Cybersecurity researchers at Cyble have uncovered an extensive phishing campaign that represents a significant evolution in credential theft tactics. The operation, which targets organizations across multiple industries in Central and Eastern Europe, bypasses conventional email security measures by using HTML attachments that require no external hosting infrastructure.
Unlike traditional phishing attacks that rely on suspicious URLs or compromised servers, this campaign embeds malicious JavaScript directly within seemingly legitimate business documents. When victims open these HTML attachments—disguised as requests for quotation (RFQ) or invoices—they’re presented with convincing login interfaces impersonating trusted brands like Adobe, Microsoft, FedEx, and DHL.
How the Attack Works
The attack chain begins with targeted emails posing as routine business correspondence. The HTML attachments use RFC-compliant filenames such as “RFQ_4460-INQUIRY.HTML” to appear legitimate and avoid triggering basic security filters.
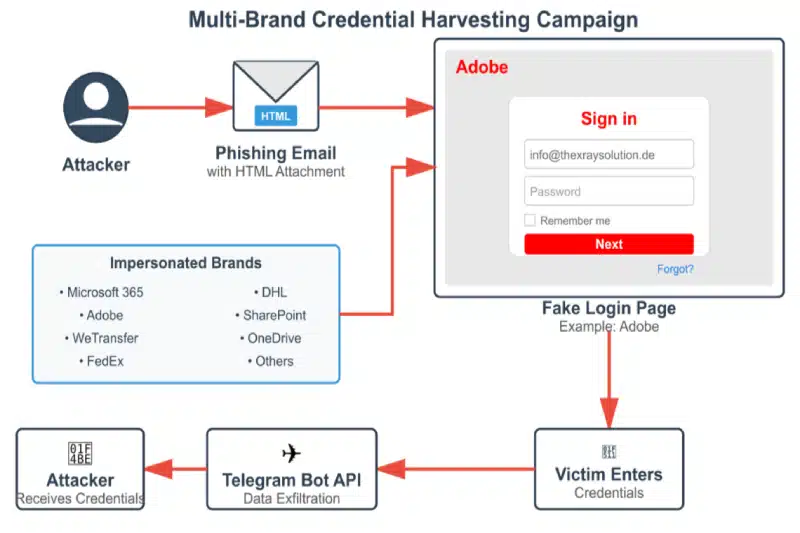
Once opened, the file displays a blurred background image of an invoice or document with a centered login modal, typically branded with Adobe styling. The victim, believing they need to authenticate to view the document, enters their email and password credentials.
Behind the scenes, embedded JavaScript captures this data and immediately transmits it to attacker-controlled Telegram bots via the Telegram Bot API. This approach eliminates the need for traditional command-and-control infrastructure, making the operation harder to detect and disrupt.
“The sophistication lies not just in the technical execution but in how it circumvents multiple layers of security,” explains the Cyble Research and Intelligence Labs (CRIL) team. The self-contained nature of the HTML files means they don’t trigger alerts for suspicious external connections during initial email scanning.
Technical Sophistication
Analysis of multiple samples reveals ongoing development and refinement of the attack methodology. Earlier versions used basic JavaScript, while more recent samples implement CryptoJS AES encryption for obfuscation and sophisticated anti-forensics measures.
Advanced samples block common investigation techniques by disabling F12 developer tools, preventing right-click context menus, blocking text selection, and intercepting keyboard shortcuts like Ctrl+U (view source) and Ctrl+Shift+I (inspect element). These measures significantly complicate analysis efforts by security researchers and forensic investigators.
The malware also employs dual-capture mechanisms, forcing victims to enter their credentials multiple times while displaying fake “invalid login” error messages. This ensures accuracy of the stolen data while maintaining the illusion of a legitimate authentication failure.
Beyond credentials, the samples collect additional intelligence including victim IP addresses (using services like api.ipify.org), user agent strings, and other environmental data that could be valuable for subsequent attacks.
Scale and Targeting
CRIL’s investigation identified multiple active Telegram bots with naming conventions like “garclogtools_bot,” “v8one_bot,” and “dollsman_bot,” each operated by distinct threat actors or groups. The decentralized infrastructure suggests either collaboration among multiple cybercriminal groups or widespread availability of phishing toolkit generators.
The campaign primarily targets organizations in the Czech Republic, Slovakia, Hungary, and Germany, with affected industries including manufacturing, automotive, government agencies, energy utilities, telecommunications, and professional services. The geographic concentration and industry selection indicate careful reconnaissance and targeting based on regional business practices.
Threat actors customize their approach for different markets, using German-language variants for Telekom Deutschland impersonation and Spanish-language templates for other targets. The modular template system enables rapid deployment of new brand variants as the campaign evolves.
Detection and Defense
Security teams face challenges in detecting this threat due to its innovative use of legitimate platforms. Traditional indicators like suspicious URLs or known malicious domains don’t apply when the attack infrastructure consists of HTML attachments and Telegram’s legitimate API.
Cyble recommends organizations implement several defensive measures. Security operations centers should monitor for unusual connections to api.telegram.org from end-user devices, particularly POST requests that wouldn’t occur in normal business operations. Network traffic to third-party services like api.ipify.org and ip-api.com from endpoints should also trigger investigation.
Email security policies should treat HTML attachments as high-risk file types requiring additional scrutiny. Organizations should implement content inspection that flags HTML attachments containing references to the Telegram Bot API or similar public messaging platforms.
For end users, the guidance remains straightforward: exercise extreme caution with unsolicited HTML attachments, especially those prompting credential entry to view documents. Any unexpected authentication request should be verified through independent channels before entering credentials.
Cyble has published complete indicators of compromise, including specific bot tokens, attachment patterns, and YARA detection rules to its GitHub repository, enabling security teams to hunt for signs of compromise within their environments and implement preventive controls.
