The Network’s Hidden Battlefield: Rethinking Cybersecurity Defense
Modern cyber threats are no longer knocking at the perimeter – they’re already inside. The traditional security paradigm has fundamentally shifted, and CISOs must adapt or risk catastrophic breaches. Network detection and response (NDR) isn’t just a technology upgrade – it’s a strategic imperative.
Brian Dye, CEO of Corelight, understands this landscape intimately. In an exclusive interview, he revealed the critical vulnerabilities lurking within enterprise networks and how advanced detection strategies can transform cybersecurity defense.
The Perimeter is Porous
Cybersecurity experts have long recognized that perimeter defenses are increasingly ineffective. Attackers have become sophisticated, leveraging complex techniques to bypass traditional security mechanisms.
“Current modern threats are bypassing traditional perimeter defenses,” Dye explained. “There’s been a huge rise in perimeter vulnerabilities, particularly in network device infiltration.”
The statistics are sobering. Major breach reports from Verizon and M-Trend consistently demonstrate that attackers are evolving faster than traditional security approaches can respond. What makes these modern attacks particularly dangerous? They’re using non-malware techniques, “living off the land” within network infrastructures, making detection exponentially more challenging.
The Open Source Advantage
Interestingly, Corelight’s approach stems from an open-source heritage – a strategy that provides unique insights and continuous innovation.
“The people who can deploy open-source technology are the most elite defenders in the world,” Dye noted.
These include web-scale tech giants, major financial institutions, and government entities who’ve been battling advanced threats for over a decade. This open-core model creates a continuous innovation flywheel.
Advanced attack detection techniques are developed, shared, and refined within a collaborative ecosystem.
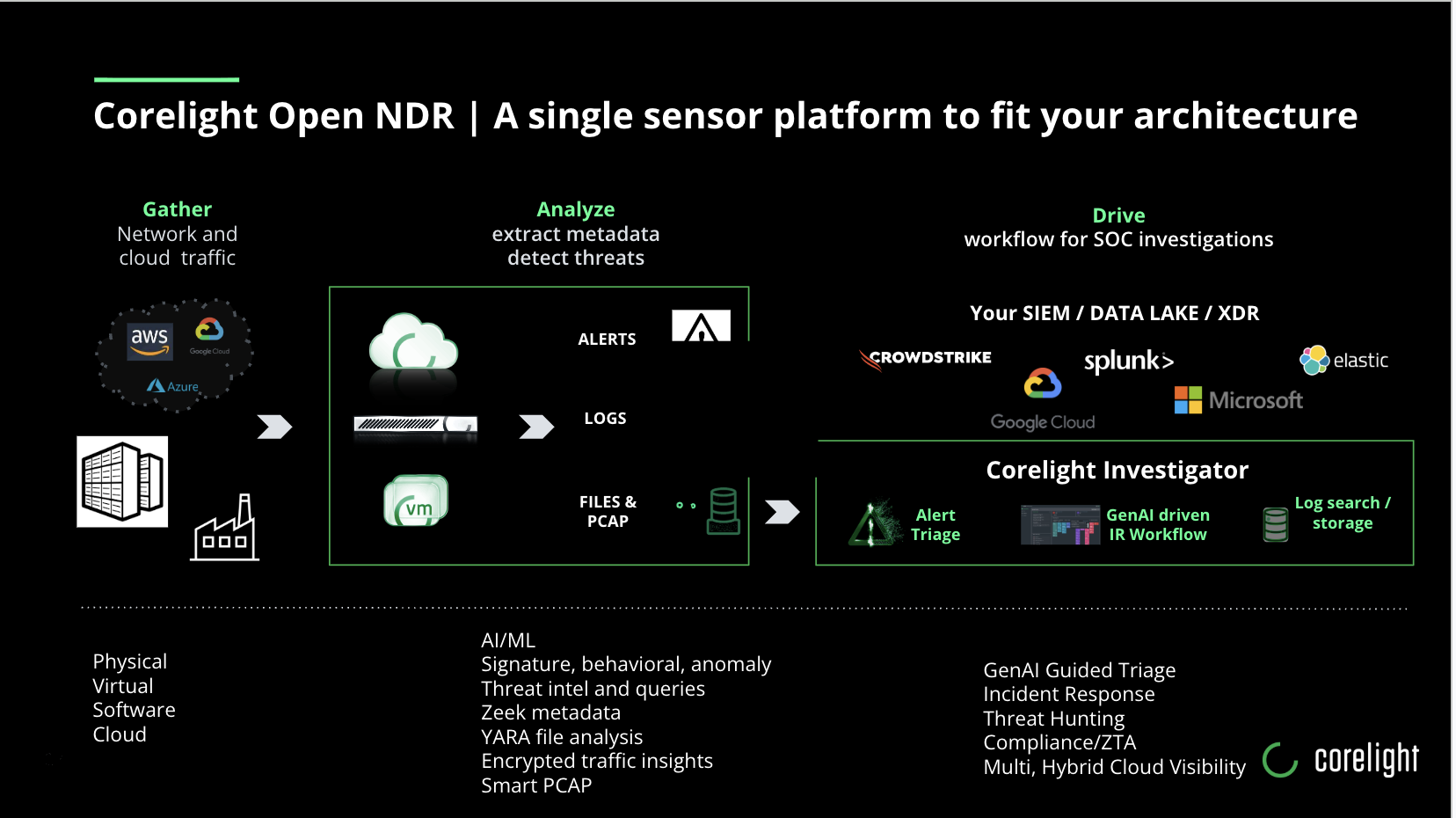
Three Pillars of Modern Network Defense
Corelight’s approach to network detection and response revolves around three critical strategies:
Understanding network traffic at a granular level provides the foundation for effective defense. By capturing and analyzing complete network interactions, security teams gain unprecedented insights.
Beyond traditional signatures, modern NDR leverages supervised and unsupervised machine learning to detect anomalous behaviors that might indicate potential threats.
Accelerating incident response isn’t just about detection – it’s about providing structured, actionable intelligence that enables rapid, precise interventions.
The AI Revolution in Cybersecurity
Artificial intelligence is transforming network defense, and Corelight is at the forefront of this revolution.
