Cybersecurity’s Dirty Little Secret: Reimagining Isolation – How Replica Cyber Empowers CISOs with Secure Environments in Seconds
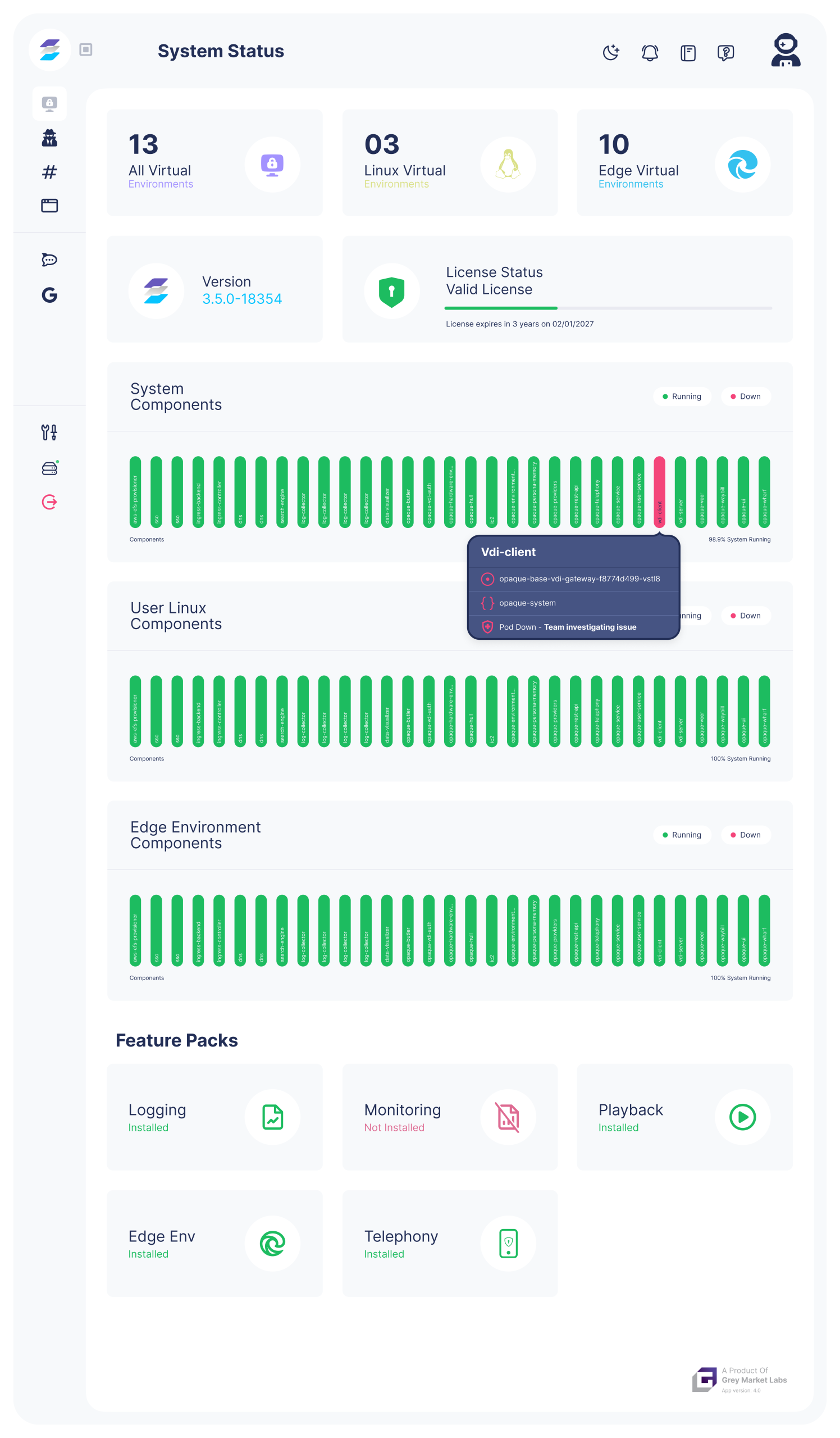
Imagine creating a completely secure, fully configured digital workspace in minutes instead of months. Replica Cyber does exactly that – providing organizations with instant, automated secure environments that can be spun up for any digital task, from sensitive research to critical software development. As organizations experiment with powerful, yet unproven AI models and tools, Replica provides the isolation and control needed to safely explore, test, and develop AI without risking exposure, IP theft, or system compromise.
