Here’s a look at the most interesting products from the past month, featuring releases from: Abnormal Security, Arista Networks, Armorblox, BigID, Binarly, Cofense, Cyera, Cynalytica, D3 Security, Eclypsium, GitGuardian, Guardz, Halo Security, Immuta, Malwarebytes, ManageEngine, Netskope, Obsidian Security, Searchlight Cyber, Sotero, Stamus Networks, ThreatX, Traceable AI, Venafi, Veracode, Versa Networks, Wazuh, and Zyxel Networks.
Malwarebytes unveils WorldBytes to help users reveal the hidden cyber threats around them
Powered by Malwarebytes and AI technology, WorldBytes empowers users to use their mobile devices to scan the world around them and get real-time threat assessments of anything and everything – including questionable Tinder dates, the unlabeled sauce at the back of their fridge and their neighborhood cat. The responses, powered by ChatGPT, humorously explain the potential cyber risks lurking within.
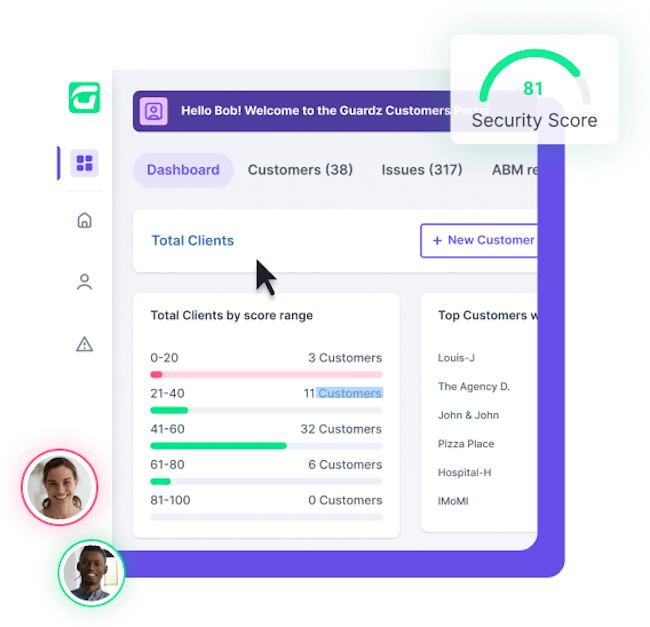
Guardz releases cybersecurity platform for MSPs and IT professionals
Guardz’s new MSP cybersecurity platform is an all-in-one solution providing businesses with both 24/7 cyber protection and cyber insurance coverage. Within the platform, MSPs can seamlessly control multiple customers’ cyber posture, subscription plans, and remediation from a single, multi-tenant dashboard.
Obsidian’s SSPM solution enables organizations to increase their SaaS security
Obsidian Security released its latest suite of SaaS security solutions. This suite of solutions comprising Obsidian Compliance Posture Management, Obsidian Integration Risk Management, and Obsidian Extend will together enable security and GRC teams to increase their SaaS security and compliance posture measurably.
Stamus Networks U39 uncovers hidden anomalies in a proactive threat hunt
With U39, Stamus Security Platform users now have access to 21 new guided threat hunting filters and additional sources of threat intelligence, including 2 lateral movement rulesets and 3 suspicious domain lists. SSP can now detect activity from a match on the media type (also known as mime-type) and can ingest additional third-party threat intelligence feeds to trigger a detection event based on a match on IP addresses and domain lists.

Cynalytica OTNetGuard provides visibility into critical infrastructure networks
Cynalytica has launced its Industrial Control System (ICS/SCADA) monitoring sensor, OTNetGuard, that passively and securely captures analog, serial, and IP communications closing the capabilities gap in complete monitoring of OT networks.
GitGuardian Honeytoken helps companies secure their software supply chains
With attackers increasingly targeting components in the software supply chain as entry points, GitGuardian’s Honeytoken offers a proactive and pragmatic approach to detect and limit the impact of data breaches. Honeytokens look like real credentials, but don’t grant access to actual customer data, instead only triggering alerts that report the intruder’s IP address.
ThreatX Runtime API & Application Protection goes beyond basic observability
With ThreatX RAAP, organizations can extend protections beyond the edge and address a myriad of risks to runtime environments, including insider threats, malware, web shells, remote access software, code injections and modifications, and malicious rootkits.
BigID’s data minimization capabilities enable organizations to identify duplicate data
With BigID’s data minimization and cleanup capabilities, organizations can now automatically find duplicate data quickly and delete it in accordance with retention policies – enabling full data lifecycle management across all of their data, everywhere.
Netskope Endpoint SD-WAN helps enterprises accelerate edge networking
Announced as the newest addition to the Netskope Borderless SD-WAN portfolio, Netskope Endpoint SD-WAN offers workers anywhere the same level of application experience and security from their laptops or other devices as they would receive in the corporate office, without requiring any hardware.