“We’re enabling the agentic SOC ecosystem,” Dye emphasized.
This means creating interconnected, intelligent systems that can collaborate, analyze, and respond to threats with unprecedented speed and accuracy.
Practical Use Cases
CISOs might wonder about real-world applications. Corelight’s customers have discovered innovative uses beyond traditional threat detection:
- Compliance Automation
- Quantum Readiness Monitoring
- Fraud Detection
- Zero Trust Architecture Support
The common thread? Generating “ground truth” data that provides comprehensive, actionable insights.
Corelight at Black Hat USA 2025
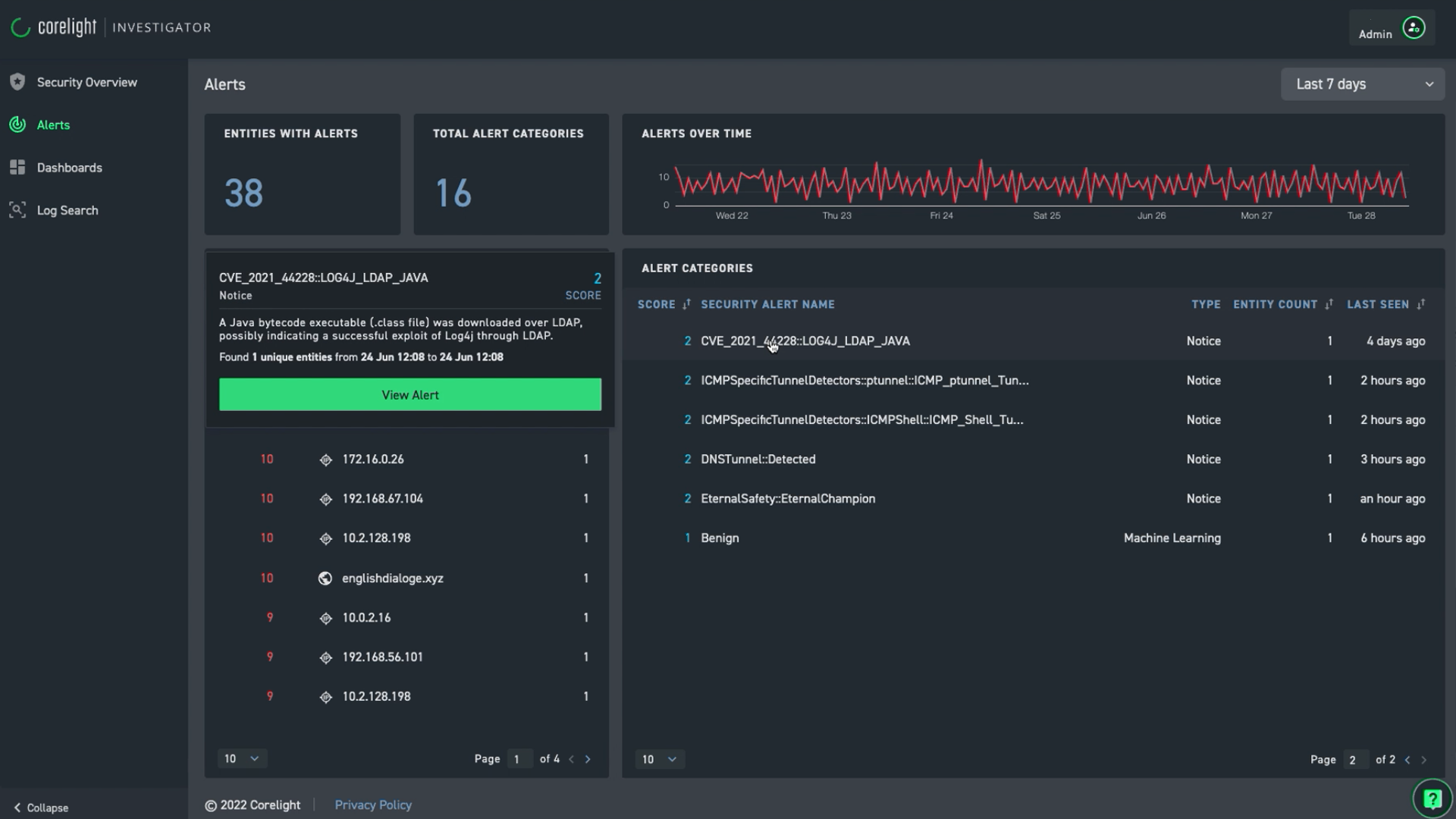
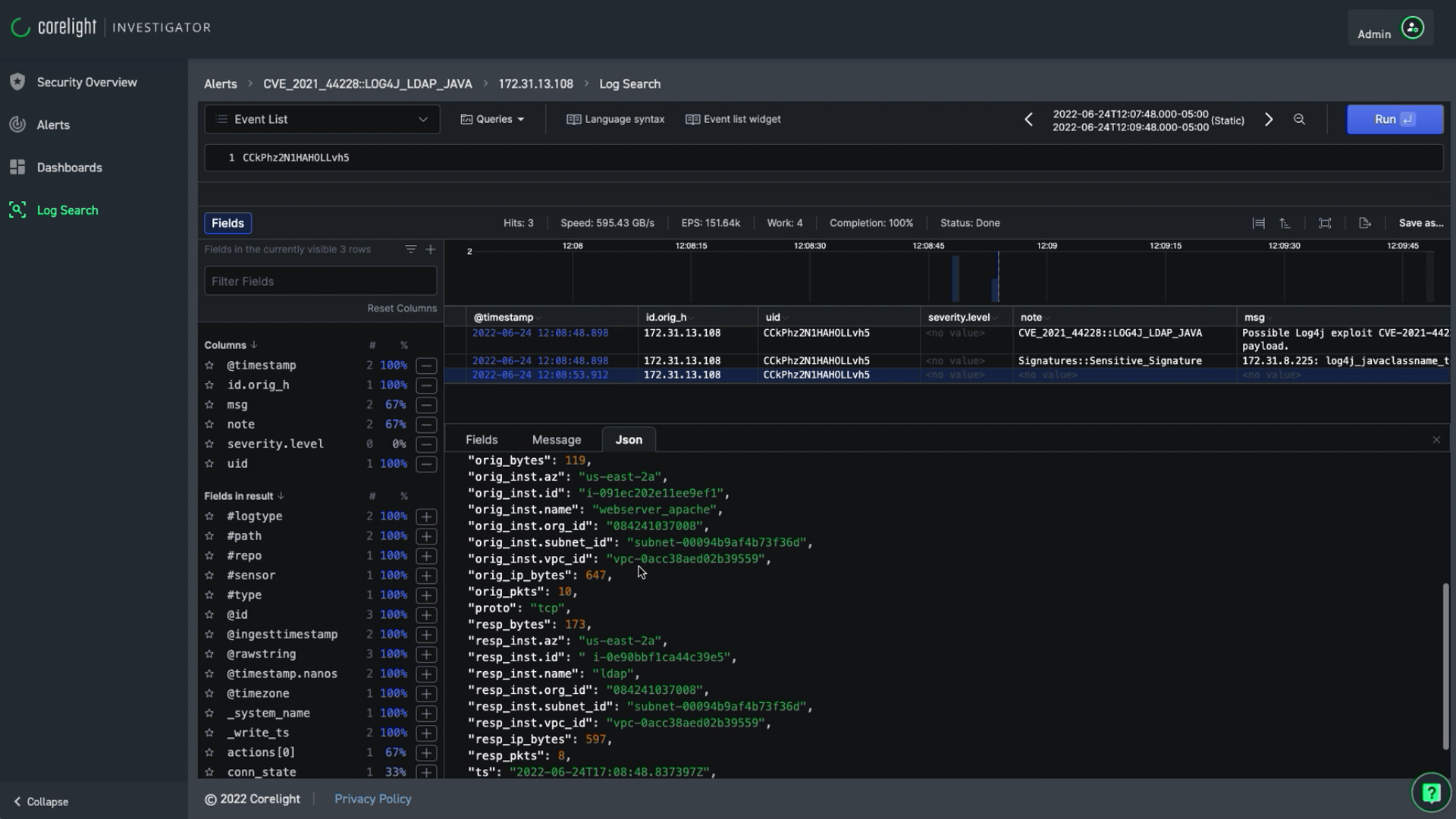
Corelight, the fastest-growing provider of network detection and response (NDR) solutions, announced a private preview of its GenAI Accelerator Pack. The pack combines industry-standard network evidence with large language models to accelerate and enhance security operations center (SOC) workflows. It includes a Model Context Protocol (MCP) server, Analyst Assistant Promptbooks, and Investigation Promptbooks.
Features of the GenAI Accelerator Pack
- MCP Server
Provides a simple interface for analysts or agents to access Corelight logs, alerts, and detections from the SIEM, including Splunk, Elastic, and LogScale. Dozens of prebuilt tools translate complex queries into clear, actionable insights using natural language. - Investigation Promptbooks
Offers more than a dozen investigation workflows that automate common alert types, with fully transparent reporting of each step taken during the investigation. - Analyst Assistant Promptbooks
Delivers a wide range of prompts to support day-to-day analyst tasks, from alert translation to payload and session summaries, along with other routine SOC activities.
A Call to Action for CISOs
The cybersecurity landscape demands immediate, strategic action.
Here are three (3) critical steps:
- Pay Attention to the Network
Revisit your network monitoring strategies. The pendulum of security innovation is swinging back to network-level visibility.
Whether leveraging vendor-provided AI or developing internal capabilities, engagement is no longer optional.
- Treat Data as a First-Class Asset
Your security data is not just a byproduct – it’s a strategic resource that fuels advanced defense mechanisms.
The Future of Network Defense
Looking ahead, Corelight is focused on three key developments:
- Enriching evidence and context
- Expanding detection coverage
- Developing trustworthy generative AI capabilities
Learn more at: https://corelight.com/
Author’s Note: This exclusive interview was conducted live at the 2025 Black Hat Conference in Las Vegas, providing unprecedented insights into the evolving cybersecurity landscape.
About the Author

Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.