Swiss global solutions provider Ascom has confirmed a cyberattack on its IT infrastructure as a hacker group known as Hellcat targets Jira servers worldwide using compromised credentials.
The company announced in a press release that hackers on Sunday breached its technical ticketing system and is currently investigating the incident.
Ascom is a telecommunications company with subsidiaries in 18 countries focusing on wireless on-site communications.
HellCat hacking group claimed the attack and told BleepingComputer that they stole about 44GB of data that may impact all of the company’s divisions.
Ascom says that the hackers compromised its technical ticketing system, the incident had no impact on the company’s business operations, and that customers and partners do not need to take any preventive action.
“Investigations against such criminal offenses were initiated immediately and are ongoing. Ascom is working closely with the relevant authorities” – Ascom
Rey, a member of the HellCat hacking group, told BleepingComputer that they stole from Ascom source code for multiple products, details about various projects, invoices, confidential documents, and issues from the ticketing system.
The Swiss company did not provide technical details about the breach but targeting the Jira ticketing system has become a common attack method for the HellCat hackers.
HellCat on a Jira hacking spree
Jira is a project management and issue-tracking platform commonly used by software developers and IT teams to track and manage projects. The platform often contains sensitive data, such as source code, authentication keys, IT plans, customer information, and internal discussions related to these projects.
Previous incidents claimed by HellCat and confirmed by the targeted companies count Schneider Electric, Telefónica, and Orange Group, and in all three instances the hackers breached their way in through Jira servers.
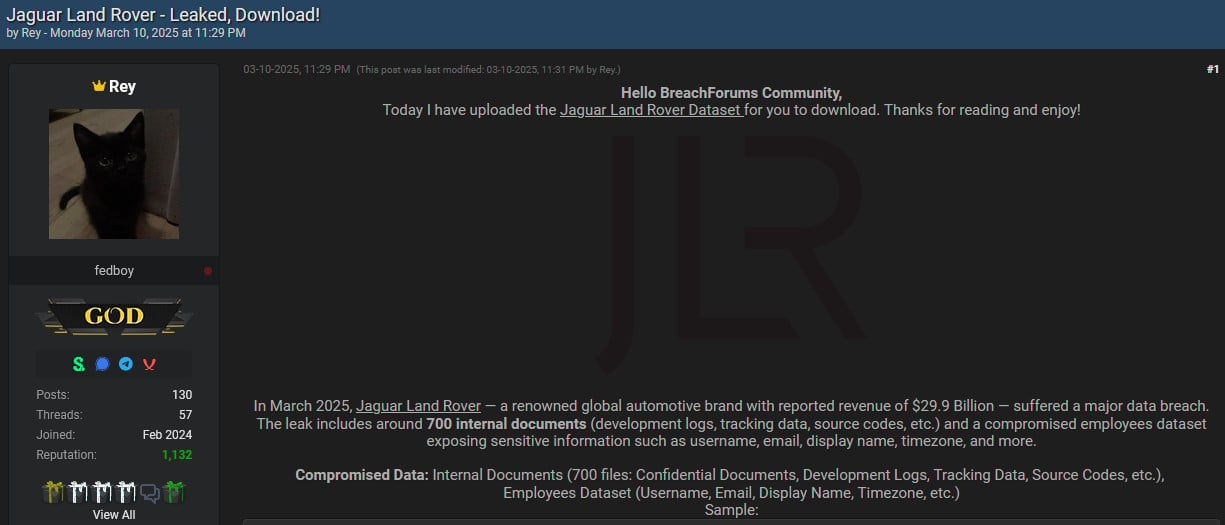
Recently, the same hackers also took responsibility for an attack on the British multinational car maker Jaguar Land Rover (JLR) and stole and leaked about 700 internal documents.
As the threat actor describes it, the leak includes “development logs, tracking data, source codes” and an employee’s data that exposed “sensitive information such as username, email, display name, timezone, and more.”
Alon Gal, co-founder and CTO at threat intelligence company Hudson Rock, says the JLR breach follows a pattern specific to HellCat hackers.
“At the heart of this latest incident lies a technique that has become HELLCAT’s signature: exploiting Jira credentials harvested from compromised employees that were infected by Infostealers” – Alon Gal
The researcher said that the JLR incident was possible by using the credentials of an LG Electronics employee with third-party credentials to JLR’s Jira server.
Gal highlights that the compromised credentials were not fresh and had been exposed for several years but remained valid all this time, allowing hackers to take advantage.
HellCat’s activity didn’t stop at these breaches as the threat actor announced today that they compromised the Jira system of Affinitiv, a marketing company that provides data analytics a platform for OEMs and dealerships in the automotive industry.
The threat actor confirmed to BleepingComputer that they breached Affinitiv through a Jira system and disclosed publicly that they stole a database with a little over 470,000 “unique emails” and more than 780,000 records.
When contacted by BleepingComputer about the alleged attack, Affinitiv said that they had begun an investigation.
To prove the breach, hackers published two screenshots with names, email addresses, postal addresses, and dealership names.
Alon Gal is warning that Jira “has become a prime target for attackers due to its centrality in enterprise workflows and the wealth of data it houses” and this type of access can be used to “move laterally, escalate privileges, and extract sensitive information.”
As credentials collected by infostealers are easy to find and given that some of them remain unchanged for years as companies fail to include them in a regular rotation process, such attacks will likely become more frequent.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
