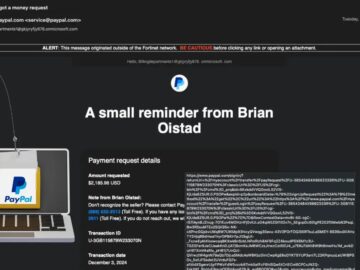
A massive Indonesian-speaking cybercrime operation spanning over 14 years has been uncovered, revealing a sophisticated infrastructure that shows hallmarks of state-level backing and resources typically associated with advanced persistent threat actors.
Security researchers at Malanta have exposed what may be one of the largest and most complex Indonesian-speaking cyber operations ever documented a sprawling ecosystem that has operated continuously since at least 2011.
The campaign orchestrates an intricate web of illegal gambling operations, malware distribution, domain hijacking, and infrastructure infiltration across enterprise and government networks worldwide.
The sheer scale and persistence of this operation suggest resources and organization consistent with state-sponsored threat activity rather than typical cybercriminal enterprises.
The threat actor maintains control over more than 328,000 domains, consisting of 236,433 purchased domains specifically for gambling operations, 90,125 hijacked legitimate domains, and 1,481 compromised subdomains.
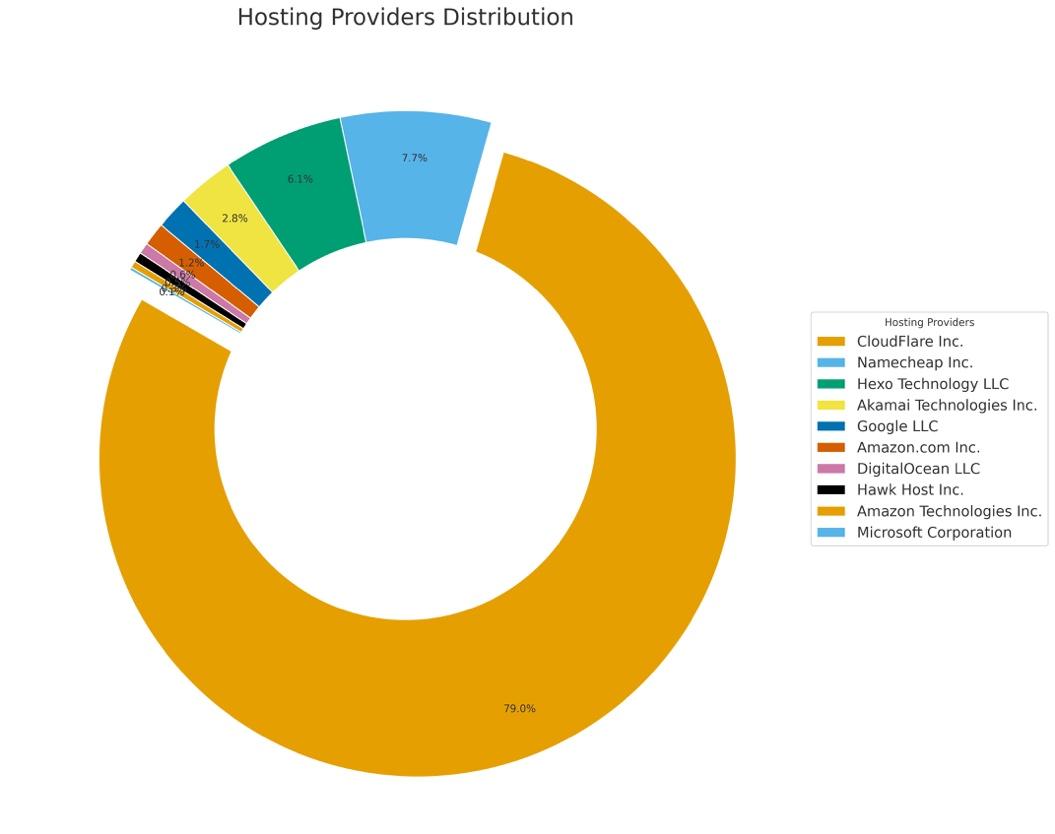
This massive infrastructure spans cloud platforms, primarily AWS and Azure, with hosting concentrated on Cloudflare and U.S.-based IP addresses.
What distinguishes this operation is not merely its size but its sophistication. The attackers systematically exploit WordPress vulnerabilities, PHP component weaknesses, dangling DNS records, and expired cloud resources to weaponize trusted domains.
Some hijacked government subdomains in Western countries have been configured with TLS-terminating reverse proxies a technique that allows the threat actor to disguise command-and-control traffic as legitimate HTTPS connections from government domains while simultaneously enabling session cookie theft.
Mobile Malware Distribution Network
Researchers discovered approximately 7,700 domains containing links to at least 20 AWS S3 buckets hosting thousands of malicious Android applications with gambling-themed names like deltaslot88.apk and jayaplay168.apk.
The gambling websites themselves are geo-restricted, typically accessible only from Indonesian IP addresses, and require registration with Indonesian phone numbers and local banking details from institutions like BCA, Mandiri, and digital wallets including DANA and OVO.
Laboratory analysis revealed these APKs function as droppers that download additional malicious payloads, access external storage for data exfiltration, and utilize Google’s Firebase Cloud Messaging for remote command delivery.
Hardcoded credentials and API keys within the applications provide telemetry and management capabilities the malware shares common command-and-control infrastructure, with multiple samples communicating with domains like jp-api. namesvr[.]dev.
The domain and subdomain hijacking operation represents a particularly concerning aspect of the campaign.
Attackers inject malicious content into compromised websites, often concealing gambling links within harvested HTML from popular platforms like Lazada, eBay, and Envato.
Analysis shows these 108,000 domains without specific templates are hosted on only approximately 600 IP addresses, with 92% of these IPs hosting at least two domains strong evidence of centralized control by a single threat actor.
The subdomain hijacking targeting Western government entities is especially troubling. These compromised subdomains inherit session cookies from their parent domains, creating opportunities for credential theft from financial services and sensitive data systems.
The NGINX-based reverse proxies deployed on legitimate government FQDNs provide the attackers with highly stealthy channels for cybercrime activities and malware communications that appear entirely legitimate.
Supporting Infrastructure and Attribution
The operation’s supporting infrastructure includes 38 burner GitHub accounts hosting malicious templates, webshells, Google verification strings, and distribution artifacts.
Threat actor has hijacked at least 1,481 subdomains. Most of them were hosted on AWS, Azure, and GitHub.

Researchers also identified 480 domain lookalikes impersonating major organizations including Slack, Amazon, Facebook, Instagram, and Shopify many registered since 2020 and renewed annually, demonstrating intentional, persistent operation.
Over 51,000 stolen credentials linked to this infrastructure have surfaced in dark web forums, originating from gambling sites, infected Android devices, and hijacked subdomains.
Researchers estimate the operation requires between $725,000 and $5.3 million annually just for domain registration, hosting, and certificate costs financial resources that exceed typical cybercriminal capabilities.
Combined with the operation’s 14-year longevity, sophisticated techniques blending exploitation and opportunistic compromise, underground marketplace presence, and organizational maturity, the characteristics align more closely with state-sponsored threat operations than conventional financial cybercrime.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.