ANY.RUN, an interactive malware sandbox, has published a comprehensive analysis of the growing threat that crypto-malware poses in a time when it is more important than ever to have strong digital security.
This malicious software, designed to covertly mine cryptocurrency using infected devices’ processing power, represents a significant shift in the cyber threat landscape.
Let’s have a detailed look at crypto-malware, its various forms, and how its platform can be leveraged to analyze and combat this insidious threat.
ANY.RUN is a cloud-based environment for analyzing Windows malware and Linux-based samples. Malware analysts, SOC, DFIR teams can safely examine threats, simulate different scenarios, and gain insights into malware behavior to improve cybersecurity strategies.
ANY.RUN also allows researchers to understand malware behavior, collect IOCs, and easily map malicious actions to TTPs—all in our interactive sandbox.
The Threat Intelligence Lookup platform helps security researchers find relevant threat data from sandbox tasks of ANY.RUN.
What is Cryptomining Malware?
Cryptomining malware, or cryptojacking, hijacks a target’s computing resources to mine cryptocurrencies like Bitcoin. This malware performs complex mathematical calculations to verify cryptocurrency transactions, requiring significant CPU and sometimes GPU power.
Unlike legitimate mining operations, the rewards of this illicit activity go to the attackers, leaving device owners with degraded system performance and increased electricity bills.
Examples of Cryptomining Malware
The landscape of cryptomining malware is diverse, with various methods employed to infect target computers. These range from code embedded in websites to classic email phishing attacks. Once in place, the malware operates in the background, making detection challenging.
High-profile examples of crypto-jacking include the Mirai botnet, which has been adapted for crypto-mining purposes, showcasing the adaptability and persistence of cybercriminals in exploiting digital resources for financial gain.
Cybersecurity experts from ANY.RUN’s report noted a rise in the use of crypto mining malware, with XMRig and DarkGate being two prominent examples of this malicious software’s repurposing by cyber criminals. This is a worrying development for digital security.
XMRig
XMRig, initially an open-source CPU mining software intended for the cryptocurrency Monero (XMR), has been hijacked and embedded within the malware.
The altered version of XMRig is designed to stealthily adjust its mining intensity based on the system’s CPU usage. This cunning adaptation allows it to evade detection, as it avoids the usual symptoms of high resource consumption that might alert users to its presence.
DarkGate
Meanwhile, DarkGate, a multifaceted malware loader, has been found to execute crypto-mining payloads, including the compromised version of XMRig.
DarkGate is insidious due to its ability to gain system-level privileges on infected machines. It employs rootkit-like features to maintain persistence, making it challenging to remove.
Techniques used by DarkGate to ensure its continued operation include initiating from an LNK file in the Windows Startup folder, altering registry keys to run in tandem with the LNK file, or using a DLL file, varying with its configuration settings.
Analyzing Crypto Malware in ANY.RUN
ANY.RUN offers a cutting-edge solution for analyzing crypto malware through interactive malware sandboxes. This technology allows for the detailed examination of suspicious files, which spam filters can automatically submit for analysis.
In a recent technical analysis, ANY.RUN successfully identified a crypto miner using its advanced detection capabilities, highlighting the effectiveness of its platform in combating the rising threat of crypto-malware.
The detection was primarily based on the miner’s network activity, which allowed ANY.RUN to bypass manual investigation processes and directly proceed to collect Indicators of Compromise (IOCs).
The crypto miner, once activated, exhibited unmistakable signs of malicious activity. Notably, the system’s CPU usage spiked to its maximum after startup, along with a significant increase in RAM utilization.
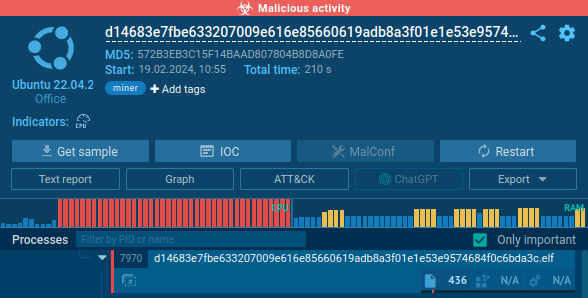
Such abnormal behavior indicates a system being compromised, especially when paired with the miner’s excessive network activity.
