Security researchers have uncovered a sophisticated cyberattack campaign that exploited publicly exposed ASP.NET machine keys to compromise hundreds of Internet Information Services (IIS) servers worldwide.
The operation, detected in late August and early September 2025, deployed a previously undocumented malicious module dubbed “HijackServer” that transforms legitimate web servers into tools for search engine manipulation while maintaining persistent backdoor access.
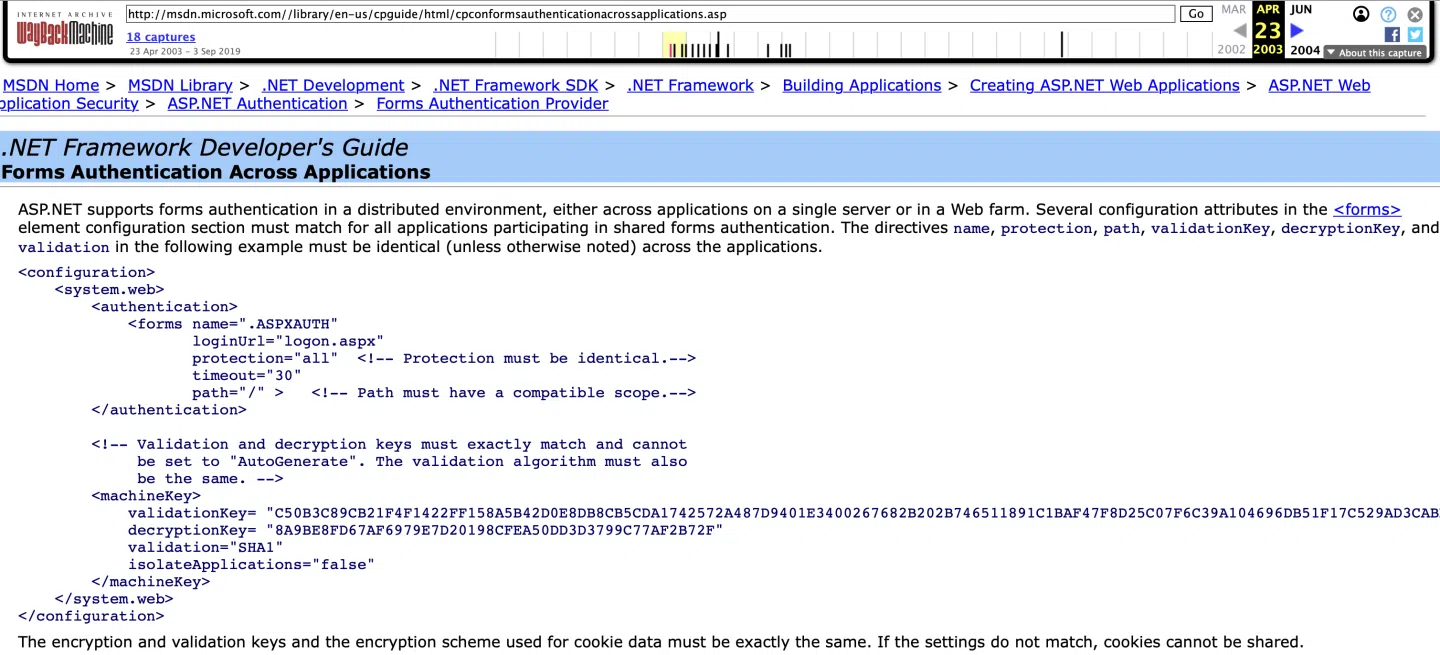
The attack leverages a critical weakness that has plagued web administrators for two decades. Researchers discovered that compromised servers were using example cryptographic keys published in a Microsoft Developer Network help page dating back to 2003.
These “secrets,” meant only as configuration examples, were copied verbatim by countless administrators over the years and shared across programming forums including StackOverflow.
Attackers exploited these publicly known machine keys to manipulate ASP.NET viewstate deserialization, achieving remote code execution on vulnerable servers.
Microsoft had warned about this attack vector in early 2025, identifying over 3,000 publicly exposed machine keys in code repositories. The problem intensified during summer 2025 when SharePoint vulnerabilities enabled additional machine key exfiltration.
The threat actors deployed a comprehensive toolkit to automate their operations. The infection process began with viewstate exploitation, followed by privilege escalation using “Potato” techniques to create hidden administrator accounts.
Attackers can trivially exploit ASP .NET viewstate deserialization to remotely execute code if they know the associated cryptographic secrets.
Attackers then installed the HijackServer module alongside a customized rootkit derived from the open-source “Hidden” project, which concealed malicious files and registry keys from detection.
The toolkit included GUI deployment tools with Chinese-language interfaces, automated installation scripts, and a kernel driver signed with an expired but still-functional certificate from “Anneng electronic Co. Ltd.”
Researchers identified the toolset had been in use since late 2024, with components uploaded to online scanners in December of that year.