This isn’t cloud hosting.
This isn’t traditional desktop-as-a-service.
This is a comprehensive zero-trust isolated environments platform that gives CISOs unprecedented control and flexibility.
Kris Schroeder, CEO of Replica Cyber, understands this paradox intimately.
“Every tool we trusted failed us at the worst possible moment. In our world, that didn’t just mean data loss – it meant lives on the line.”
He and co-founder Ryan Underwood spent decades protecting U.S. national security. Time after time, even the most hardened “secure” tools betrayed users in the field.
The Traditional Cybersecurity Trap
For years, CISOs have been sold a narrative of protection through isolation. Build higher walls. Create more barriers. Restrict everything. The result? A sprawling, rigid stack that inhibits agility while still leaving gaps.
Replica Cyber emerged from a fundamental rebellion against this model. Schroeder and his co-founder Ryan Underwood weren’t just building another security tool – they were reimagining how organizations interact with digital risk.
“We’re not traditional cyber red team people,” Schroeder emphasizes. “We’re mission-focused people, operations and outcomes-focused people.”

New Security Paradigm for Mission-Driven Innovation:
What sets Replica Cyber apart is its reimagining of what secure workspaces can be. Ryan Underwood describes it as more than just another desktop solution:
“These aren’t locked-down desktops or gated sandboxes – they are full computing environments engineered to accelerate secure missions and foster innovation without introducing risk.”
Key differentiators include:
- Total Isolation: Fully detached from enterprise or personal networks
- Instant Deployment: Mission-ready workspaces in minutes
- AI-Safe Experimentation: Isolated environments to test models, agents, or tools
- Operational Stealth: Realistic personas and regional network simulation
- Flexible Infrastructure: Multi-cloud orchestration with mission-tuned apps and workflows
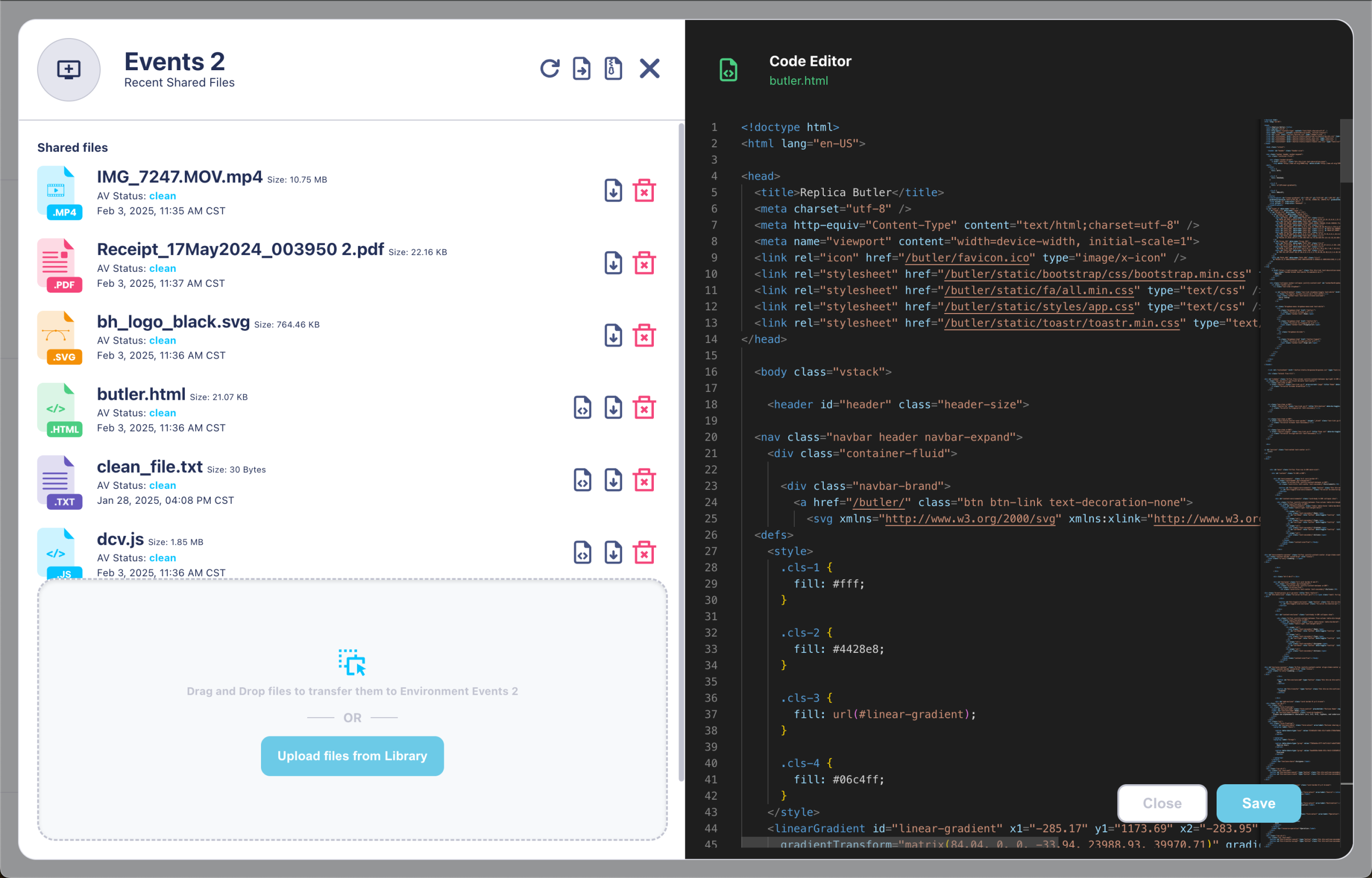
- Secure Collaboration: Seamlessly exchange sensitive data without compromising security
Breaking the Cost Center Mentality
Perhaps most revolutionary is Replica Cyber’s potential to transform cybersecurity from a cost center to a business enabler.
“The CISO and CTO shops are moving from ‘How did you protect me?’ to ‘What did you enable our business to do?’” Underwood explains.
That shift is reflected in outcomes. In one case, a global consulting firm’s CTO was stunned when Replica Cyber created complex lab environments in a week – something that would have traditionally taken millions of dollars and months of work.
