
Have I Been Pwned has added almost 71 million email addresses associated with stolen accounts in the Naz.API dataset to its data breach notification service.
The Naz.API dataset is a massive collection of 1 billion credentials compiled using credential stuffing lists and data stolen by information-stealing malware.
Credential stuffing lists are collections of login name and password pairs stolen from previous data breaches that are used to breach accounts on other sites.
Information-stealing malware attempts to steal a wide variety of data from an infected computer, including credentials saved in browsers, VPN clients, and FTP clients. This type of malware also attempts to steal SSH keys, credit cards, cookies, browsing history, and cryptocurrency wallets.
The stolen data is collected in text files and images, which are stored in archives called “logs.” These logs are then uploaded to a remote server to be collected later by the attacker.
Regardless of how the credentials are stolen, they are then used to breach accounts owned by the victim, sold to other threat actors on cybercrime marketplaces, or released for free on hacker forums to gain reputation amongst the hacking community.
The Naz.API dataset
The Naz.API is a dataset allegedly containing over 1 billion lines of stolen credentials compiled from credential stuffing lists and from information-stealing malware logs. It should be noted that while the Naz.API dataset name includes the word “Naz,” it is not related to network attached storage (NAS) devices.
This dataset has been floating around the data breach community for quite a while but rose to notoriety after it was used to fuel an open-source intelligence (OSINT) platform called illicit.services.
This service allows visitors to search a database of stolen information, including names, phone numbers, email addresses, and other personal data.
The service shut down in July 2023 out of concerns it was being used for Doxxing and SIM-swapping attacks. However, the operator enabled the service again in September.
Illicit.services use data from various sources, but one of its largest sources of data came from the Naz.API dataset, which was shared privately among a small number of people.
Each line in the Naz.API data consists of a login URL, its login name, and an associated password stolen from a person’s device, as shown below.
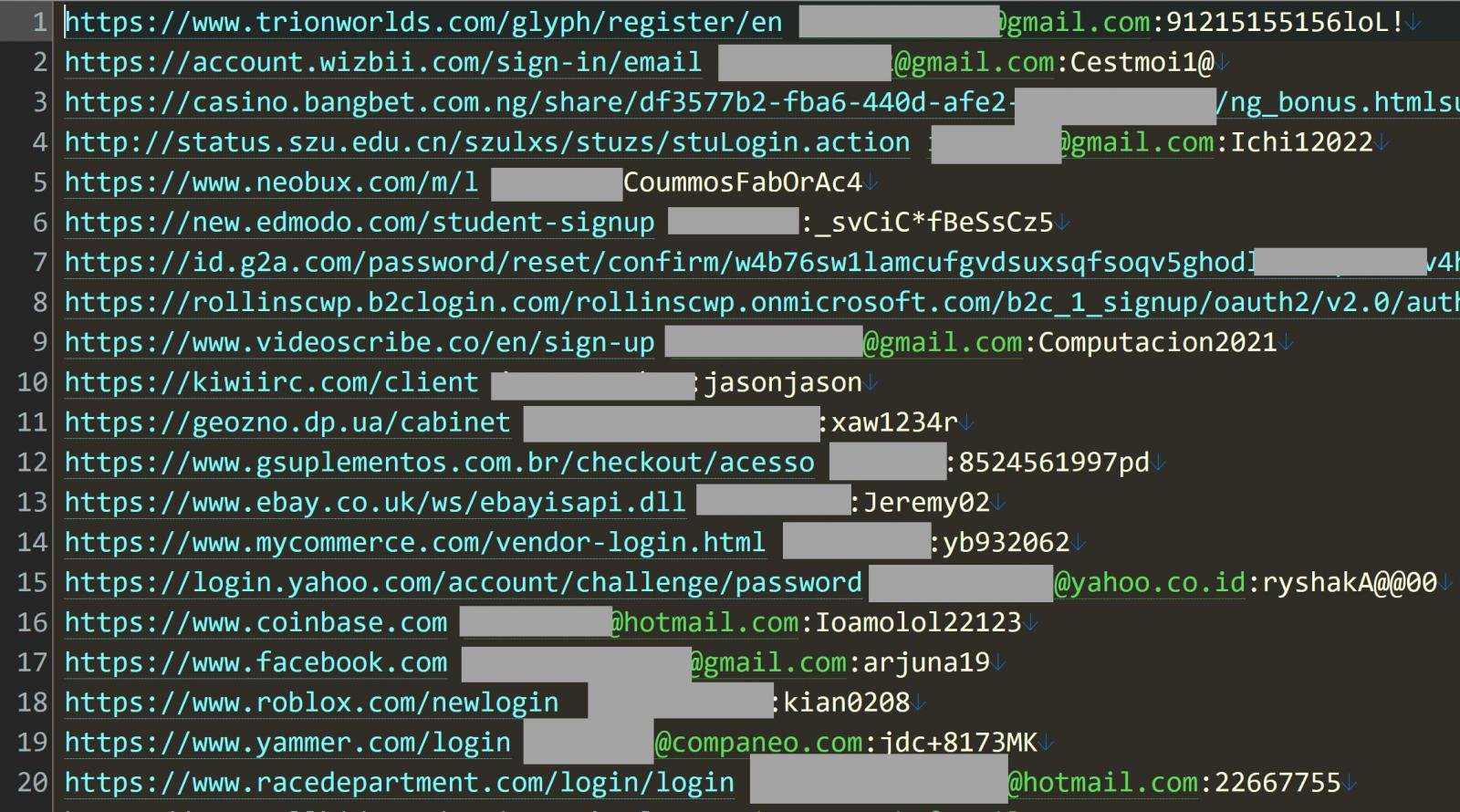
Source: Troy Hunt
Naz.API added to HIBP
Today, Troy Hunt, the creator of Have I Been Pwned, announced he added the Naz.API dataset to his data breach notification service after he received it from a well-known tech company.