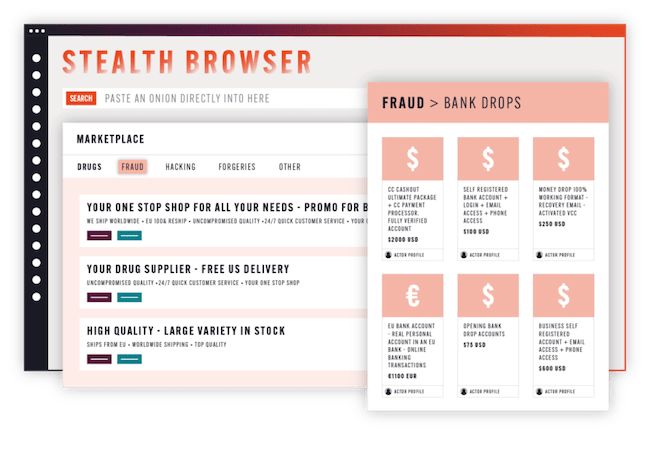
Searchlight Cyber launches Stealth Browser for secure dark web access
Stealth Browser eliminates these risks by automatically masking the investigator’s digital fingerprint, allowing both novice and experienced investigators to access Tor and I2P onions on the dark web without risk to themselves or their organization’s infrastructure.
Wazuh 4.4 combats breaches, ransomware, and cyberattacks all from a single agent
Wazuh launched Wazuh 4.4, the latest version of its open source security platform. The latest version adds multiple new features, including IPv6 support for the enrollment process and agent-manager connection, and support for Azure integration within Linux agents.

Binarly Transparency Platform identifies vulnerabilities and malicious threats in code
At the core of the Transparency Platform is a Vulnerability Analysis engine that leverages deep code inspection to detect vulnerabilities within analyzed firmware images. This tool provides organizations with crucial insight into the existence of known vulnerabilities, allowing them to address potential threats before they can be exploited.
Zyxel SCR 50AXE boosts network security for small businesses and remote workers
The feature-rich SCR 50AXE is a secure cloud-managed router that incorporates a business-class firewall, VPN gateway, WiFi 6E connectivity, and built-in subscription-free security to protect the network from threats including ransomware and malware.
Cofense Protect+ defends mid-size organizations from cyber threats
Protect+ uses Cofense’s crowd-sourced intelligence and inspects emails in real-time to make instantaneous decisions as to whether emails are malicious. Email attacks are detected upon arrival and are automatically moved away from the user’s inbox.
Armorblox releases Graymail and Recon Attack Protection to stop malicious emails
Armorblox Graymail and Recon Attack Protection uses advanced machine learning algorithms and large language models to enable the precise detection and classification of graymail, such as newsletters and marketing emails, and unwanted solicitation from a legitimate source.

Versa Zero Trust Everywhere strengthens security posture for onsite, remote and hybrid workers
With Versa Zero Trust Everywhere, enterprises can now leverage Versa’s AI/ML-powered Unified SASE platform to enable in-line zero trust policy enforcement for both remote workers and onsite/hybrid workers in campus and branch offices.
Veracode Fix helps organizations tackle software security issues
Veracode Fix is a security-specialist machine learning solution, which uses the same transformer architecture on which Chat GPT is built. It generates secure code patches developers can review and implement to remediate security flaws, without manually coding a fix.
D3 Security Smart SOAR improves response to incidents
D3 Security has launched its Smart SOAR platform, which expands beyond traditional SOAR with hyperscalable, risk-based autonomous triage and incident remediation across the entire stack.
Venafi Firefly enhances the security of machine identities for cloud-native applications
Part of the Venafi Control Plane for Machine Identities, Firefly enables security teams to securely meet developer-driven machine identity management requirements for cloud native workloads by issuing machine identities, such as TLS and SPIFFE, locally at high speeds across any environment.
Sotero Ransomware Protection encrypts data to prevent theft and extortion
Sotero’s patented machine learning capabilities look at patterns or signatures of previously discovered threats at the disk level to identify new threats as they develop. Sotero utilizes a behavior-based approach to detect new strains of ransomware based on how they interact with files and data.
