A recent investigation by Security Joes has unveiled a novel cyberattack method targeting the Windows operating system. This technique exploits the trusted WinSxS folder, a critical component of Windows, using a sophisticated approach known as DLL Search Order Hijacking. This discovery sheds light on a new avenue for threat actors to execute malicious code without high privilege requirements.
DLL Search Order Hijacking is a security vulnerability that can occur in Windows operating systems. It exploits the way Windows searches for Dynamic Link Libraries (DLLs) when an application is run. Here’s a detailed explanation:
Background: Dynamic Link Libraries (DLLs)
- DLLs: DLL files are a type of file that contain code and data that can be used by multiple programs at the same time. They promote code reusability and efficient memory usage.
- Usage: When a Windows application runs, it often requires additional functionality that is provided by these DLLs.
How Windows Searches for DLLs
- Search Order: Windows has a specific order in which it searches for a required DLL. It usually starts with the directory from which the application was launched, and then moves through a set of predefined directories (like the System32 folder). The general flow followed by the Windows operating system when searching and loading external resources is as follows:
- The directory from which the application is launched.
- The folder “C:WindowsSystem32”.
- The folder “C:WindowsSystem”.
- The folder “C:Windows”.
- The current working directory.
- Directories listed in the system’s PATH environment variable.
- Directories listed in the user’s PATH environment variable.
- No Verification: If Windows does not verify the authenticity of the DLL before loading it, this creates a vulnerability.
Exploiting the DLL Search Order
- Hijacking Scenario: An attacker places a malicious DLL with the same name as a legitimate one into a directory that precedes the legitimate DLL’s directory in the search order.
- Application Execution: When an application tries to load the DLL, it inadvertently picks up the malicious one instead of the legitimate one.
- Consequence: The malicious DLL can then execute code with the same privileges as the application. This could lead to unauthorized access, data leakage, or other malicious activities.
Example
Suppose there’s an application that requires a DLL named example.dll which is usually located in the System32 folder. If an attacker places a malicious DLL named example.dll in the application’s directory, the application will load the malicious DLL instead of the legitimate one.
DLL Search Order Hijacking is a significant security concern, especially for applications that do not explicitly specify the path to the required DLLs or that run with high privileges. Awareness and implementation of mitigation strategies are key to protecting systems from this type of vulnerability.
The WinSxS folder, short for Windows Side by Side, is a crucial directory in the Windows operating system. It stores multiple versions of DLLs and other system components to resolve compatibility issues. Due to its importance and trusted status, it is typically overlooked as a potential security threat.
The key purposes of the WinSxS folder include:
- Version Management: It stores multiple versions of Dynamic Link Libraries (DLLs) and system files, ensuring efficient access as needed. This capability is crucial for maintaining compatibility with various applications, as different programs may require specific versions of the same component.
- System Integrity: The WinSxS folder helps maintain the integrity of the system by preventing incorrect or corrupted versions of system files from replacing the correct ones. This safeguard ensures the stability and reliability of the operating system.
- Dynamic Activation: The folder facilitates the dynamic activation or deactivation of Windows features, eliminating the need for separate installations. This flexibility allows users to enable or disable specific features as required.
The Exploitation Technique: Security Joes’ investigation reveals that attackers are leveraging executables commonly found in the WinSxS folder. By employing DLL Search Order Hijacking, they can execute malicious code within applications located in the Windows folder, specifically targeting WinSxS. This method bypasses the need for high-level privileges usually required to run harmful code in protected areas of the operating system. Below is table summarizing the vulnerable executables located in the WinSxS folder during research and the corresponding resources which are searched during its execution.
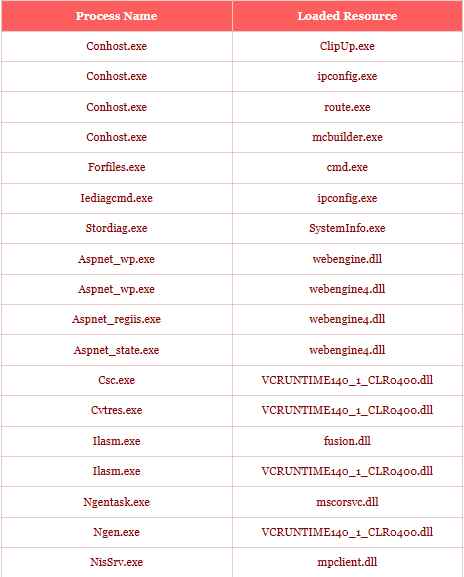
Implications of the Attack: This innovative attack vector is particularly concerning because it does not require additional binaries in the attack chain. It allows threat actors to execute malicious code from any location, significantly lowering the barrier to successful exploitation. The use of a trusted system folder like WinSxS further complicates detection and prevention efforts.
Security Measures and Recommendations: To mitigate the risk posed by this new attack method, Security Joes recommends increased vigilance and enhanced security measures. This includes regular monitoring of the WinSxS folder for unusual changes, employing advanced threat detection tools, and educating IT personnel about this new threat vector.
Mitigation Strategies
- Safe DLL Loading: Implementing secure coding practices to ensure that applications only load DLLs from trusted sources.
- Code Signing: Using code signing to verify the authenticity of DLLs before they are loaded.
- Path Auditing: Regularly auditing system and application paths for unexpected or untrusted directories.
- User Privileges: Running applications with the least privileges necessary to reduce the impact of a potential hijack.
- Security Software: Using antivirus and other security solutions to detect and prevent malicious activities related to DLL hijacking.
Conclusion: The discovery of the WinSxS hijacking technique represents a significant development in the landscape of cybersecurity threats. It underscores the need for continuous adaptation of security strategies to counter evolving attack methods. As threat actors become more sophisticated, understanding and anticipating their tactics is crucial for maintaining robust cybersecurity defenses.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
