A sophisticated technique uncovered where threat actors abuse Amazon Web Services‘ X-Ray distributed tracing service to establish covert command and control (C2) communications, demonstrating how legitimate cloud infrastructure can be weaponized for malicious purposes.
AWS X-Ray, designed to help developers analyze application performance through distributed tracing, has been repurposed by red team researchers into a steganographic communication channel called XRayC2.
This technique leverages X-Ray’s annotation system, which allows arbitrary key-value data storage, to transmit commands and exfiltrate data through legitimate AWS API calls to xray.[region].amazonaws.com endpoints.
Weaponizing AWS X-Ray for Covert Command and Control
According to Dhiraj, the attack methodology exploits X-Ray’s trace segments functionality, where malicious payloads are embedded within seemingly benign monitoring data.
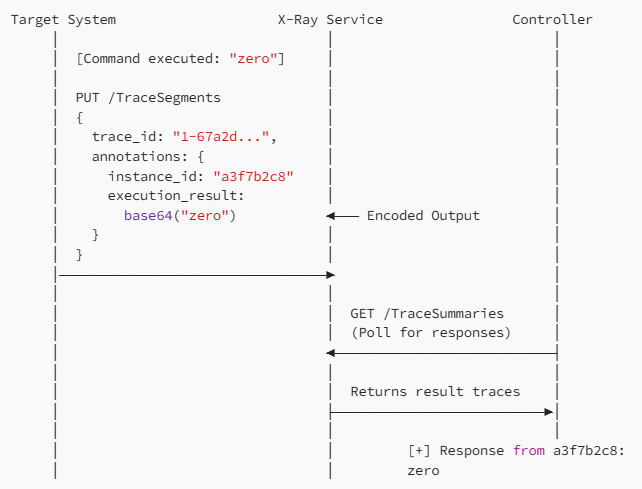
Attackers utilize the service’s PutTraceSegments, GetTraceSummaries, and BatchGetTraces API endpoints to establish bidirectional communication channels that blend seamlessly with legitimate cloud traffic.
The implant establishes presence through beacon markers containing system information encoded in trace annotations, including service type identifiers like “health_check” and unique instance identifiers.
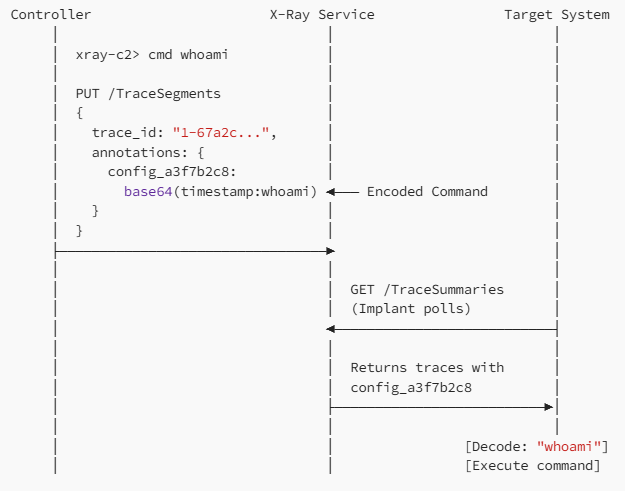
Command delivery occurs through base64-encoded payloads stored in configuration annotations, while result exfiltration leverages execution_result fields within trace data structures.
This technique demonstrates sophisticated evasion capabilities by implementing custom AWS Signature Version 4 (SigV4) authentication, creating legitimate AWS API traffic that integrates naturally with standard network logs.
The malicious communication employs randomized beacon intervals between 30 and 60 seconds and utilizes HMAC-SHA256 signing with access keys, following Amazon’s canonical request format.
The XRayC2 toolkit requires minimal AWS permissions, utilizing the AWSXRayDaemonWriteAccess policy alongside custom permissions for trace manipulation.
This approach significantly reduces the attack surface compared to traditional C2 infrastructure while maintaining persistent access through cloud-native services.
Detection of this technique presents challenges for security teams, as the malicious traffic appears as standard application performance monitoring activities.
Organizations should implement enhanced monitoring of X-Ray API usage patterns, establish baseline metrics for trace annotation data volumes, and scrutinize unusual service interactions within their AWS environments to identify potential abuse of legitimate cloud services for covert communications.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
