The distinction between nation-state actors and organized cybercriminals is becoming increasingly blurred.
Both groups now leverage similar tactics, techniques, and procedures (TTP) in their cyber operations, resulting in a complex landscape where motivations and objectives often intersect.
This article delves into the intricate dynamics between these two types of cyber operatives, examining their methods, motivations, and implications for global cybersecurity.
Nation-State Actors
Historically, nation-state actors have engaged in cyber operations primarily to achieve geopolitical objectives. Groups like Russia’s APT28 and China’s APT10 have targeted governmental and critical infrastructure networks to gather intelligence and disrupt rivals.
Their operations are characterized by sophistication and a strategic focus on long-term disruptions that align with national interests.
In recent years, Chinese cyber groups such as Volt Typhoon have intensified campaigns against U.S. critical infrastructure, utilizing stealth tactics to infiltrate sectors crucial to national security, reported by Trellix.
Similarly, Russian actors like APT29 (Cozy Bear) have conducted high-profile espionage, demonstrating the continuity of state-sponsored cyber operations even amidst global tensions.
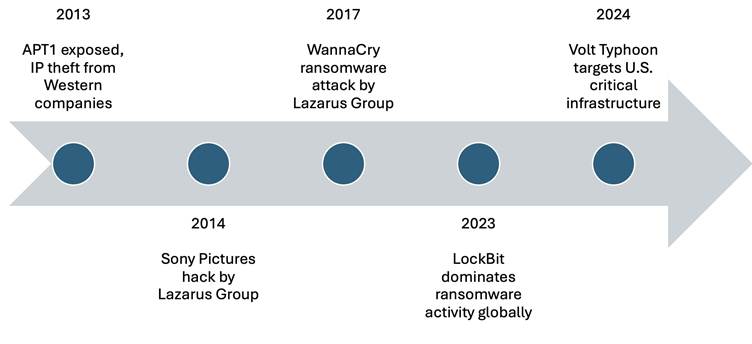
Iranian groups like APT33 are also noteworthy, leveraging cyber capabilities to target vital industries and disrupt U.S. political processes, particularly during election cycles.
North Korea’s infamous Lazarus Group exemplifies a hybrid model, merging traditional espionage with high-stakes financial theft through operations such as the Sony Pictures hack and the WannaCry ransomware attack.
Organized Cybercriminals
In contrast, organized cybercriminals have typically focused on financial gain. Groups like REvil and DarkSide have exploited vulnerabilities for extortion and theft, targeting businesses and individuals alike.
The rise of Ransomware-as-a-Service (RaaS) has enabled these groups to scale operations, resulting in significant financial gains and disruptions across various sectors.
The emergence of new ransomware groups continues to reflect the adaptability and evolution of organized cybercrime.
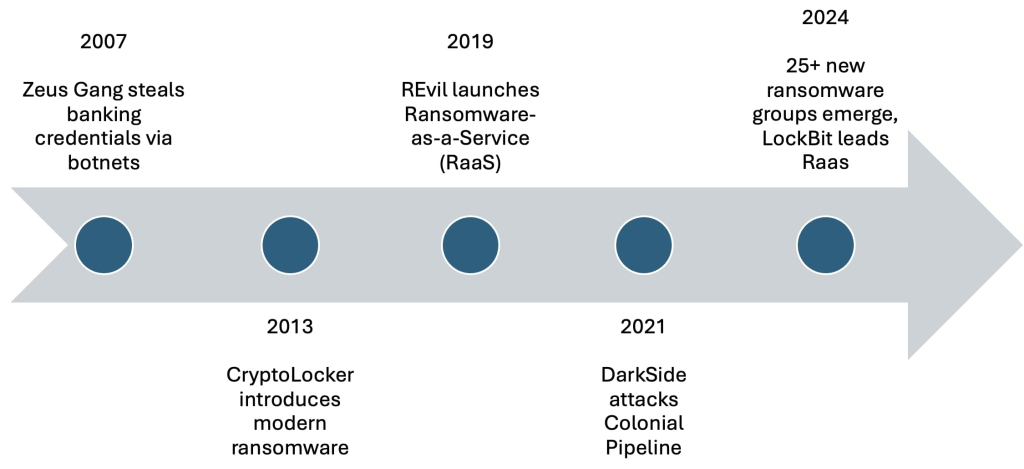

For instance, the BianLian group has shifted tactics to maximize payouts, showcasing the ongoing innovation within cybercriminal networks.
