When your alert queue seems endless, it might feel like threat intelligence is more of a curse than a blessing. But taking the right approach to it will help increase detection rates without stretching resources thin.
Top-performing SOC analysts don’t necessarily go through more alerts than others; they simply know where to look for reliable data. That’s what allows them to achieve higher results without the need to overwork. They go another way, and so can you.
What Causes Alert Overload in the First Place
It’s a myth that more data equals better efficiency. Thousands of alerts, most of which are false positives, lack of context for prioritization of incidents, and too much manual work: this is a common struggle for many SOCs.
The overwhelm of Tier 1 analysts leads to alert fatigue, as well as unnecessary escalations. The entire team experiences its negative effects: missed alerts, slower MTTR, and burnout across the board.
To sidestep these challenges, you need a source of intel that works in your favor. It makes all the difference and helps skyrocket detection rates with lesser load.
What to Look for in Threat Intelligence Sources
Threat intelligence sources that stand out are:
They might provide less data, but if this is the result of filtering, it’s a huge pro, not a con. Fewer false positives mean less work and better focus on real threats.
Look for feeds that provide indicators coming from the very core of malicious configurations rather than from third-party sources. This, once again, guarantees that you get reliable information, not outdated and irrelevant info.
Not all threat intelligence is made equal. While most feeds provide just a collection of feeds, others feature threat context, which helps accelerate triage by providing a deeper visibility into threats.
Delayed alerts are practically useless. The less time it takes for an indicator to make it to the feed, the better. Solutions with real-time updates should be your go-to if you want to stay on top of things.
Analysts Stay Ahead with ANY.RUN Threat Intelligence Feeds
There aren’t many threat intelligence feeds that fit these requirements. Accurate and fresh data with little to no false positives isn’t easy to obtain: it requires access to unique threat data.
ANY.RUN’s Threat Intelligence Feeds are powered by a global network of 15K SOC teams and 500K malware analysts who continuously provide live attack data, which then gets filtered and delivered to users’ systems. This means that every indicator is backed by an actual threat investigation, giving you confidence and real-world insights.
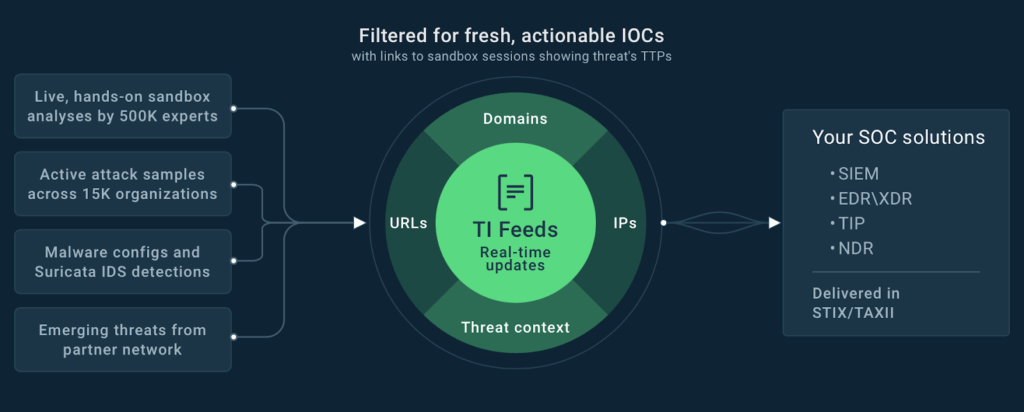
TI Feeds by ANY.RUN keep your systems up-to-date with exclusive IOCs in real time
Detect more threats with less noise and tap into live malware analysis data -> Try TI Feeds in our SOC
The results TI Feeds users see:
- Decreased workload: Indicators from TI Feeds enrich your SIEM, EDR/XDR, and other systems for a smoother workflow. As a result, the case load for Tier 1 analysts lowers by 20%.
- Wider coverage: 99% of IOCs in TI Feeds are unique and can’t be found elsewhere, so you automatically extend your monitoring range.
- Constant updates: No more missed threats and false alerts caused by outdated indicators.
- Actionability: High-confidence threat intelligence fueled with context gives you a hand in classifying and prioritizing alerts for targeted action.
Conclusion
Analysts increase their detection rates using validated intelligence that enriches their system in real time, shortly after a threat emerges. TI Feeds with wide coverage and deep context supplied by reliable sources give SOC teams an upper hand in triage and cut their workload for better overall efficiency.