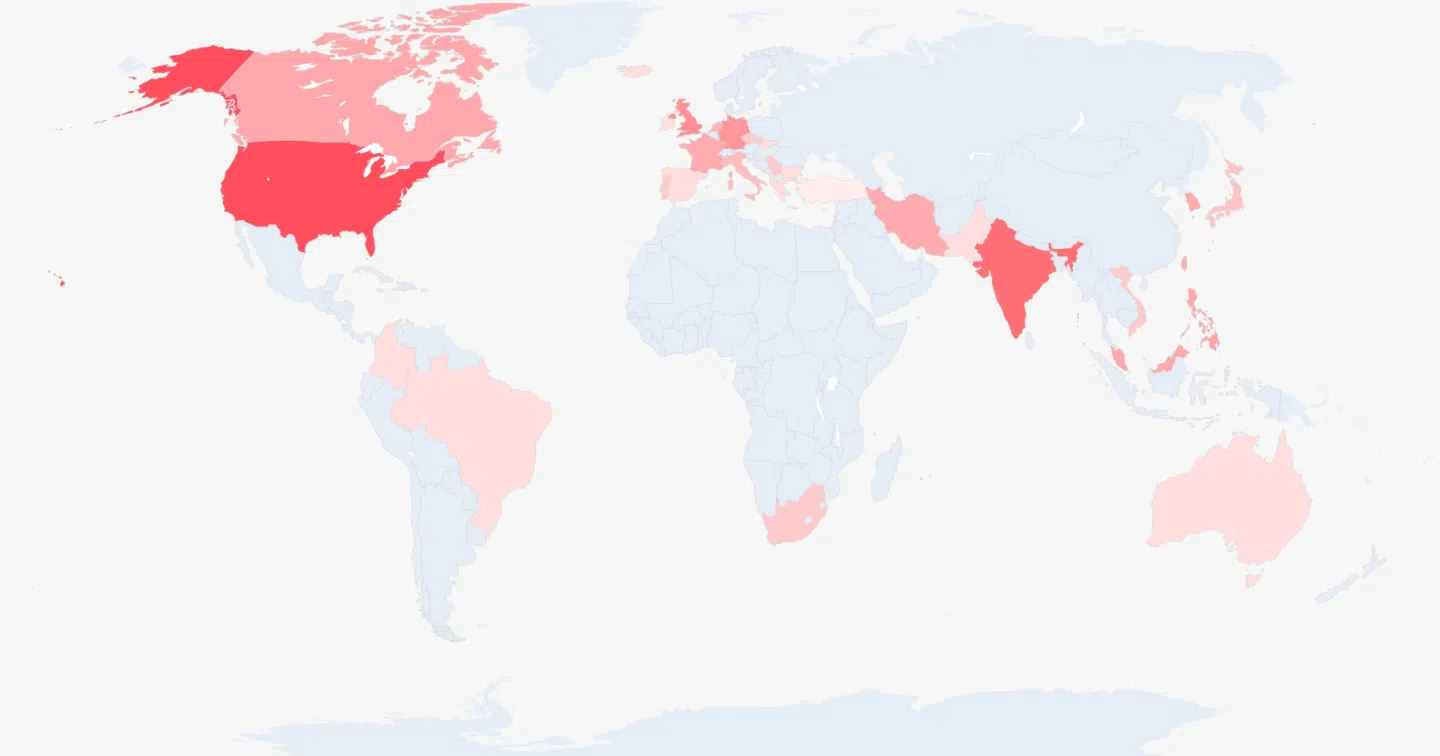

Researchers identified 171 distinct HijackServer installations affecting approximately 240 server IP addresses and 280 domain names across the globe.
The campaign primarily targeted servers in Asia, with the oldest known compromise dating back to 2024 on a server geolocated in Singapore.

The malicious module operates by intercepting HTTP requests and generating fake content for Google’s web crawlers.
When search engines visit compromised servers, HijackServer serves dynamically generated pages containing investment-related content with links redirecting to questionable cryptocurrency websites.
This black-hat SEO technique successfully manipulated search engine rankings, with generated pages appearing in actual Google search results.
Hidden Backdoor Raises Security Concerns
While the primary purpose appears to be SEO fraud for financial gain, HijackServer contains a critical security flaw that affects all compromised servers.
The module includes an unauthenticated remote command execution capability accessible through specific URL paths. This backdoor allows any attacker who discovers the compromised server to execute arbitrary commands without authentication, creating a pool of vulnerable systems available for exploitation by any malicious actor.
The operators appear to be Chinese-speaking based on language artifacts throughout the toolset, including command names, configuration variables, and documentation.
Security firm Elastic Security Labs, in cooperation with two other organizations, published concurrent research referring to the IIS modules as “TOLLBOOTH,” confirming the widespread nature of this threat.
Organizations running IIS servers should immediately audit their ASP.NET machine key configurations, review IIS module installations, and implement detection rules to identify compromise indicators associated with this campaign.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
