LastPass Evolves Secure Access Experiences to Combat Shadow IT and AI Risks for CISOs
Picture your organization humming along, with teams adopting new apps to boost efficiency. But beneath that surface, unsanctioned tools creep in, exposing data and inflating costs. For CISOs like you, this shadow IT landscape demands smarter defenses. LastPass steps up with innovations that turn visibility into action, all without overwhelming your resources.
My previous exploration of secure access in a conversation with LastPass at the RSA Conference (RSAC) in San Francisco this year highlighted browser extensions as gateways to better control. Now, with SaaS Monitoring’s general availability and the debut of SaaS Protect, plus passkey support, LastPass builds on that foundation.
These tools address the sprawl of SaaS and AI apps directly, giving you the edge in a threat-filled environment. Shadow IT has long plagued mid-sized enterprises, where employees introduce apps without oversight.
Don MacLennan, Chief Product Officer at LastPass, captured this challenge earlier this year. “Small to mid-sized enterprises often have this problem of Shadow IT,” he explains. “Employees are putting business-critical data into SaaS applications that IT leadership may or may not have visibility into.”
His words ring true for many CISOs juggling limited budgets and growing risks.
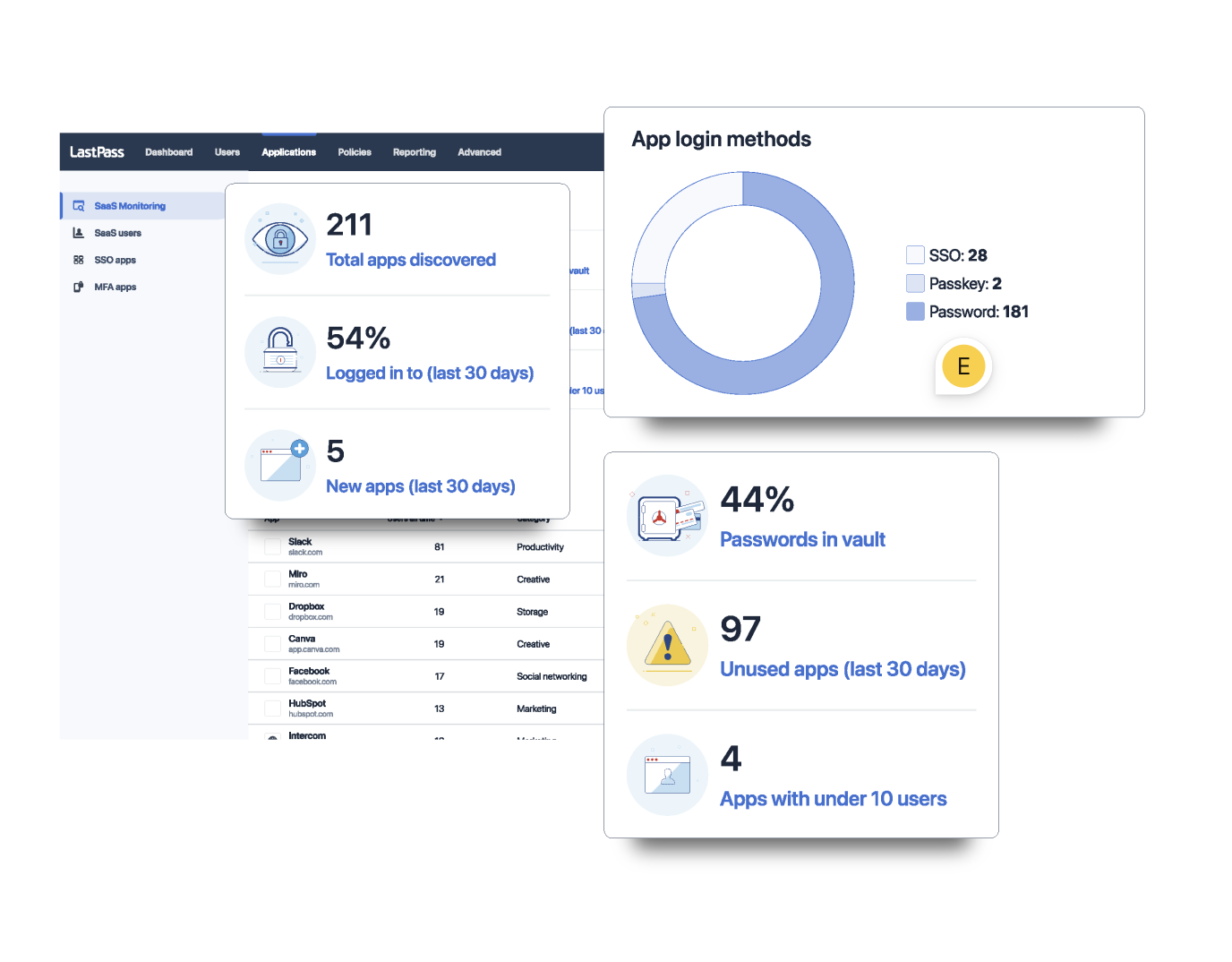
The response? LastPass launched SaaS Monitoring in RSAC, marking the start of their Secure Access Experiences initiative. This feature provides a clear view of your SaaS ecosystem through intuitive dashboards.