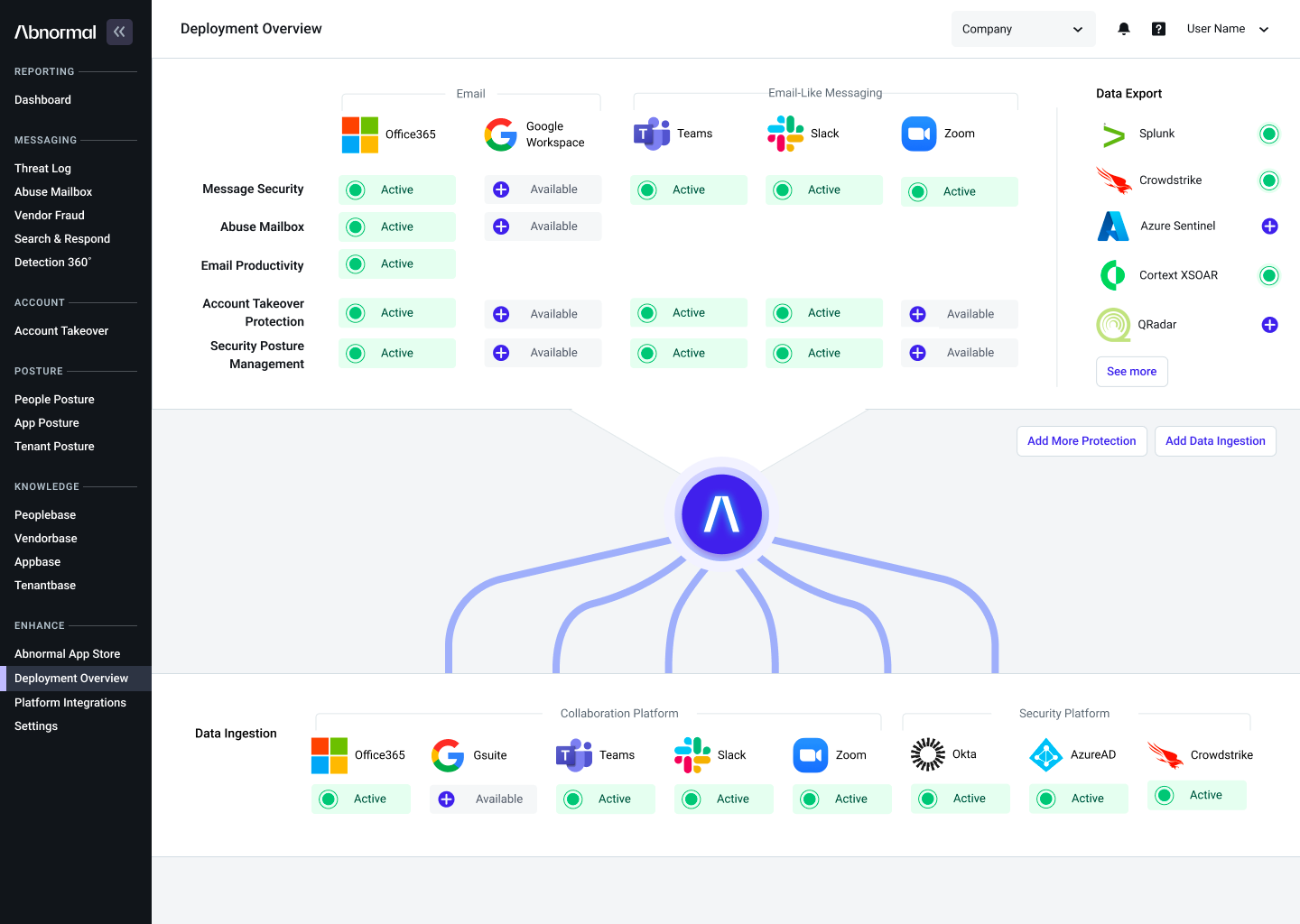
Abnormal Security expands its platform and launches new products
Abnormal Security launched three new products focused on expanding security detection for Slack, Microsoft Teams and Zoom. The new products will extend the power of the Abnormal platform to detect suspicious messages, remediate compromised accounts and provide insight into security posture across the three applications.
ManageEngine releases MSSP Edition of Log360 Cloud
ManageEngin launched the MSSP Edition of its cloud-based SIEM solution, Log360 Cloud, designed to address the unique business challenges of MSSPs and thereby drive up their profit margins.
Cyera enhances its AI-powered data security platform to stop sensitive data exfiltration
Cyera has introduced new operational capabilities in its AI-powered data security platform, to help security teams stop data exfiltration and remediate sensitive data exposures in real time.
Immuta releases new data security features to help users accelerate remediation efforts
Immuta announced new vulnerability risk assessment and dynamic query classification capabilities for the Immuta Data Security Platform. These new features enable customers to promptly identify and prioritize security gaps, protecting sensitive data based on the context and sensitivity levels.
Traceable AI Zero Trust API Access detects and classifies the data that APIs are handling
Traceable AI launched Zero Trust API Access to help organizations better protect sensitive data, stop API abuse, and align data security programs with broader innovation and business objectives.
Halo Security detects exposed secrets and API keys in JavaScript
Halo Security has unveiled a new feature that helps security teams detect unintended exposures. Its agentless solution identifies secrets in scripts used across the attack surface, no matter how they’ve been added, so security teams know what is dangerous and what isn’t.
Eclypsium launches Supply Chain Security Platform with SBOM capability
Eclypsium released Supply Chain Security Platform, enabling an organization’s IT security and operations teams to continuously identify and monitor the bill of materials, integrity and vulnerability of components and system code in each device, providing insight into the overall supply chain risk to the organization.
Arista Networks unveils AI-driven network identity service
Based on Arista’s CloudVision platform, Arista Guardian for Network Identity (CV AGNI) expands Arista’s zero trust networking approach to enterprise security. CV AGNI helps to secure IT operations with simplified deployment and cloud scale for all enterprise network users, their associated endpoints, and Internet of Things (IoT) devices.