For years, microsegmentation has carried a reputation for being too complex, too manual, or too advanced for most organizations. In fairness, legacy microsegmentation solutions earned that estimation by consistently over-promising and under-delivering, proving slow to deploy, difficult to configure, and equally painful to scale.
But times – and technology – have changed; one of the most influential voices in cybersecurity recently weighed in to confirm that microsegmentation is essential for bolstering cyber defenses, and it’s no longer reserved for only the most mature and well-resourced enterprises.
CISA’s latest guidance, Microsegmentation in Zero Trust Part One: Introduction and Planning, validates that microsegmentation is not a nice-to-have or an advanced-stage optimization, it’s a foundational pillar of Zero Trust security that every organization can and should adopt – the only question is: how?
A Turning Point: Microsegmentation Is Foundational, Not Optional
CISA has long acknowledged the critical role of microsegmentation for achieving true Zero Trust security, but its Zero Trust Maturity Model, first released in 2021, placed microsegmentation at the framework’s pinnacle – a treacherous peak atop a symbolic snowcapped mountain, marked by a red flag that reads more like a warning label than a finish line.
The agency’s latest guidance marks a clear departure from legacy thinking, confirming microsegmentation is no longer relegated to the end of a daunting journey or reserved for “advanced” organizations.
This new perspective from CISA underscores a broader shift. Exactitude Consultancy now estimates that the global microsegmentation market will reach a value of $41.24 billion by 2034 – a fivefold increase – as more frequent and sophisticated cyberattacks plus increasingly complex hybrid networks fuel demand, leading to “the rising popularity of microsegmentation as a core cybersecurity strategy.”
Further evidence of this turning point in action, new research from Enterprise Management Associates (EMA) found that 96% of IT and security leaders consider microsegmentation extremely or very important for cyber defense.
Respondents cited the ability to instantly quarantine and contain threats, halting lateral movement and thwarting ransomware, and meeting compliance and cyber insurance requirements as the most valuable microsegmentation benefits – a sign that organizations are shifting focus toward rapid incident response and limited the blast radius of attacks.
So, it’s clear that cyber authorities and security teams alike recognize the urgent need to adopt microsegmentation and prioritize containment; the challenge – as always – comes down to execution.
Outlearn, outsegment, and outdefend the competition on Containment Island, a four-week gamified webinar series with a grand prize trip to the Four Seasons Bahamas.
Join practical sessions with industry experts, compete in challenges, and climb the leaderboard in this cyber version of Survivor.
Register Now
Traditional Barriers to Segmentation Success Remain Relevant
Though security teams overwhelmingly recognize microsegmentation’s value, just 5% are microsegmenting their networks today. What’s driving the disconnect? Implementation complexity, operational disruptions, legacy application headaches, and costly rollouts are some of the top-reported concerns from IT and security leaders in ViB Tech’s report on the role of network segmentation in Zero Trust architectures.
In a bid to bridge the gap, CISA offers a step-by-step roadmap for implementation in its release, advising a phased approach that largely aligns with legacy solutions’ capabilities: identify resources, map dependencies, determine policies, then deploy and iterate.
Though this sounds simple, it’s not a one-and-done initiative – the same process must be repeated continuously as organizations secure (at most) a few apps at a time.
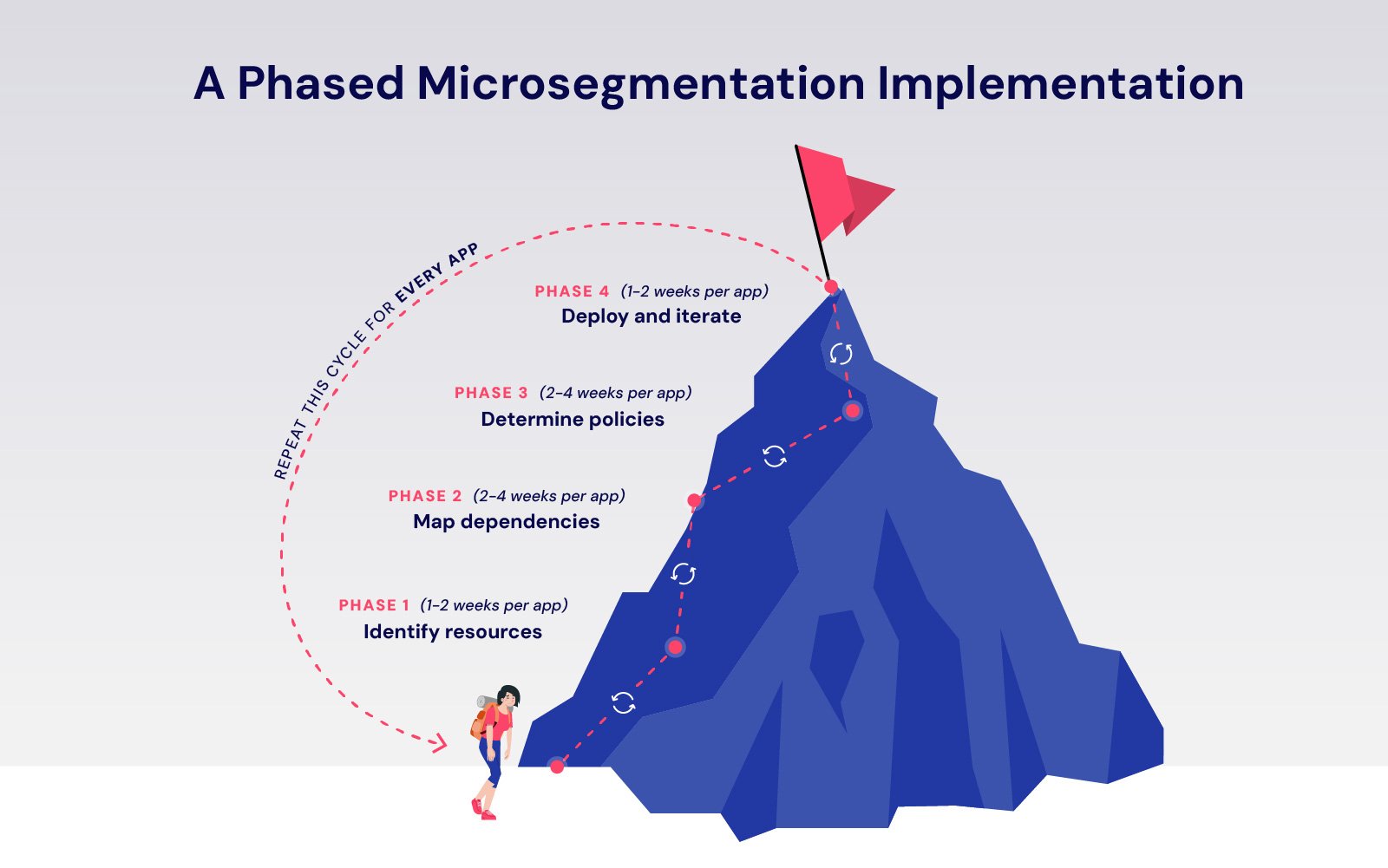
Importantly, the milestones outlined in CISA’s roadmap aren’t wrong, but this linear, manual tactic leaves organizations to grapple with the same barriers that have traditionally caused microsegmentation projects to stall or fail outright, putting security teams back at square one.
Fortunately, modern microsegmentation solutions open a path to step off the implementation hamster wheel and fast-forward through CISA’s phases, unlocking comprehensive segmentation in a fraction of the time – but what exactly defines “modern” microsegmentation?
Microsegmentation Made Easy: Defining Capabilities and Their Real-World Impact
To understand the key capabilities closing the gulf between microsegmentation’s promise and practical value, we only need to take a closer look at recent industry insights.
CISA’s release highlights the need for segmentation policies that evolve dynamically, using contextual data such as identity, device posture, behavioral indicators, and more – all of which enable adaptive policies.
Meanwhile, EMA’s research tells us what security teams are looking for as they consider innovative solutions in the next 1-2 years: automated policy creation and lifecycle management, automated asset discovery and asset tagging, and MFA integration top the list of must-haves.
These answers echo ViB Tech survey findings, where respondents said MFA overlay, automated policy creation, and agentless deployment were the most important capabilities for a microsegmentation solution.
Zero Networks is the only microsegmentation solution that delivers all the attributes of a truly modern approach — agentless, automated, identity-aware, and MFA-powered.
In practice, these capabilities eliminate the hurdles that typically stall microsegmentation. An agentless deployment means seamless integration with existing infrastructure, no need to coordinate across thousands of endpoints or disrupt typical network usage patterns.
Automation removes manual tagging, grouping, and policy creation from the equation. Layered identity controls, including just-in-time MFA, scale protection to privileged access, closing the security gaps left by legacy solutions.
The result? Security leaders can stop approaching microsegmentation implementation as a necessarily stilted, cyclical process and instead achieve comprehensive protection in one fluid motion while reducing manual effort and operational complexity – not adding more.