You can spot categories like productivity tools or AI chatbots, track access methods, and monitor adoption trends. No extra agents needed; it leverages the existing browser extension. Benefits extend beyond discovery.
SaaS Monitoring helps reduce costs by identifying duplicates and enforces credential hygiene by logging access patterns. For compliance, it prepares you for audits and disruptions.
Todd Thiemann, Principal Analyst at ESG, emphasized its value for smaller teams. “Without visibility into their SaaS ecosystems, SMB leaders risk security breaches from unauthorized access and rising costs from Shadow IT and Shadow AI,” he notes.
His insight underscores how LastPass fills a gap for resource-strapped organizations.
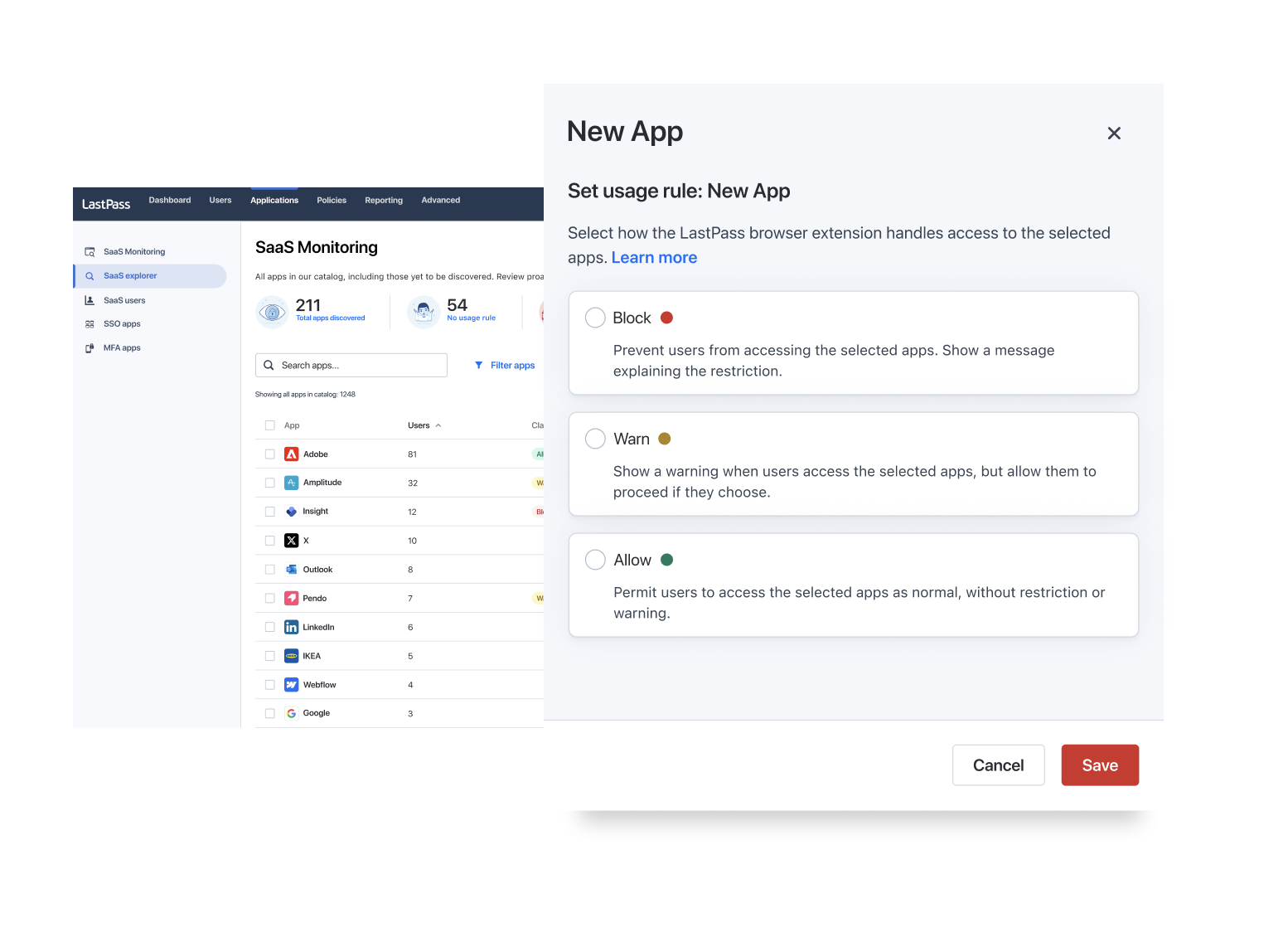
Building on this, LastPass unveiled SaaS Protect at Black Hat 2025 in August. This addition shifts from passive monitoring to active enforcement. You gain customizable policies, credential risk detection, and real-time reporting as well as restrict unsanctioned apps, issue warnings, and generate compliance-ready reports. All while optimizing SaaS spend by spotting over-licensed tools.
Don MacLennan described the urgency driving this feature. “Small and mid-sized businesses are facing a perfect storm of complexity: unknown risks living within unknown apps and AI services,” he says. “We built SaaS Protect to turn that chaos into clarity. It’s designed specifically for resource-constrained businesses that need visibility, policy enforcement, and credential protection without adding operational overhead.”
This proactive stance aligns with your need to block threats before they escalate. SaaS Protect integrates seamlessly with SaaS Monitoring, operating via the browser extension. Activity data flows to your admin console, enabling quick decisions.
For CISOs, this means addressing the 75 percent of employees Gartner predicts will use unauthorized tech by 2027. It tackles the IBM-reported $5.3 million average cost of data breaches from shadow IT.
Available in beta for Business and Business Max customers (with general availability reported in late August 2025), it’s included in the Business Max bundle at no extra cost.
This bundle combines password management, unlimited SSO and MFA, and now these monitoring tools. Passkeys represent another leap in LastPass’s strategy, launched in August 2025. These cryptographic key pairs replace traditional passwords, stored securely in your LastPass vault. They sync across devices, resisting phishing and breaches.
