Today, HackerOne is launching the industry’s first hacker API. This release is now out of beta and is available to the hacker community. It includes a collection of API endpoints that help automate common workflow tasks. In the past, hackers had to use the UI to complete repetitive tasks on the platform, with no supported mechanism to script or automate their workflows. With the new API, hackers can increase productivity and allocate more time towards creative bug hunting.
With the new hacker-facing set of API endpoints, you can integrate common HackerOne platform features into your regular workflows, including your listing programs, determining assets in scope, creating reports, viewing report status, and listing your earnings and payouts. You can also automate repetitive manual tasks, such as submitting reports through the UI or checking for updated status changes on reports.
We provide new API endpoints that help hackers to do the following:
- Access Program Information
- Hackers have an easy way to get information on all accessible public and private programs. You can query all assets in scope to integrate with your tools.
- Manage Report Lifecycle
- Ability to access all vulnerabilities you submitted and see the latest updates on the reports. Easily submit a new vulnerability through the API from your favorite tools.
- Monitor Earnings and Payouts
- Make your tax reporting more manageable than ever with complete visibility into your bounty earnings and payouts.
For complete documentation, click here.
How to Access the Hacker API
Use personal API tokens to authenticate with the API. If you are logged on the HackerOne platform you can generate and manage API Tokens from your API settings page. Use your username and token as the username and password for authentication. These must be sent in the Authorization header for every request as shown in Figure 1 below.
See the Hacker API in Action
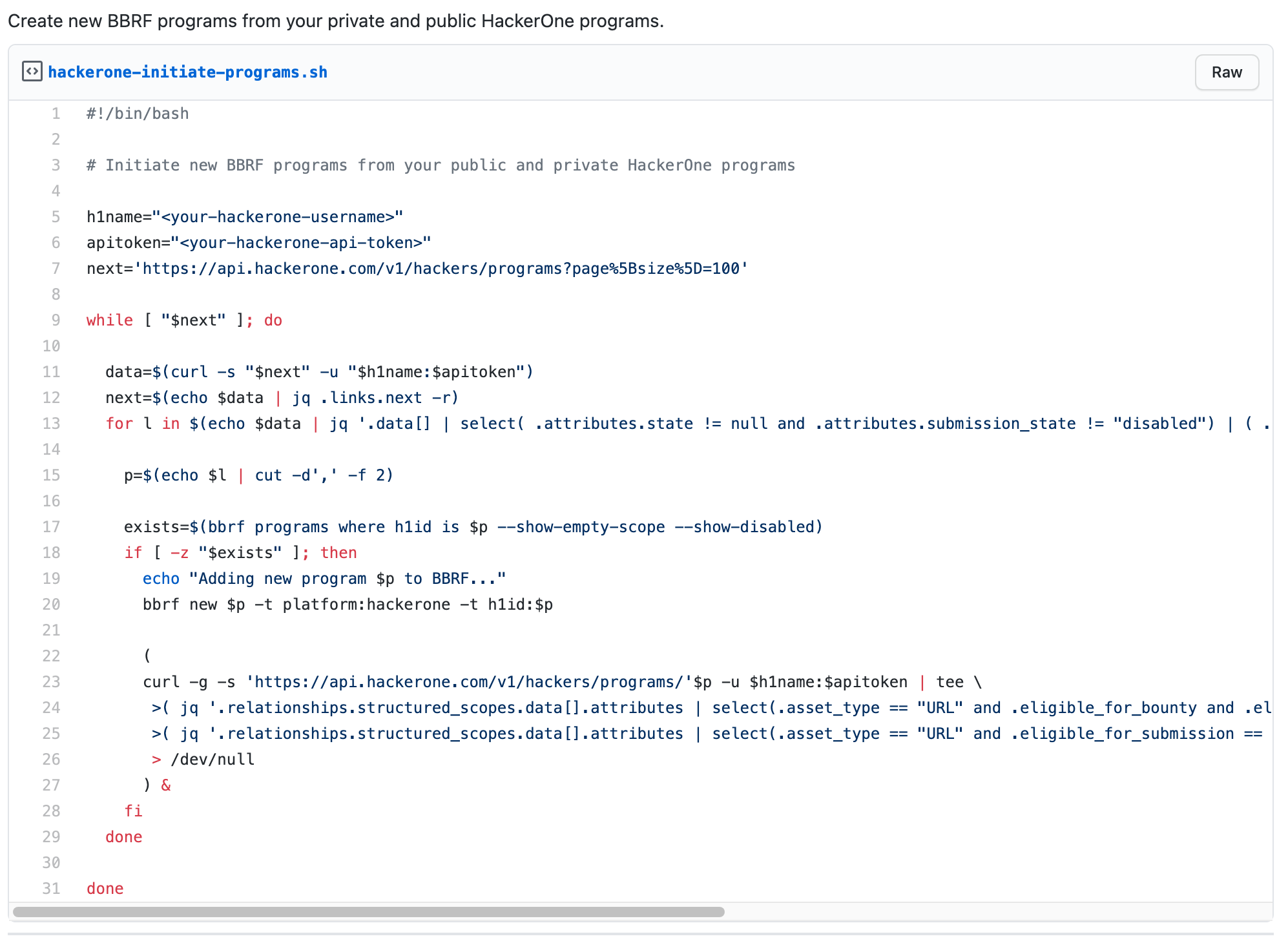
Use Case #1: Hackers Pieter (Honoki) and ManoeIT created an integration from the HackerOne API with their reconnaissance tool Bug Bounty Reconnaissance Framework (BBRF) to automatically import new assets from HackerOne, as seen in Figure 2 below.
According to Pieter: “HackerOne is the first platform that allows me to automatically ingest new programs and scope changes into my BBRF reconnaissance flows. With two daily automated tasks, all my public and private programs get pulled into BBRF, along with their scope definition and all overnight scope changes that a program might have made. I get to spend more time looking for bugs and less time managing my datasets.”
Use Case #2: Hacker Dominic Couture (Dee-see) used the HackerOne API to fetch all bounties he had earned in the current year and calculated the total to use when filing his taxes.
He says: “With the fun of bug bounties comes the pain of taxes! In the past, to get the end-of-year numbers, we had to go to the payments page, request an email with a CSV file, and then calculate the relevant numbers. I wrote a small Ruby script with the API, and I now get the total in a single operation. I saved time, and anything to make the tax filing process more pleasant is a win!”
HackerOne’s new set of API endpoints saves time. It increases hacker job satisfaction by automating regular tasks, freeing them up to bug hunt rather than continually track datasets and perform other manual tasks. By allowing hackers to integrate their workflows with the HackerOne platform easily, the API lets hackers do more productive and creative hacking, benefiting both the HackerOne community and our customers. Here’s how to get started with the HackerOne API.