“Here’s the back story: this week I was contacted by a well-known tech company that had received a bug bounty submission based on a credential stuffing list posted to a popular hacking forum,” explained a blog post by Hunt.
“Whilst this post dates back almost 4 months, it hadn’t come across my radar until now and inevitably, also hadn’t been sent to the aforementioned tech company.”
“They took it seriously enough to take appropriate action against their (very sizeable) user base which gave me enough cause to investigate it further than your average cred stuffing list.”
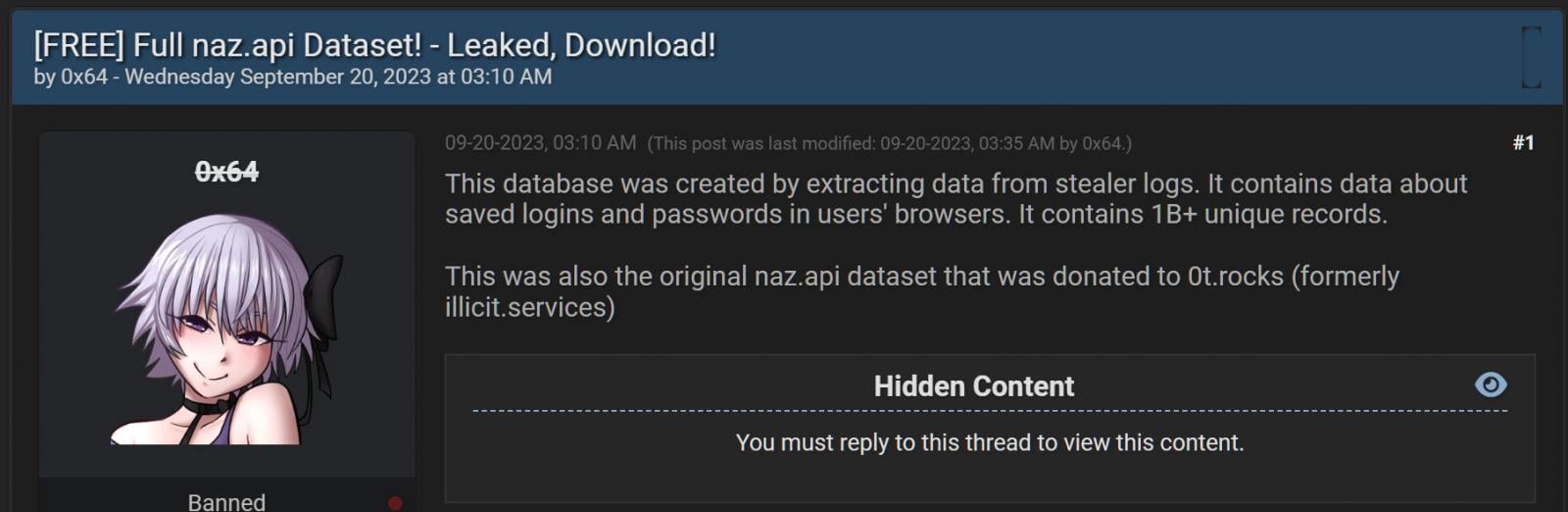
Source: BleepingComputer
According to Hunt, the Naz.API dataset consists of 319 files totaling 104GB and containing 70,840,771 unique email addresses.
However, while there are 70 million unique emails, for each email address, there are likely many other records for the different sites’ credentials were stolen from.
Hunt says the Naz.API data is likely old, as it contained one of his and other HIBP subscribers’ passwords that were used in the past. Hunt says his password was used in 2011, meaning that some of the data is over 13 years old.
