BadCandy, a Persistent Access Threat to Network Edge Devices
BadCandy is a Lua-based web shell implant deployed on compromised Cisco IOS XE routers and switches through exploitation of CVE-2023-20198, a vulnerability with the maximum CVSS score of 10.0. The flaw allows remote unauthenticated attackers to create highly privileged accounts on vulnerable systems, enabling complete control of affected devices.
Once deployed, the BadCandy implant consists of an Nginx configuration file named cisco_service.conf that establishes a URI path for interacting with the web shell. Despite being non-persistent—meaning the implant is removed upon device reboot—the privileged accounts created during exploitation persist across reboots, providing threat actors with continued access even after the visible implant disappears.
ASD’s advisory reveals that since July 2025, over 400 devices were potentially compromised with BadCandy in Australia. While this number has decreased following bulk victim notifications sent by ASD through service providers, the fact that over 150 devices remain compromised years later shows the significant challenges in vulnerability management and incident response across Australian organizations.
The Vulnerability Chain
The BadCandy campaign exploits a two-vulnerability chain affecting Cisco IOS XE Software’s web UI feature.
CVE-2023-20198 (CVSS 10.0 Critical): This vulnerability enables remote, unauthenticated attackers to create accounts with privilege level 15 access on affected systems. Privilege level 15 grants full administrator access, allowing attackers to take complete control of the device. The flaw affects the authentication mechanism in the web UI, essentially providing a backdoor for credential creation without any authentication requirement.
CVE-2023-20273 (CVSS 7.2 High): Once attackers establish access through CVE-2023-20198, they exploit this second vulnerability to execute commands with root privileges. This command injection vulnerability, caused by insufficient input validation, allows the deployment of the BadCandy implant to the device’s file system. The combination of both vulnerabilities provides threat actors with persistent privileged access and command execution capabilities.
The vulnerabilities were first exploited in the wild in October 2023, with Cisco Talos researchers identifying and naming the BadCandy implant. Initial campaigns compromised tens of thousands of Cisco IOS XE devices globally, making it one of the most significant network infrastructure compromises in recent years.
Also read: Understanding Cisco IOS XE Vulnerabilities: CVE-2023-20198 and More
Who’s Behind BadCandy
ASD’s assessment indicates that while any threat actor can leverage the BadCandy implant, both criminal and state-sponsored cyber actors are believed to be exploiting this vulnerability.
State-sponsored actors target network edge devices for strategic intelligence collection, positioning for potential disruptive attacks, and establishing persistent presence in target networks. Compromised routers and switches provide valuable vantage points for intercepting network traffic, mapping internal infrastructure, and conducting man-in-the-middle attacks without requiring deeper network penetration.
Criminal actors exploit network infrastructure for various purposes including establishing proxy networks for anonymizing criminal operations, conducting distributed denial-of-service (DDoS) attacks, deploying cryptomining malware, and positioning for ransomware deployment. The privileged access provided by BadCandy enables extensive post-compromise activities regardless of attacker motivation.
Critically, ASD warns that cyber actors are known to re-exploit previously compromised devices where patches have not been applied and the web interface remains exposed to the internet. This creates an ongoing risk where organizations that remove the implant without properly patching and hardening their devices face immediate recompromise.
The Re-Exploitation Problem
The fact that over 150 devices in Australia remain compromised more than two years after patches became available reveals systemic challenges in vulnerability management. ASD’s advisory explicitly warns about re-exploitation. Threat actors continuously scan for vulnerable devices and immediately compromise any systems where patches haven’t been applied or web interfaces remain improperly secured.
This pattern reflects broader trends observed in the ACSC’s Annual Cyber Threat Report 2024-25, which said legacy IT and inadequate patching were critical vulnerabilities across Australian organizations. Network edge devices present particular challenges because they often run specialized firmware, require careful change management to avoid service disruption, and may be managed by different teams than enterprise IT infrastructure.
The threat report also concluded that Australia faces increasing cyber threats targeting critical infrastructure, with particular emphasis on telecommunications, energy, and government networks where compromised edge devices could enable significant damage or disruption.
BadCandy shares characteristics with other network infrastructure malware families including VPNFilter (2018), which compromised hundreds of thousands of routers globally, and more recent campaigns targeting Fortinet, Pulse Secure, and other VPN and edge devices. These campaigns demonstrate that network infrastructure represents a strategic target that enables subsequent attacks rather than being merely opportunistic exploitation.