Don MacLennan highlighted their transformative potential. “Passkeys are changing how people log in, using a much more secure method,” he states. He added context on the implementation. “We’ve built support to store passkeys across platforms and without friction. It’s a smarter, simpler way to stay secure.”
For you as a CISO, passkeys reduce helpdesk tickets and enhance hygiene. With 92 percent of IT leaders believing they improve security posture, adoption makes sense and they can be used to provide management alongside passwords in one vault, without ecosystem lock-in. This fits the Secure Access Experiences framework, unifying visibility, hygiene, and control.
Recall the earlier vision: browser extensions evolving beyond password management. Now, with these updates, that vision materializes. You can discover 100 additional SaaS apps, sanction them, and block or warn on unsanctioned ones – as well as integrate threat feeds to prevent navigation to malicious sites.
The simplicity stands out: minimal configuration, immediate value, scalable for your team. In practice, this means evaluating your SaaS landscape becomes straightforward. Assessing employee usage, exploring browser-based solutions, and scheduling assessments becomes easy. The narrative shifts from reactive firefighting to strategic leadership.
Don MacLennan envisioned future enhancements. “We could imagine linking this to threat feeds,” he says, “so that if an employee is about to navigate to a malicious site or phishing credential harvesting site, we would provide a front-end feed to stop them from coming into contact with harm’s way.”
Such foresight positions LastPass as a partner in your cybersecurity journey. For CISOs in sectors like healthcare or finance, where compliance is non-negotiable, these tools ensure audit readiness.It now becomes a no-brainer to generate reports aligned with SOC 2 and other frameworks.
MacLennan highlighted their transformative potential. “Passkeys are changing how people log in, using a much more secure method,” he states. He added context on the implementation. “We’ve built support to store passkeys across platforms and without friction. It’s a smarter, simpler way to stay secure.”
