Phishing kits are evolving fast. Threat actors behind toolkits like Tycoon2FA, EvilProxy, and Sneaky2FA are getting smarter, setting up infrastructure that bypasses 2FA and mimics trusted platforms like Microsoft 365 and Cloudflare to steal user credentials without raising red flags.
But if you’re part of a SOC or threat intel team, you don’t have to sit back and wait for alerts.
There’s a faster, more proactive way to uncover and block these attacks before they slip through the cracks.
The Fastest Way To Uncover Emerging Phishing Campaigns
Solutions like Threat Intelligence Lookup give you instant access to a massive pool of indicators such as files, URLs, domains, and behaviors, extracted from live analyses of malware and phishing samples performed by analysts across 15,000 companies worldwide inside ANY.RUN’s Interactive Sandbox.
You can search across fresh IOCs, IOBs, and IOAs, monitor campaigns’ activity, extract artifacts, and feed them directly into your detection stack.
Let’s take a look at how this works in practice:
Tycoon2FA: Find Active Phishing Campaigns in the Wild
Let’s say you want to track real-world sandbox sessions involving Tycoon2FA; phishing kit designed to steal Microsoft credentials and bypass two-factor authentication.
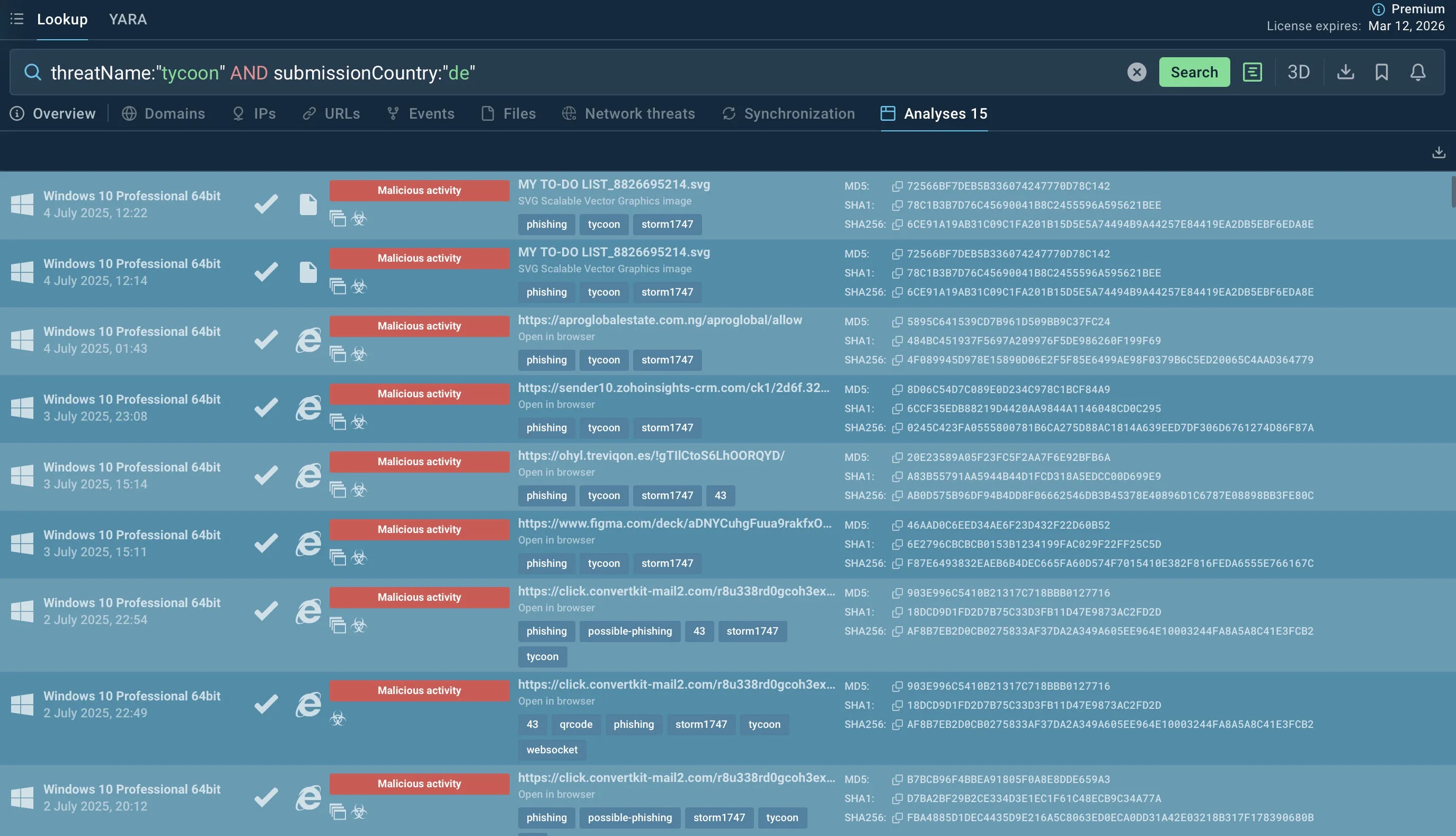
We are specifically interested in how it’s targeting users in Germany, here’s a quick query we can run in Threat Intelligence Lookup:
threatName:”tycoon” AND submissionCountry:”de”
Let’s set the search period to the past 3 days (you’ll find that filter right next to the search button).
