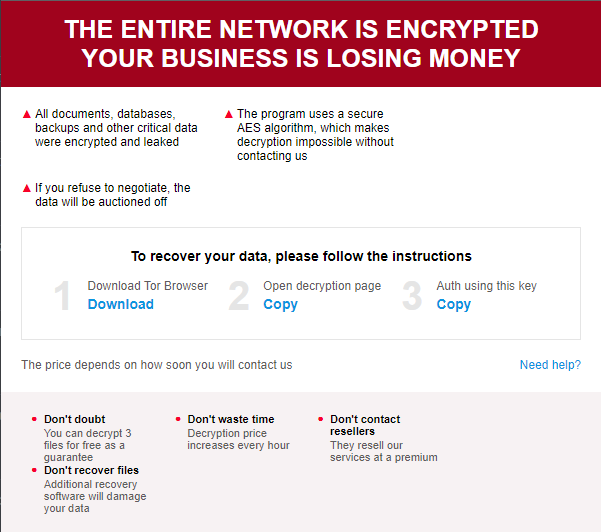
As stated, the ransom note is an HTML file with JS embedded. Further observation of the file showed some parameters containing the following information.
- CID and VID
- Email Address (Attacker)
- TOR URL for negotiation.
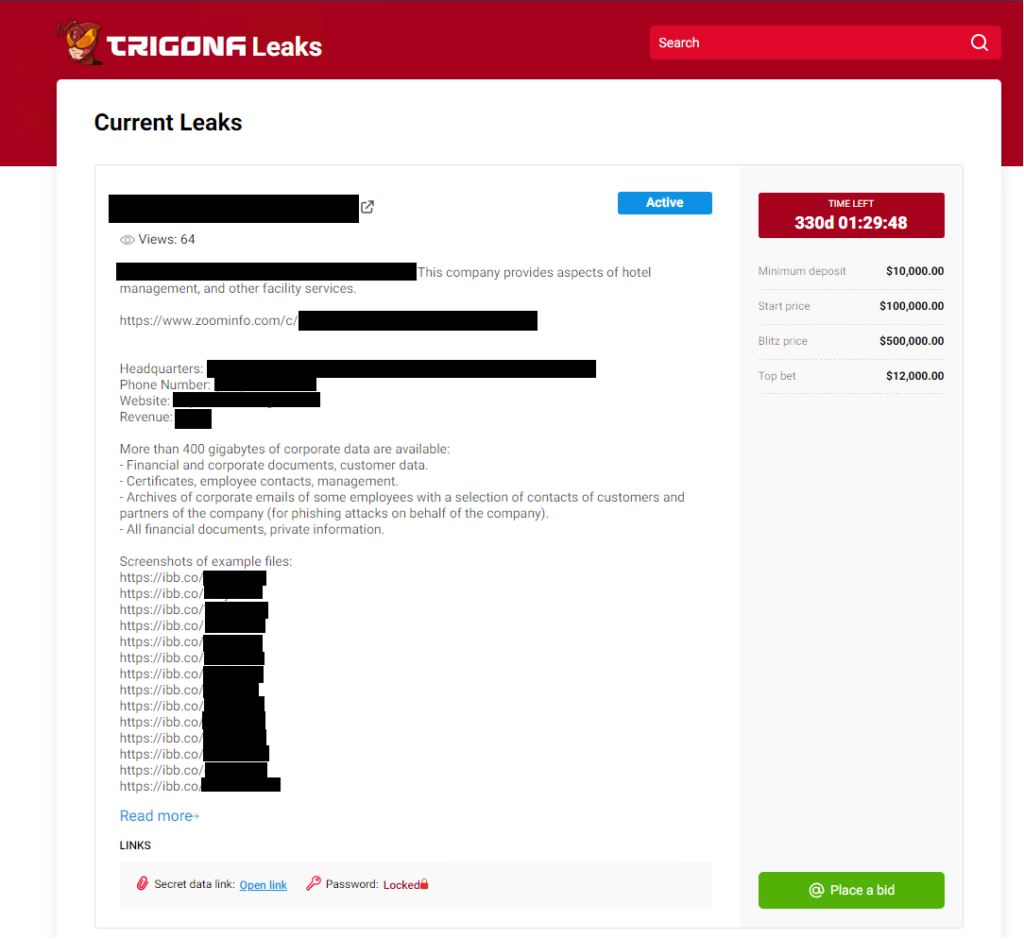
The report also mentioned that a website was associated with the ransomware leaking the stolen files. There was also an option to bid this information through an email address.
Binaries supported by Trigona
| Argument | Description |
| /full | Performs all functions of the ransomware. Encrypts both local and network files. Creates two registry keys for persistence, one for the ransomware binary and another for the ransom note. |
| /!autorun | Skips creation of registry keys for persistence |
| /test_cid “test” | Overwrites default victim generated CID and replace with “test” value |
| /test_vid “test” | Overwrites default VID and replace with “test” value |
| /p, /path “path” | Encrypts only files contained within specified path |
| /!local | Does not encrypt local system files, only encrypts files on local network |
| /!lan | Does not encrypt local network files, only encrypts files on local system |
| /autorun_only “path” | Creates registry key for persistence only. Allows for optional “path” to be provided to override default path, does not encrypt files |
DC2.exe – DC4.exe – DC6.exe
Trigona’s currently developing leak site, the operator and/or affiliates behind the ransomware likely will continue (and possibly even ramp up) its malicious activity.
A password-protected version of Mimikatz, a program for extracting sensitive information from a Windows operating system, such as passwords and authentication credentials.
- Loading Credentials – Mimikatz retrieves credentials from various locations, including Windows memory, the Local Security Authority Subsystem Service (LSASS) process, and the Windows registry.
- Dumping of Credentials – The utility then extracts and dumps the credentials to the screen or a file, including usernames and passwords, hashes, and Kerberos tickets.
- Manipulation of Credentials – Mimikatz allows users to change passwords, create new user accounts, and add people to groups using the leaked credentials.
- Injection of Credentials – The altered credentials can also be injected into other processes, allowing the user to impersonate another user and access restricted resources.
DC4.exe is a small, UPX-packed password-protected binary that generates and executes an embedded batch file. Like DC2.exe, the password to allow the binary to run is boris.
DC6.exe is an installer for the publicly available tool Advanced Port Scanner, wrapped up in an Inno Setup installer package.
“Trigona’s currently developing leak site, the operator and/or affiliates behind the ransomware likely will continue (and possibly even ramp up) its malicious activity.” Palo Alto Concluded.
This ransomware has similarities to CryLock ransomware which also includes the Tactics, Techniques, and Procedures (TTPs); Unit 42 Palo Alto published a Complete report.
Building Your Malware Defense Strategy – Download Free E-Book
Also Read:

