HackerOne and PagerDuty have partnered to create a workflow automation integration that feeds critical and high severity vulnerability findings into PagerDuty alerts to notify security teams and take timely action immediately.
How Does the Integration Work?
- When a new high or critical severity report is submitted and triaged in HackerOne, the integration automates the creation of PagerDuty alerts.
- You can customize the integration to support your workflow and security operations needs.
- It is easy to set up via familiar UIs.
HackerOne finds vulnerabilities, generates reports, and triages all findings to accelerate security actions. The first step in taking action on a high-risk finding is to notify those who need to remediate the incident. The workflow integration between HackerOne and PagerDuty ensures those vulnerability findings reach the right people at the right time.
Once HackerOne has validated and prioritized a vulnerability report, customers using the PagerDuty and HackerOne integration will receive an alert if the report is deemed a high or critical severity. Report severity is determined according to the CVSS scoring system, as seen in Figure 1 below.
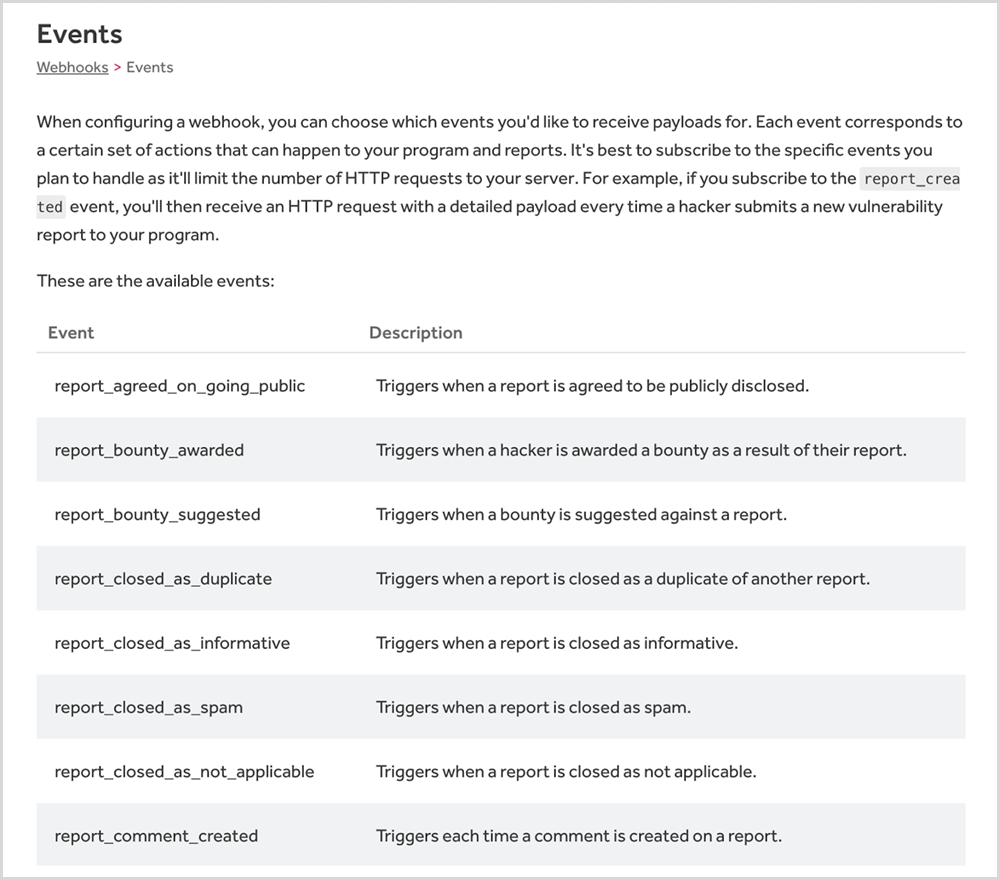
You can select events for Webhooks to trigger, as seen in Figure 2 below, allowing you to customize the alert content sent to PagerDuty.
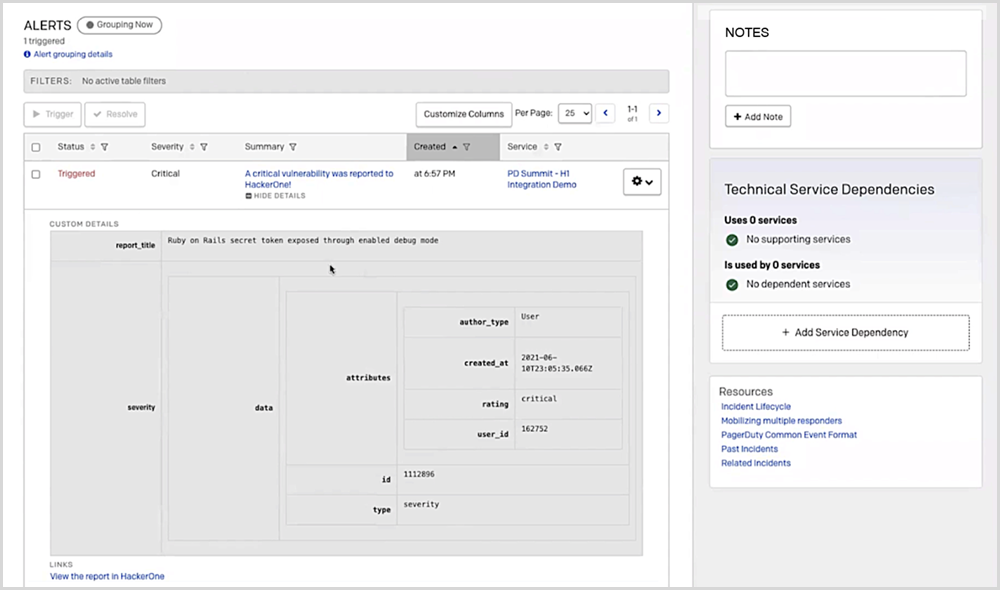
Once the finding is identified as high or critical, an alert appears in PagerDuty, routed to the right person on the Security Ops team. The alert contains details on the type of vulnerability, assignee, time, and description, as seen in Figure 3 below. In PagerDuty, the alert contains information such as source, status, time, escalation policy, and more which helps the responder determine the action needed.
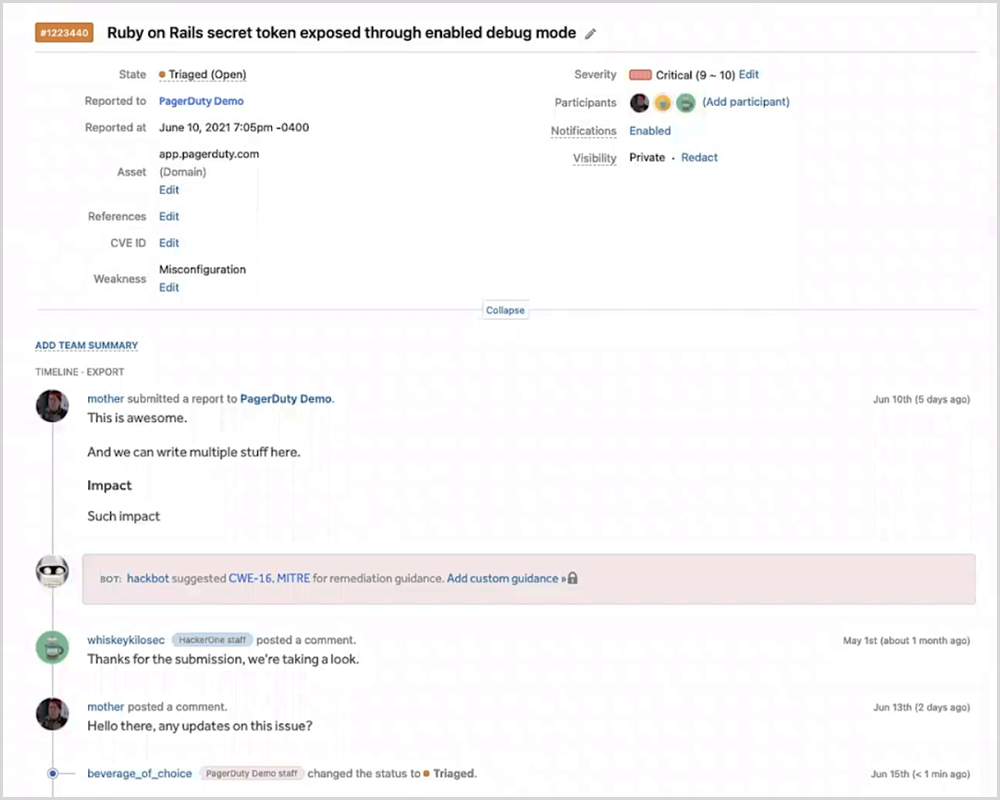
As seen in Figure 4 below, responders can also toggle back to the original HackerOne report to see hacker commentary and additional detail around the finding so they can make well-informed remediation decisions.
Each new and triaged vulnerability report in HackerOne with a high or critical severity will automatically create a PagerDuty alert and notify the appropriate people, customized to your use cases. These real-time alerts allow security teams to respond quickly to severe vulnerabilities.
For most security operations teams, SLAs for remediation of these critical vulnerabilities are compressed. This integration between HackerOne and PagerDuty is the ideal solution for optimizing SLAs and reducing Mean Time To Remediate (MTTR). It allows for fast communication of high-impact vulnerabilities to Security Ops teams and ensures safer applications for end-users. It is available to all HackerOne Enterprise customers. To learn more about HackerOne and PagerDuty together, watch the demo. For setup details, go to our documentation page.