In an incredible display of network exploitation, the miner sent almost 300,000 DNS requests to generate domain names in less than four minutes. This level of network activity is highly unusual and far exceeds the bounds of legitimate software operations, further confirming the malicious nature of the entity.
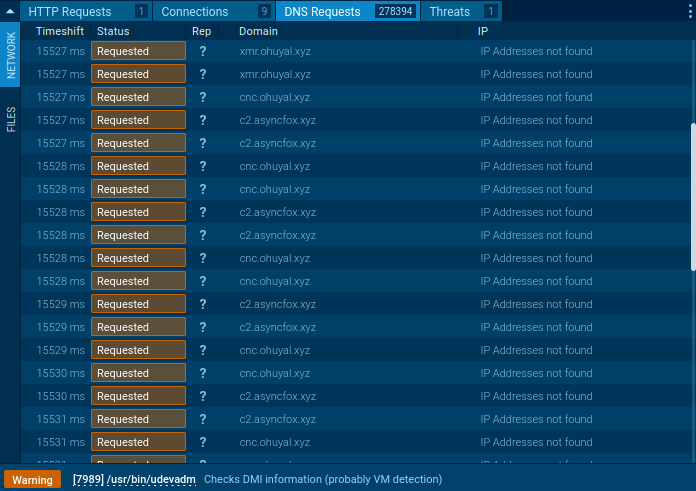
ANY.RUN’s thorough analysis established the existence of a crypto miner and made it possible to gather crucial IOCs quickly. These indicators are vital for configuring Security Information and Event Management (SIEM) and Web Application Firewall (WAF) systems to protect against this threat.
ANY.RUN’s ability to detect and analyze crypto malware with such precision underscores the importance of advanced cybersecurity solutions in today’s digital landscape.
As crypto malware continues to evolve, platforms like ANY.RUN are essential for identifying and mitigating these silent yet significant threats, safeguarding digital assets and maintaining system integrity.
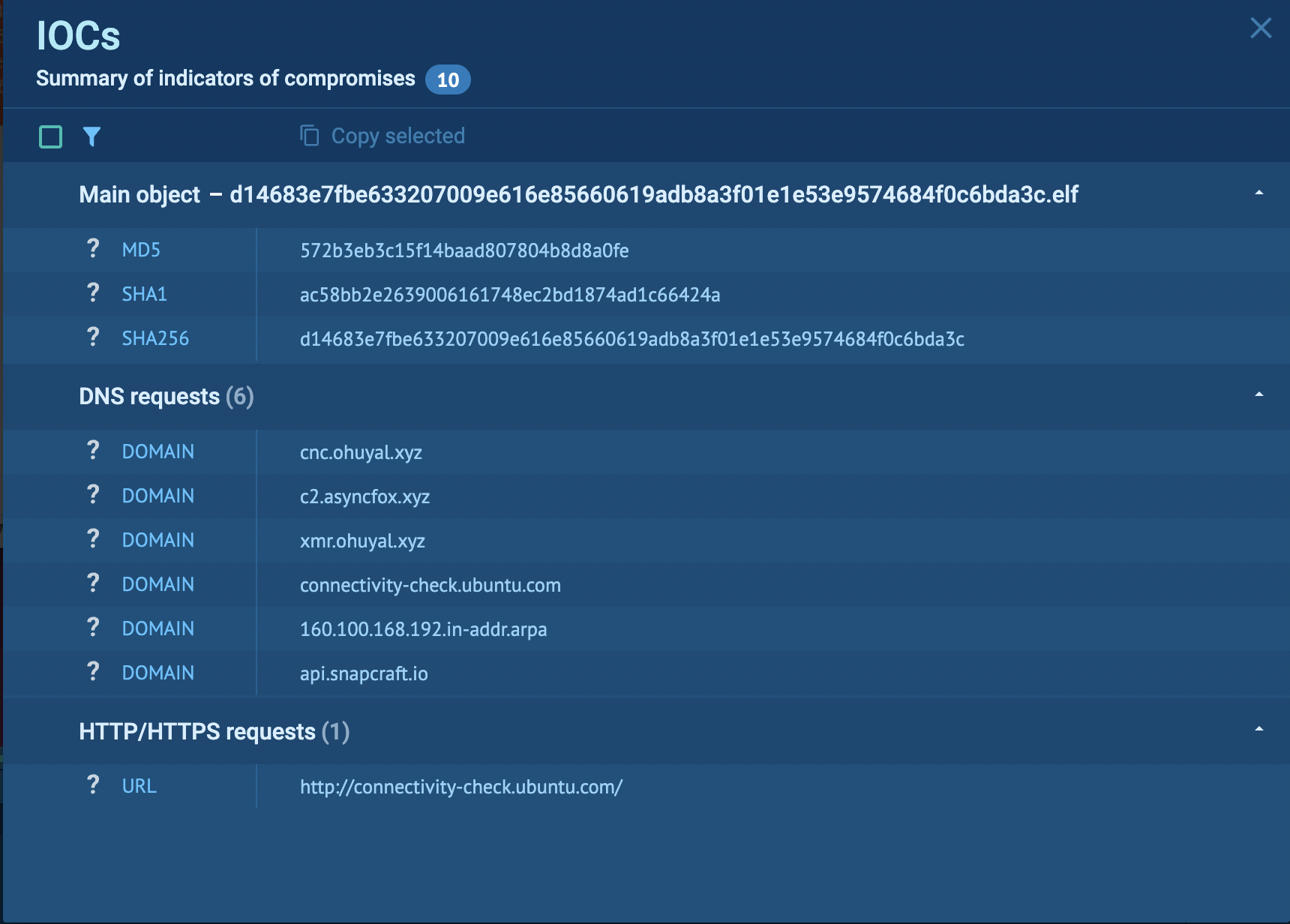
Users can manually analyze these files or send samples directly via API. By analyzing sandbox reports, users can collect Indicators of Compromise (IOCs) and configure their security systems to fend off crypto malware attacks effectively.
Prevention
To safeguard against crypto-malware, ANY.RUN recommends a combination of vigilance and adherence to cybersecurity best practices. This includes exercising caution when downloading software and visiting websites, keeping systems updated, and employing reputable antivirus solutions.
