Cybersecurity researchers have observed a surge in phishing campaigns leveraging QR codes to deliver malicious payloads.
This emerging threat, often dubbed “quishing,” exploits the opaque nature of QR codes to conceal harmful URLs that redirect victims to credential-harvesting sites or malware downloads.
Unlike traditional phishing links that can be flagged by email gateways, QR codes require a visual scan by the end user—typically on a mobile device—circumventing desktop security controls and expanding the attacker’s window of opportunity.
The earliest instances appeared in generic mass-email blasts posing as routine account notifications from well-known service providers.
However, attackers have rapidly refined their tactics, tailoring messages to specific targets and embedding QR codes within seemingly innocuous images.
In one campaign, a threat actor impersonated a leading cloud storage provider, prompting recipients to “scan to verify account activity.”
Upon scanning, the QR code resolved to a fake login portal meticulously crafted to mirror the legitimate site’s HTML and JavaScript.
Barracuda analysts noted this initial wave of quishing attacks relied heavily on social engineering rather than technical sophistication.
As defenders began to recognize and block simple QR code attacks, adversaries escalated their techniques.
Split QR codes emerged as a stealthier method, dividing a single code into two separate image fragments that appear benign when viewed independently.
.webp)
Email scanners inspecting image attachments typically miss two partial images, yet when rendered in an HTML email they recombine visually into a scannable QR pattern. Victims who scan the composite code are redirected to sites designed to harvest credentials or deploy secondary payloads.
Detection Evasion Through Nested QR Codes
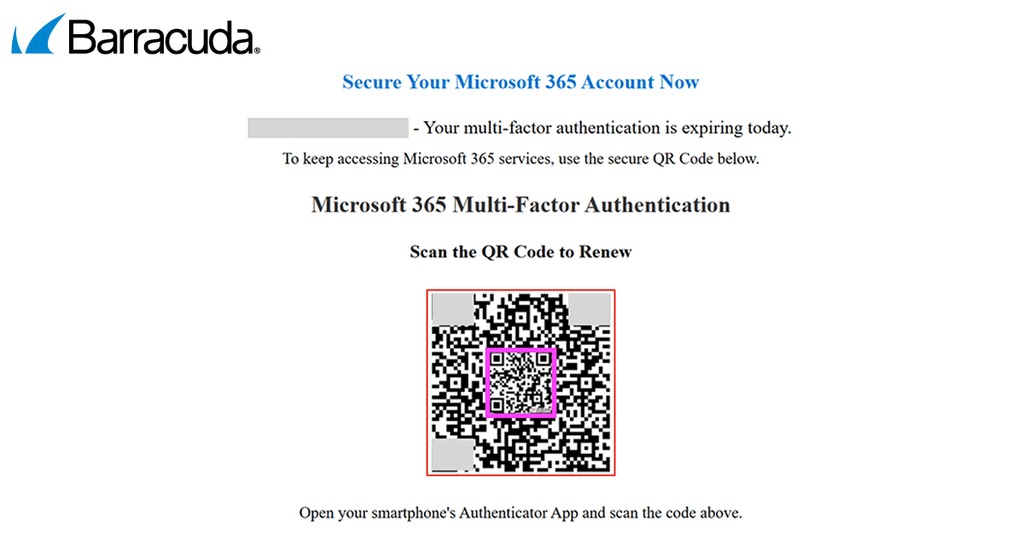
Beyond splitting, the latest quishing kits employ nested QR codes to further obfuscate malicious links.
A nested code consists of an inner, benign QR pointing to a harmless URL (e.g., Google), surrounded by an outer code directing to a phishing domain.
This dual-layer approach generates ambiguous decoding results: standard QR readers often default to the inner code, while more sophisticated decoders can extract the outer payload.
Attackers exploit this ambiguity to bypass QR analysis tools that lack the ability to interpret multiple layers within a single frame.
.webp)
To illustrate, the following Python snippet uses the pyzbar library to decode layered QR images and highlight both payloads:-
from PIL import Image
from pyzbar.pyzbar import decode
img = Image.open('nested_qr_code.png')
results = decode(img)
for res in results:
print(f'Data: {res.data.decode()}, Type: {res.type}') Defenders must adopt multimodal AI solutions capable of rendering images, isolating pixel patterns, and performing sandboxed link execution.
As organizations bolster spam filters and enforce multi-factor authentication, attackers will undoubtedly continue to innovate. Vigilance, layered defenses, and user training remain critical to counteract this evolving quishing threat.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.