.webp)
Within seconds, Lookup returns sandbox sessions where Tycoon2FA samples were analyzed by users in Germany.
.webp)
You can explore these analyses to observe the entire attack. Below is a screenshot of one of the sessions found in the results:
View Tycoon2FA sandbox session
.webp)
This kind of visibility helps analysts respond faster and with more confidence, using real-world attack data, not just generic threat signatures.
You can also download a JSON file with all session links, extracted URLs, and file hashes.
It’s a simple way to gather actionable indicators and enrich your detection rules or block lists before these threats even land in your environment.
Give your team the intel it needs to catch threats before they become incidents -> Get 50 trial requests in TI Lookup EvilProxy: Surface Malicious Domains In Seconds
EvilProxy is known for abusing legitimate cloud services to host phishing infrastructure, making its campaigns harder to spot using traditional detection methods.
One common tactic involves leveraging Cloudflare Workers to create large numbers of subdomains.
To track these campaigns, run the following query in Threat Intelligence Lookup:
domainName:”.workers.dev” AND threatLevel:”malicious”
This query targets a known pattern in EvilProxy campaigns; abuse of .workers.dev for hosting phishing pages.
After running the search, go to the Domains tab to see a list of domains extracted from sandbox sessions. Many of these are tied directly to EvilProxy samples:

Having access to up-to-date infrastructure indicators like these helps your team block threats earlier, refine detection rules, and reduce manual analysis time, especially when those domains are already being used in active attacks.
Sneaky2FA: Catch Reused Elements Across Campaigns
While attackers constantly change domains, IPs, and file names to avoid detection, some artifacts tend to stay the same across campaigns involving phishing kits.
These can include things like favicon images, login page templates, JavaScript snippets, or brand assets like logos.
That’s because assets provided by phishing kits are often reused or only lightly customized between campaigns.
Rebuilding an entire kit takes time, so threat actors frequently copy and paste elements from one target to the next. This consistency gives defenders a small but critical window of opportunity.
For instance, Sneaky2FA regularly uses spoofed Microsoft 365 login pages, and one of the assets it often includes is the same Microsoft logo.
By searching for the SHA-256 hash of that logo in Threat Intelligence Lookup, you can uncover fresh phishing samples tied to this kit:
sha256:”5d91563b6acd54468ae282083cf9ee3d2c9b2daa45a8de9cb661c2195b9f6cbf
Even if the attacker rotates the domain or obfuscates parts of the page, static artifacts like this logo often remain untouched.
That makes them valuable indicators for identifying ongoing campaigns that may otherwise slip through traditional network detection.
.webp)
This approach helps you catch phishing activity that’s been dressed up to look new but is really just the same kit underneath. It’s a simple way to stay one step ahead of attackers who reuse what works.
Strengthen Detection with Real-World Phishing Intelligence
Phishing kits like Tycoon2FA, EvilProxy, and Sneaky2FA evolve fast but their traces are visible if you know where to look.
With ANY.RUN’s Threat Intelligence Lookup, your team can move from reactive to proactive: uncovering fresh indicators, tracking attacker infrastructure, and identifying reused assets before they hit your environment.
- Earlier threat detection and faster containment reduce the risk of breaches and limit potential damage
- Stronger protection based on real-world data improves overall security posture across the organization
- Faster response times help minimize operational disruption and lower incident-handling costs
- Higher detection accuracy reduces missed threats and improves SOC efficiency
Get 50 trial requests in TI Lookup and turn scattered indicators into actionable intel! 