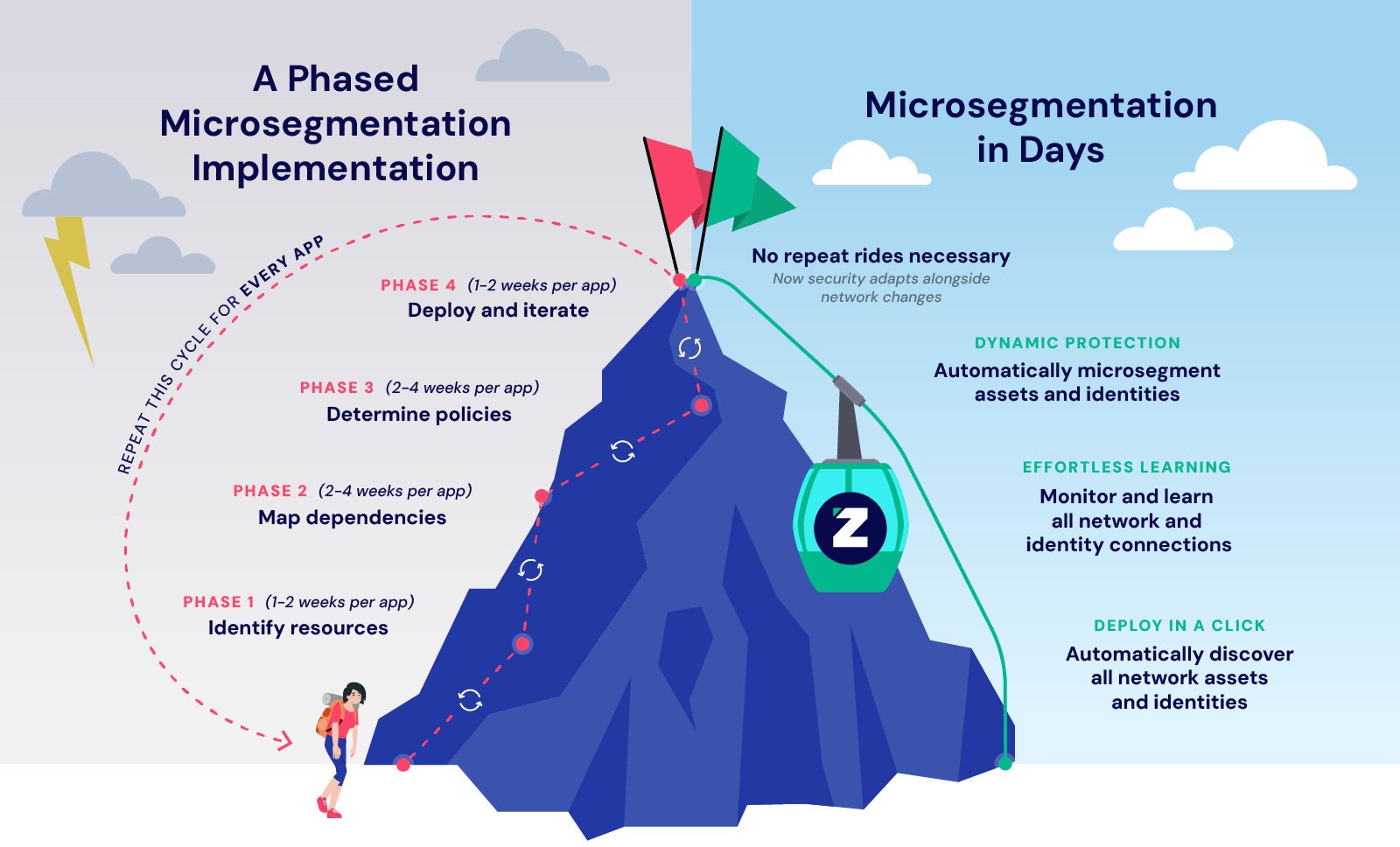
Importantly, the same features that accelerate deployment can dynamically adapt policies, translating to significantly less manual work in both the short and long term.
For example, in a technical validation report, analyst group ESG found that Zero Networks cuts costs by 87% for the average enterprise when compared with traditional segmentation, due primarily to the effortless maintenance and management enabled by Zero’s robust automation engine.
Containment Is Key
After years of over-relying on detection while deprioritizing prevention, defenders are shifting focus: containment must take center stage. CISA is right to affirm microsegmentation as foundational to Zero Trust, but its roadmap still leans on legacy methods that make the path to built-in containment feel inevitably slow and complex.
Modern approaches prove that doesn’t have to be the case. Now, microsegmentation aligned to industry-leading Zero Trust guidance isn’t just aspirational, it’s practical for every organization.
It’s time to question the order of operations imposed by legacy solutions.
Today, fortifying and future-proofing your defenses should feel more like a gondola ride than a trek to the top of a mountain.
Join Zero’s Containment Island webinar series for a deeper dive into how you can achieve real-time containment without added complexity.
Sponsored and written by Zero Networks.