Monitoring for unusual spikes in CPU usage can also serve as an early warning sign of infection, enabling users to take swift action to mitigate potential damage.
Prevent Crypto-Malware Attacks
EDR system configuration: EDR can warn you of unusual CPU/GPU and memory utilization by non-standard programs.
Also out for odd process executions, especially those connecting to recognized crypto mining pool addresses.
Make use of the Threat Intelligence lookup. Use real-time threat information to update TIP and SIEM systems with crypto-malware indications (IPs, domains, and file hashes).
Set up email filters. Block executable, script, and macro-filled email attachments. Send questionable files for manual review automatically.
Analyze samples with Interactive Malware Sandboxes like ANY.RUN. Automatically send suspected spam filter-detected files to ANY.RUN for comprehensive analysis by API or ticket. Analyze sandbox reports for IOCs and security system configuration.
Who is ANY.RUN?
As the digital world continues to evolve, the threat of crypto-malware looms larger, making the insights and tools provided by ANY.RUN is more essential than ever.
Through their comprehensive analysis and innovative sandbox technology, ANY.RUN empowers users to understand and defend against crypto-malware’s silent but significant threat.
For further information on ANY.RUN’s analysis of crypto-malware and how their platform can assist in combating this threat, you can get access to ANY.RUN sandbox platform for free.
If you’re from the SOC and DFIR teams to investigate incidents and streamline threat analysis. Try all features of ANY.RUN at zero cost for 14 days with a free trial.