Built for the Modern Threat Landscape: Replica isn’t a niche tool. It’s the platform behind high-risk, high-impact work, including:
- Threat intel and dark web operation
- Malware detonation and sandboxing
- End-to-end M&A, from due diligence to secure integration
- Secure R&D and DevOps
- Experimental AI model training and deployment
Today, generative AI and machine learning are reshaping innovation, but they also introduce unprecedented security risks. Proprietary models, training data, and novel agents are high-value targets. Replica provides an ideal environment for testing and deploying these tools without risking enterprise infrastructure or user exposure. Whether you’re running LLMs behind the firewall or integrating experimental agents, Replica keeps the development invisible, secure, and compliant.
AI: The Next Frontier of Secure Environments
With AI integration baked into their approach since 2018, Replica Cyber is thinking several moves ahead.
“How we implement AI,” Schroeder notes, “is about making complex tasks simple.”
The vision? Environments where sophisticated security configurations can be established through natural language interactions, eliminating the need for extensive coding knowledge. This capability transforms the way analysts and engineers work – lowering barriers to advanced operations while maintaining strict isolation and control.
Practical Implications for CISOs
For security leaders evaluating Replica Cyber, the platform offers compelling advantages:
- Deploy Faster: Reduce lead times from weeks to minutes
- Cut IT Burden: Zero-touch environments that scale
- Increase Visibility: Full audit trails, screen recording, logging
- Mitigate Risk: Operate without attribution or exposure
- Fuel Innovation: Enable rapid, secure experimentation
Call to Action
The digital landscape doesn’t care about your comfort zone.
It evolves, mutates, and challenges every assumption about security and innovation.
Replica Cyber isn’t offering a product – it’s offering a strategic weapon.
Your choice is binary: Adapt or become obsolete.
Twenty patents. Countless hours of real-world cybersecurity experience. One fundamental truth: Protection isn’t about building walls. It’s about creating intelligent, responsive environments that anticipate threats before they emerge.
Replica Cyber doesn’t just secure your digital ecosystem. It transforms it. The next chapter of your organization’s digital strategy starts now.
More information can be found at replicacyber.com.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.
