The original Gootloader malware was used by numerous threat groups, including ransomware affiliates and in additional payloads like SystemBC and IcedID.
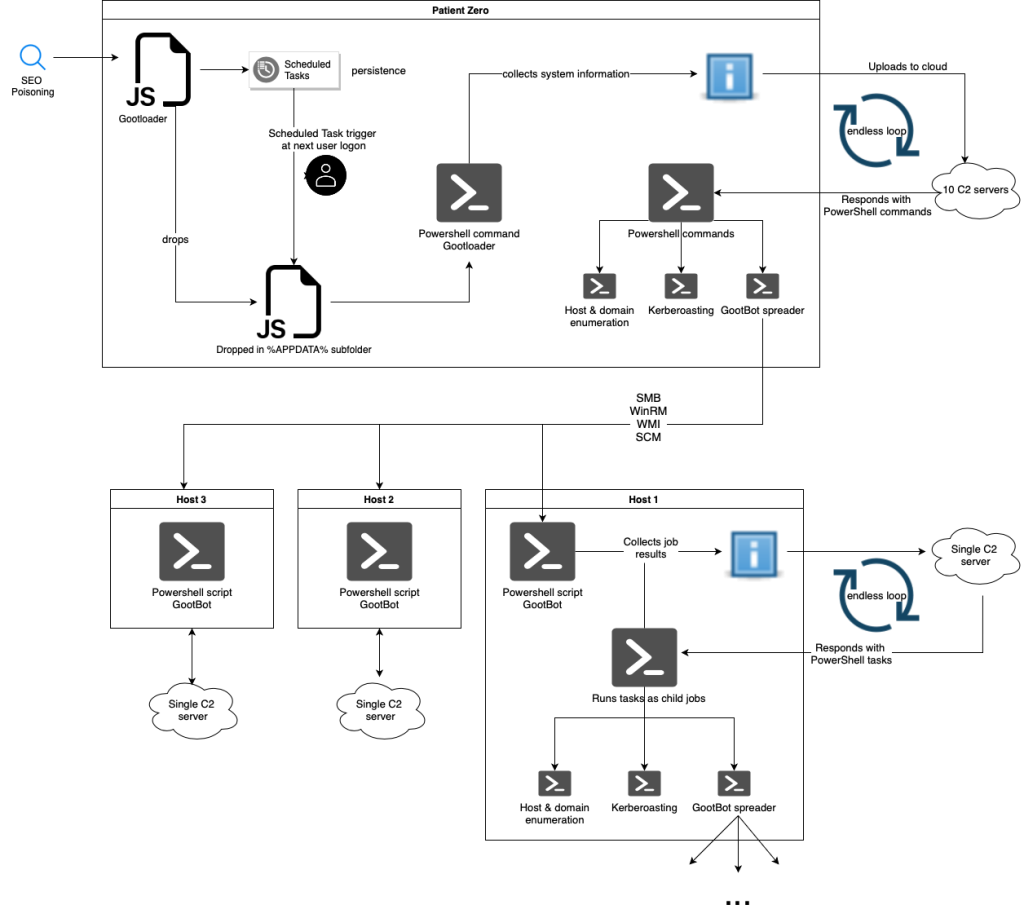
IBM X-Force has discovered a new variant of the notorious Gootloader malware, dubbed GootBot. This malware performs stealthy lateral movement, which complicates the detection or blocking of the campaign within enterprise networks.
According to the blog post authored by Golo Mühr and Ole Villadsen, the Gootloader group implements their custom bot in the latter stages of this attack chain to evade detection, using off-the-shelf tools for establishing C2 communication, such as RDP or CobaltStrike.
Gootloader malware was initially used only as an initial access tool and evolved considerably over time to include GootBot, a lightweight obfuscated PS script. It is downloaded after the Gootloader infection and receives commands via C2 through encrypted PowerShell scripts.
For your information, the Gootloader group (aka UNC2565 or Hive0127) first surfaced in 2014 and focused more on SEO poisoning techniques and compromised WordPress websites to distribute the Gootkit-based Gootloader malware. Tanium’s director of endpoint security research, Melissa Bischoping, explained how SEO poisoning works.
“SEO poisoning drives users to malicious payloads by manipulating the search results for key terms. Most security awareness training focuses heavily on phishing and other methods where an attacker sends something to the user. There’s a false sense of security that people place in search result top rankings and an outdated mindset that the lock on the address bar means a site is safe.”
