Maintaining updated systems and applications is a challenge for any IT team—especially considering the sheer volume of vulnerabilities organizations must find and prioritize on a rolling basis.
ThreatDown Vulnerability Assessment (VA), now included for free in every ThreatDown bundle, simplifies the vulnerability-finding process by automatically identifying gaps in your environment and prioritizing the results.
Based on the scans shared by the VA, ThreatDown Patch Management (PM), patches both the operating system and third-party applications installed on endpoints. But how exactly do both solutions work together?
In this article, we’ll dive into the inner workings of ThreatDown Vulnerability Assessment and how it integrates with Patch Management to seamlessly plug the holes in your cyber defenses.
1. Getting a lightweight start
Our journey with how Threat Down Vulnerability Assessment and Patch Management works begins as all great cybersecurity journeys begin: A clunky, on-prem server directly wired up to all your endpoints.
Just kidding. This isn’t the 1970s anymore. Thankfully.
The cornerstone of all ThreatDown security solutions—not just Vulnerability Assessment, but Endpoint Detection and Response (EDR) in general—is a lightweight endpoint agent (EA). The EA is a software tool which collects and sends endpoint security data to a central system for analysis and threat response
You can distribute the ThreatDown EA to endpoints either manually to each user or automatically via network-wide remote deployment tools.
2. Vulnerability Assessment scans endpoints
When you download the ThreatDown Endpoint Agent on your devices, it can then scan for installed third-party software and find out if there are any known vulnerabilities in them.
To enable a Vulnerability Assessment policy in Nebula, check out this simple step-by-step guide. There are two ways to scan for vulnerabilities: on-demand or scheduled.

3. VA finds vulnerabilities across third-party applications
The ThreatDown EA sends the results of the vulnerability scan to Nebula, our cloud-hosted security platform. Vulnerability data is stored and displayed for up to 90 days across all endpoints.
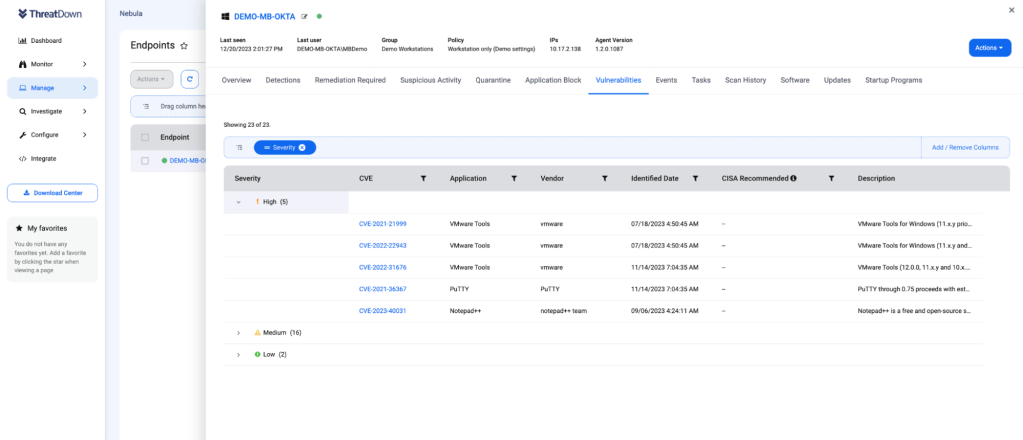
All vulnerabilities found are automatically assigned a severity rating based on the Common Vulnerability Scoring System (CVSS) standard. As well, vulnerabilities are tagged as “CISA recommended” if they are found in the Cybersecurity and Infrastructure Security Agency (CISA) managed catalog of known exploited vulnerabilities.
In Nebula, you have a few options for how you want to view found vulnerabilities:
Vulnerabilities page
On the left navigation menu, go to Monitor > Vulnerabilities to view vulnerabilities across your environment.

Endpoint page
On the Endpoints page, add a new column for a quick glance of the severity of CVEs for each endpoint. Hover over the diagram for a breakdown of vulnerabilities by severity.