To check if your credentials are in the Naz.API dataset, you can perform a search at Have I Been Pwned. If your email is found to be associated with Naz.API, the site will warn you, indicating that your computer was infected with information-stealing malware at one point.
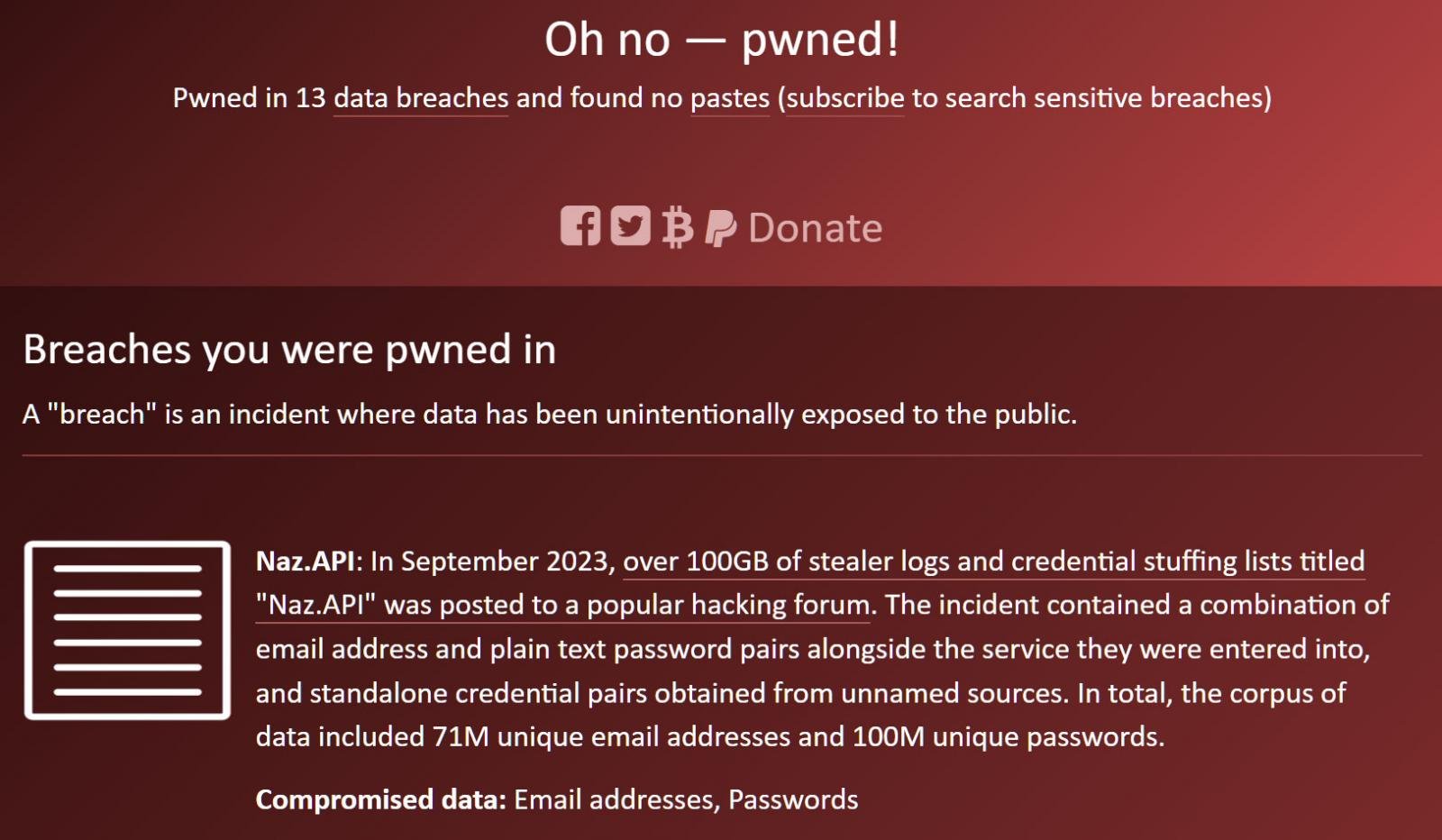
Source: BleepingComputer
Unfortunately, even if HIBP warns you that your email was in the Naz.API, it does not tell you for what specific website credentials were stolen.
As this dataset is partially linked to information-stealing malware, it’s recommended to change passwords for all your saved accounts.
This includes passwords for corporate VPNs, email accounts, bank accounts, and any other personal accounts.
Furthermore, as info-stealers attempt to steal cryptocurrency wallets, you should immediately transfer any crypto to another wallet if you own any.
For more detailed information about what accounts were exposed, you can try the Illicit.Services website, which is currently overwhelmed with everyone attempting to use it.