Hackread.com has been following the Gootloader group’s activities since its emergence. The group frequently targets business-related online searchers like queries about legal contracts, creating legit-looking websites, and positioning them on the first page of search results. Once the user visits the page, they entice them into downloading archive files, which appear harmless and relevant to their queries but actually contain Gootloader malware.
In March 2021, Sophos cybersecurity firm confirmed that Gootloader has evolved into a sophisticated loader framework from serving as an initial access point, revealing that its delivery method had expanded beyond the Gootkit malware family. As an initial access point, Gootloader malware was used by numerous threat groups, including ransomware affiliates and in additional payloads like SystemBC and IcedID.
GootBot is a novel Gootloader variant. It is a PowerShell payload encapsulating a single C2 server address. Its strings use a replacement key to conduct mild obfuscation. The malware, just like Gootloader, sends a GET request to the C2 server, requesting PowerShell tasks, and gets a string comprising a Base64-encoded payload.
The last 8 digits of the code are the task’s name. It then decodes the payload and injects it into the script block before executing it. The payload runs asynchronously, maintaining a default beaconing interval of 60 seconds. When it receives a C2 task, the next loop iteration starts, and for completed jobs, the results are returned.
GootBot is designed for lateral movement within the network, noted X-Force researchers. Its C2 infrastructure can quickly generate numerous GootBot payloads for distribution, each having a unique C2 address, and can cause multiple infections of the same host. It also runs a reconnaissance script and contains a unique GootBot ID for the host.
This effective malware lets attackers swiftly propagate across the compromised network to deploy additional malicious software. Unlike Gootloader, GootBot spreads through infected domains to reach the domain controller. This indicates a shift in attack tactics from Gootloader operators and enhances the success rate of post-exploitation stages, including Gootloader-based ransomware affiliate activity.
The malware is capable of extracting domain user name, and OS details from the registry key, checks for x86 dir and int ptr size if 64bit architecture is detected, and obtains information about domain controllers from registry and ENV var, SID, local IP address, hostname, and running processes. The data gets formatted with the specified ID.
The emergence of the GootBot variant highlights that attackers are employing sophisticated methods to stay undetected and spread laterally across the network. Lateral-movement scripts are possible through various techniques, such as WinRM, SMB, and WinAPI calls, to spread the payload to other hosts.
Organizations must implement advanced security mechanisms, including endpoint detection and response (EDR) solutions and regularly updating software to prevent the threat. Bugcrowd cybersecurity firm’s founder and chief strategy officer, Casey Ellis, shared the following statement with Hackread.com regarding the current Gootloader campaign.
“This all strikes me as a very organized and thoughtful initial access broker (IAB). Their watering-hole style deployment of malicious SEO isn’t particularly targeted, however, it suits the opportunistic attack model of an IAB quite well. For defenders, it’s important to remember that organized cybercrime is continuing to evolve, stratify, and mature and that the threat actor behaviours now include this type of long, wide game.”
Keeper Security’s CEO and co-founder, Darren Guccione, in an exclusive statement shared with Hackread.com, noted that it is hard for innocent users to distinguish between authentic and fabricated search results, which makes SEO poisoning so successful.
“Innocent people who are not trained on SEO (Search Engine Optimization) and SEO-related attack vectors, including SEO poisoning, generally focus on the aesthetics of the search results page they are familiar with such as the domain name and the logos displayed. Often, threat actors will use language like “Official Website” to lure people into clicking a dangerous link or visiting a spoofed site that can download Gootloader or other malware onto their device.”
However, some scrutiny can prove beneficial in detecting malicious websites, said Guccione. “Phony or spoofed websites will usually have a different website address than the official company name and can also use different domain extensions than the one for the legitimate website. The majority of popular websites use the domain extension .com,” explained Guccione.
“If you visit a site, pay special attention to the domain itself and if it appears to be abnormally long or unrecognizable based on your normal search activity, it’s best to ignore it – and not click on any link. Online tools such as a Google Transparency Report can also be used to determine whether a site is safe.”
RELATED NEWS
- Google Algorithm Updates vs SEO Strategies
- How Can SEO Help Increase Website Security?
- Google Indexed Trove of Bard AI User Chats in Search Results
- Ad-blocker Chrome extension AllBlock injected ads in Google searches
- Malicious Chrome, Edge extensions manipulating Google search results