For you as a CISO, passkeys cut down on helpdesk calls and boost overall security hygiene, with 92 percent of IT leaders seeing them as a posture improver, making the switch feel like a no-brainer.
You manage them right alongside passwords in a single vault, free from any platform lock-in, and this ties neatly into the Secure Access Experiences framework, pulling together visibility, credential strength, and smart controls.
Now, with these pieces in place, recall that earlier vision of browser extensions doing more than just filling passwords; it’s reality – where you discover hidden apps, set policies, and block risks in real time, turning shadow IT from a lurking danger into something you command.
In sectors where compliance can’t slip, like healthcare or finance, these features keep you audit-ready, letting you pull reports that align with SOC 2 standards without breaking a sweat.

On the cost side, you can optimize amid tech sprawl, where Zylo reports small businesses use 275 known SaaS apps but oversee only 26 percent of the spend, and shadow AI adds another layer. Tools like chatbots introduce risks that SaaS Protect’s real-time governance guides against without disrupting workflow.
Custom warnings educate users, fostering a security-aware culture that balances security with user experience, which is crucial for retention and productivity.
As digital threats evolve, so must your strategies, and LastPass’s innovations provide that evolution, tailored for mid-sized enterprises.
MacLennan summed up the broader impact. “SaaS Monitoring gives businesses something they’ve been missing – visibility and control,” he explains. “In their efforts to enhance productivity, employees often turn to SaaS and AI tools outside of company policies. This Shadow IT usage can result in cost overruns and business-critical data exposures. SaaS Monitoring from LastPass is an affordable, easy-to-deploy capability that gives businesses the visibility they need to identify unnecessary risks and curb spending.”
His perspective resonates with the daily battles you face, and integrating passkeys further strengthens this by storing private keys encrypted in the vault to mitigate server-side risks, while users authenticate via biometrics or devices, streamlining access and reducing phishing vulnerabilities, a top concern for CISOs.
LastPass’s FIDO2 certification underscores their commitment, and combined with SaaS tools, it forms a comprehensive defense.
The user dashboard in SaaS Monitoring details login methods, devices, and timestamps, letting you spot anomalies quickly to enhance threat detection, and for continuity planning, you identify critical apps so in disruptions, you know what’s essential.
This proactive mindset shifts you from defender to strategist, and the conversation around access management changes.
Are you leading it?
With LastPass, you can.
Their Secure Access Experiences initiative democratizes advanced security with no heavy deployments, just effective tools that let CISOs focus on high-level responsibilities, not minutiae.
The roadmap excites with threat feed integration and expanded controls to stay ahead of the curve.
MacLennan described a practical scenario. “Imagine we discovered 100 additional SaaS apps for a customer,” he describes, “and an administrator can mark which are sanctioned and which are not, with the ability to warn or block access to unsanctioned applications.”
This level of control empowers your team, and privacy remains protected since monitoring captures only business usage via company emails, with no personal data intrusion, building trust within your organization.
As you discharge cybersecurity responsibilities, these tools align with your goals to protect data, ensure compliance, and optimize resources, marking the era where clunky solutions fade and simplicity reigns.
Zscaler might suit enterprises, but for mid-sized, LastPass fits as affordable, powerful, and user-friendly.
LastPass’ Black Hat 2025 debut showcased this live, with attendees seeing demos that sparked discussions, and for those not there, updates are available, including passkeys that were highlighted with general availability following beta for seamless access across platforms.
Your multi-device workforce benefits as you reduce password fatigue and cut risks, and IT leaders agree this leads to improved posture ahead. Weave these into your strategy by evaluating current tools and assessing gaps, since LastPass offers a path forward.
This narrative weaves from visibility to enforcement to future-proofing, transforming shadow IT from threat to managed asset, and CISOs like you drive this change.
Ready to explore?
Take the next step: visit LastPass for a demo or sign up for updates. Transform your access management today. Secure your organization’s future.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company and co-author of “The vCISO Playbook: How Virtual CISOs Deliver Enterprise-Grade Cybersecurity to Small and Medium Businesses (SMBs)”. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company and co-author of “The vCISO Playbook: How Virtual CISOs Deliver Enterprise-Grade Cybersecurity to Small and Medium Businesses (SMBs)”. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.