Vulnerabilities tab
Navigate to the Vulnerabilities tab from Manage > Endpoints to view the vulnerabilities of a specific endpoint.
4. VA shares these findings with the Patch Management integration
Finding vulnerabilities, of course, is just one half of the battle.
After our free Vulnerability Assessment tool does its discovery work, our Patch Management module automatically imports the scan data and uses it to determine which patches and application updates need to be deployed.
With Patch Management, you can apply two different types of patches: operating system patches and software patches. To view and install both OS and software patches across your environment, navigate to Monitor > Patch Management on the left navigation menu.
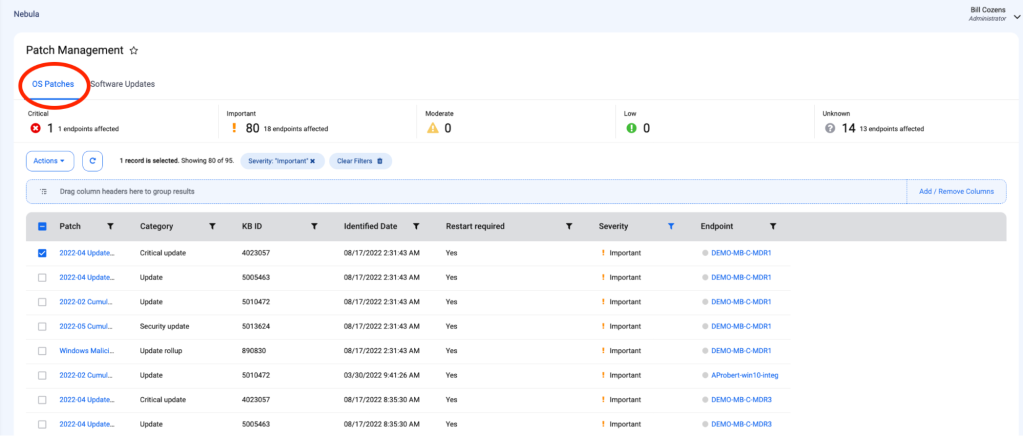
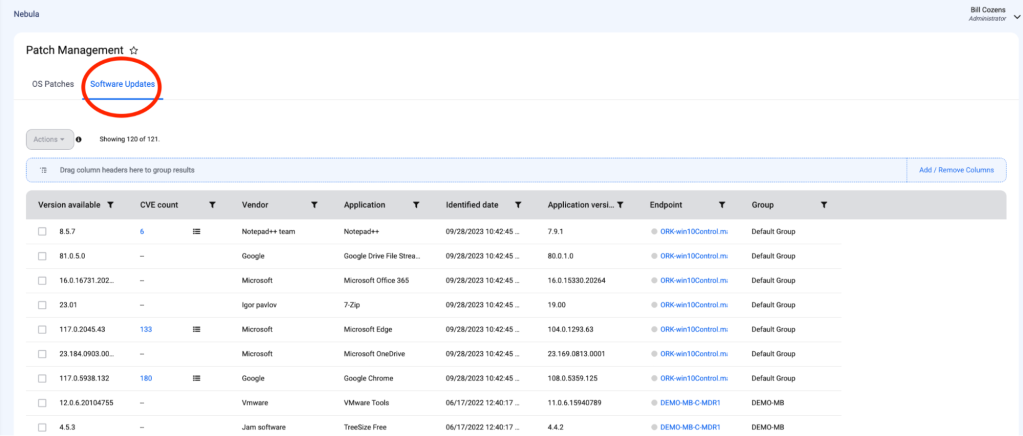
5. Patch Management automatically updates OS and third-party applications to the latest versions
To apply patches en masse, check the boxes for the systems or applications on endpoints you wish to update and click Actions > Update Software.
Bam, you’re done.

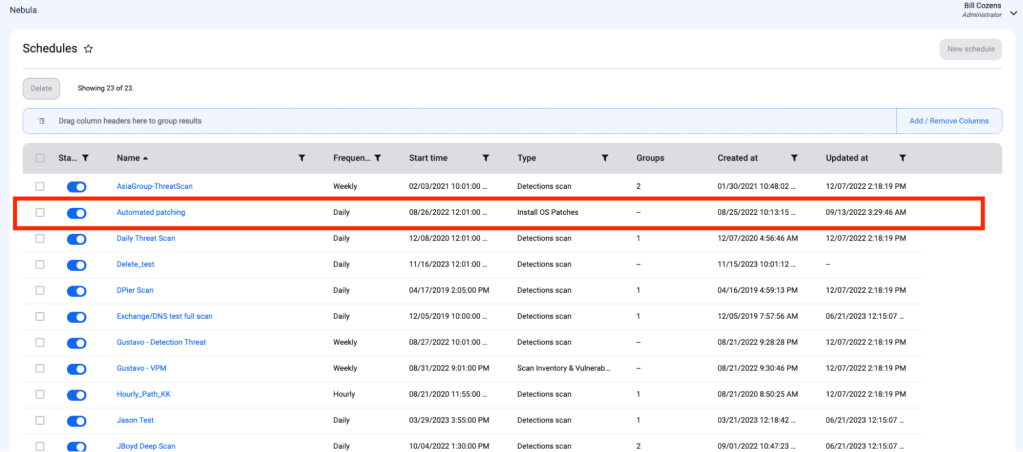
To help automate the patching process, you can create a schedule to install third-party software updates regularly. This schedule installs all system and third-party software updates found when the schedule is run.

Streamlining Vulnerability Response with ThreatDown
Managing vulnerabilities and patches yourself can be a pain. But, as we’ve broken down in this article, ThreatDown takes care of vulnerability management all from one console.
Learn more about our free Vulnerability Assessment solution here.
Interested in adding Patch Management capabilities as well? Check out ThreatDown Advanced, Elite, and Ultimate bundles.
Related:
How to choose a free vulnerability scanner: Insights from an industry veteran
How IT teams can conduct a vulnerability assessment for third-party applications