As these groups grow more sophisticated, they are also adapting techniques traditionally reserved for state actors, such as prolonged network infiltrations and supply chain attacks.
Here’s a detailed table outlining the Key Differences between nation-state actors and organized cybercriminals based on their diverging motivations and objectives:
The convergence of nation-state tactics with organized cybercriminal methods presents unique challenges. Nation-states are increasingly adopting financially motivated strategies, utilizing ransomware not just for disruption but also as a revenue stream.
North Korea’s collaboration with cybercrime groups to fund its operations underscores this trend, as does the rising complexity of organized cybercriminal campaigns that mimic APT-like behaviors.
Moreover, the integration of artificial intelligence (AI) into both domains complicates the threat landscape.
AI tools are employed to enhance the effectiveness of attacks, automate processes, and generate sophisticated phishing campaigns, further blurring the lines between state-directed and financially motivated cyber activities.
Shared Techniques and Challenges of Attribution
| Aspect | Nation-State Actors | Organized Cybercrime |
| Motivations | Geopolitical objectives: espionage, political disruption, military advantage | Financial gain: extortion, theft, fraud, monetization of stolen data |
| Objectives | Long-term intelligence gathering, disruption of geopolitical rivals, achieving strategic goals | Short-term monetary returns, maximizing profit through quick attacks |
| Targeting | High-value targets (government entities, military, critical infrastructure) | Broad industries (healthcare, retail, finance), targeting weak defenses |
| Resources/Skill Levels | Backed by state resources; access to advanced tools and custom intelligence assets | Rely on commercially available tools; often less sophisticated than state actors |
| Operational Complexity | Complex, coordinated operations involving custom-built malware; long-term infiltration | Often opportunistic; uses Ransomware-as-a-Service (RaaS) models |
| Attack Vectors | Phishing, supply chain attacks, watering hole attacks, zero-day exploits | Phishing, brute force, social engineering, exploit kits |
| Evasion Techniques | Advanced evasion tactics (fileless malware, rootkits, custom obfuscation) | May use off-the-shelf evasion tools, but also fileless malware |
| Command and Control (C2) | Uses encrypted channels, Tor, custom infrastructure for stealth | Utilizes cloud services for anonymity, encrypted channels |
| Collaboration | May collaborate with cybercriminals for mutual benefit | Increasingly mimicking state tactics to enhance effectiveness |
| Geopolitical Implications | Actions may have significant geopolitical impact, aligning with national interests | Primarily focused on financial outcomes; less concern for political ramifications |
Both nation-state actors and cybercriminals utilize similar tools and techniques, such as phishing, supply chain attacks, and fileless malware.
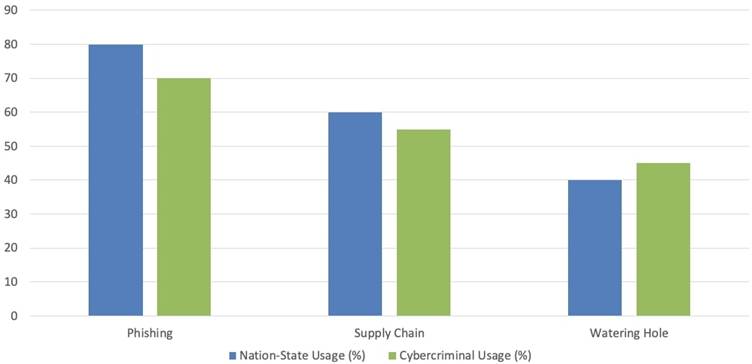

This overlap complicates attribution, making it increasingly difficult to pinpoint the origin of an attack. False flag operations, where attackers mislead investigators about their identity or motive, further obscure responsibility.
Shared command-and-control (C2) infrastructures, including cloud services and Tor networks, complicate analysis and response efforts. As both categories of attackers use encrypted channels, defenders must adapt to a landscape where threat actors increasingly appear indistinguishable from one another.
The landscape of cyber threats is evolving rapidly, challenging the traditional definitions of nation-state actors and organized cyber criminals.
Their convergence necessitates a transformation in cybersecurity strategies, aimed at fostering resilience against an increasingly complex and interwoven threat environment.
As these malicious entities adapt and collaborate, the international community must come together to bolster defenses and protect critical infrastructures from the devastating impacts of cyber warfare.
ANY.RUN Threat Intelligence Lookup - Extract Millions of IOC's for Interactive Malware Analysis: Try for Free
