I’ve been very busy these past few months, leaving little time to hack. I’m very glad to be back at it. I decided to write my first Burp extension—since it seems to be working quite nicely for me, I thought I’d share it!
The extension, BurpParamFlagger, adds a passive scan check to flag URL parameters whose name or value may indicate a possible insertion point for SSRF or LFI. The extension will look at both the name of a parameter and the value of that parameter and look for any common words or patterns indicating that you may want to do some further testing.
You can find the project’s Github repository here:
https://github.com/allyomalley/BurpParamFlagger
For example, SSRF checks include looking for parameter names like ‘redirect’, ‘url’, or ‘domain’, as well as looking for values that look like a URL:
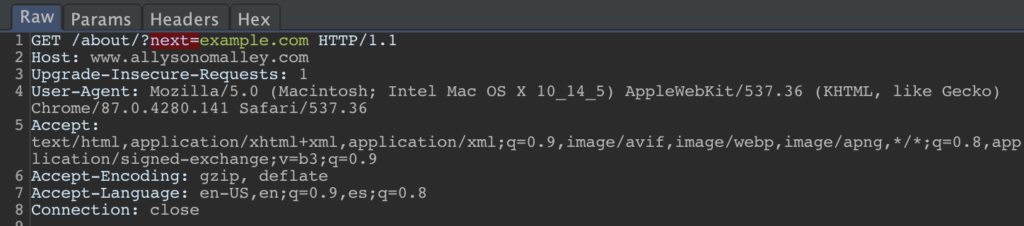
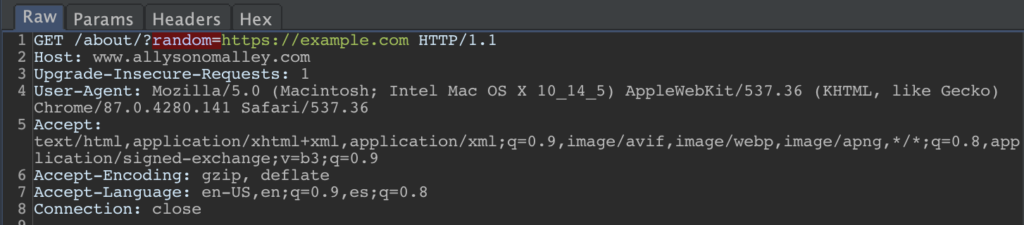
LFI checks look for names like ‘include’, ‘attach’, or ‘file’, and look for values that have a file extension:
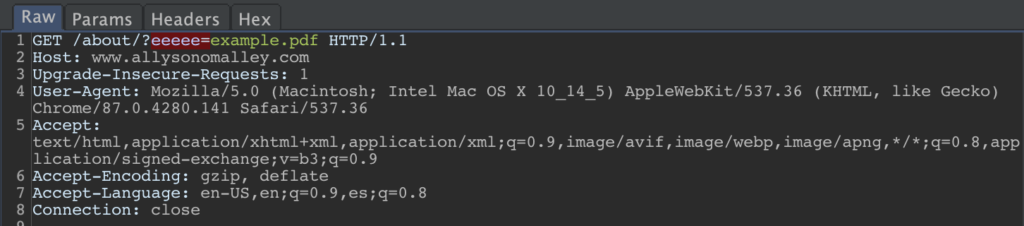
So, when you see a flagged parameter issue pop up in your dashboard, take a look! And if you think there may indeed be an opportunity there, send the request on over to Intruder or Repeater and do some testing.
I also wanted to add a note just in case anyone isn’t aware: I believe you’ll need Burp Professional to use this extension, since it builds off of Pro’s scanner functionality.
In the future, I’m thinking about adding another check for possible SQLi insertion points, and perhaps adding a setting to enable/disable the types of vulnerabilities you’d like to check for.
I hope this helps lead some of you to beautiful bugs!