The BadCandy timeline also demonstrates this challenge:
- October 2023: Initial exploitation and implant deployment observed
- October 22, 2023: Cisco releases patches for both vulnerabilities
- July 2025: Over 400 Australian devices compromised
- Late October 2025: Over 150 devices still compromised despite bulk notifications
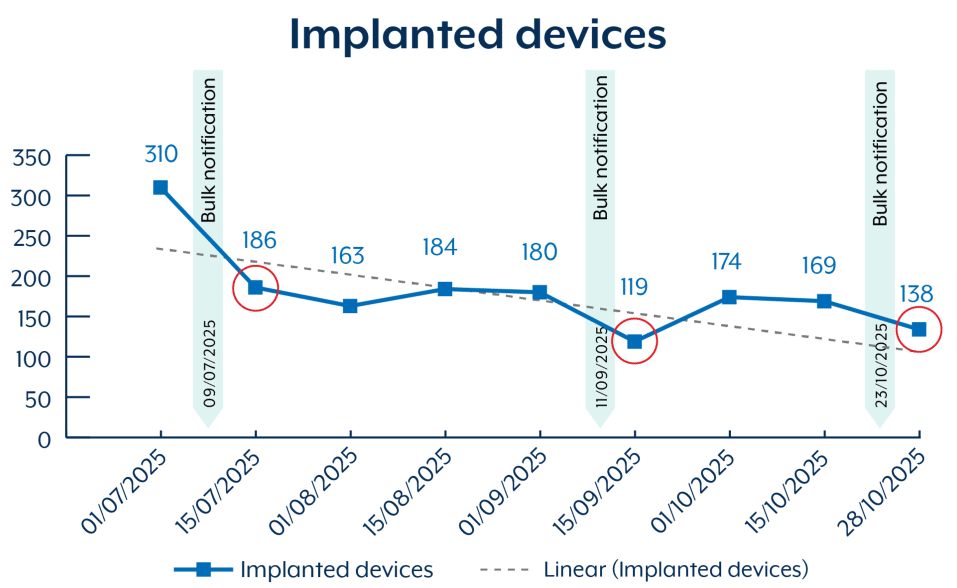
This 24-month window between patch availability and persistent compromises indicates that affected organizations either lack visibility into their Cisco IOS XE deployments, face technical or operational barriers to patching, or haven’t prioritized remediation of this critical vulnerability.
Technical Indicators and Detection Methods
Organizations can detect BadCandy compromise through several technical indicators identified in ASD’s advisory:
Privileged Account Anomalies: Review running configurations for accounts with privilege level 15. Remove any unexpected or unapproved accounts, particularly those with random strings as usernames or accounts named “cisco_tac_admin,” “cisco_support,” “cisco_sys_manager,” or “cisco.” These account names have been observed in BadCandy campaigns and should trigger immediate investigation if not legitimately created.
Unknown Tunnel Interfaces: Review running configurations for unexpected tunnel interfaces. Tunnels appear in configurations as “interface tunnel[number]” followed by IP addresses, tunnel sources, and tunnel destinations. Unauthorized tunnels can provide covert communication channels for data exfiltration or command and control.
Configuration Change Logs: If TACACS+ AAA command accounting is enabled, review logs for unauthorized configuration changes. This provides forensic evidence of attacker activities and helps identify the scope of compromise.
Implant File Presence: Check for the presence of /usr/binos/conf/nginx-conf/cisco_service.conf, the file path where BadCandy is saved. While the implant is non-persistent and removed by reboots, its presence indicates active compromise.
Remediation Steps
Immediate Actions
- Apply patches for CVE-2023-20198 and CVE-2023-20273 according to Cisco’s security advisory
- Reboot affected devices to remove the non-persistent BadCandy implant
- Review and remove unauthorized privilege-15 accounts from running configurations
- Examine configurations for unexpected tunnel interfaces or other unauthorized changes
- Review TACACS+ logs (if available) for evidence of malicious configuration changes
Rebooting removes the BadCandy implant but does NOT reverse additional actions taken by threat actors and does NOT remedy the initial vulnerability. Organizations must address both the symptoms (implant and unauthorized accounts) and the root cause (vulnerability and improper hardening).
Hardening Requirements
Disable HTTP Server Feature: If the web UI isn’t required for operations, disable the HTTP server feature entirely. This eliminates the attack surface that enables CVE-2023-20198 exploitation.
Restrict Web UI Access: If the web UI must remain enabled, implement strict access controls limiting which IP addresses can reach the interface. Never expose management interfaces directly to the internet.
Follow Cisco Hardening Guidance: Implement the comprehensive hardening recommendations in Cisco’s IOS XE hardening guide, including disabling unnecessary services, implementing access control lists, and configuring proper logging.
Implement Edge Device Security Strategies: ASD recommends following its publication on securing edge devices, which provides comprehensive guidance for reducing vulnerabilities in critical network components.
