A previously unknown traffic distribution system (TDS) named ‘VexTrio’ has been active since at least 2017, aiding 60 affiliates in their cybercrime operations through a massive network of 70,000 sites.
Traffic Distribution Systems (TDS) are services that take incoming traffic and redirect the user to another website depending on the visitor’s operating system, IP address, device, geographic region, and other criteria.
For legitimate reasons, a TDS is commonly used in affiliate marketing. However, in cybercrime, they redirect unsuspecting users to malicious destinations like phishing pages, exploit kits, and malware-dropping sites.
One such case is Parrot TDS, highlighted recently in a Unit 42 report that presented evidence of the operation remaining active and developing.
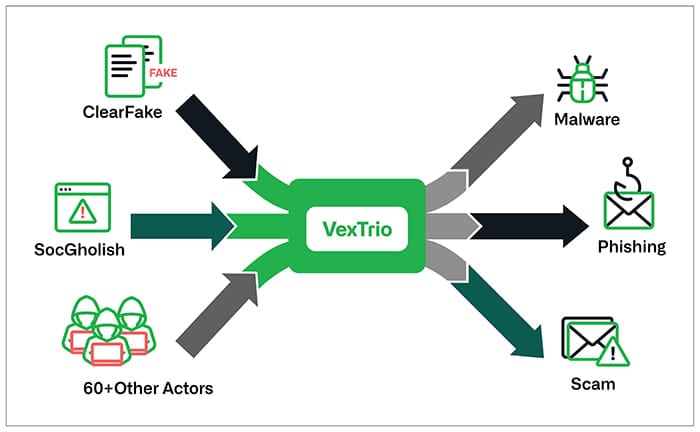
A new report by Infoblox focuses on a much larger-scale TDS operation named VexTrio, which works with notorious cybercrime campaigns and operators like ClearFake and SocGholish, among others.
Serving cybercrime since 2017
VexTrio has been identified by Infoblox as a highly pervasive entity within the cybercrime landscape, commanding a massive network that plays a central role in the distribution of malicious content.
VexTrio controls over 70,000 compromised sites, a testament to its extensive reach, enabling the platform to distribute malicious content to visitors across a wide array of websites and services.
Typically, sites are hacked to inject malicious redirection scripts into the HTML of vulnerable sites. In other cases, the threat actors simply create their own websites and utilize blackhat SEO tactics to generate traffic.
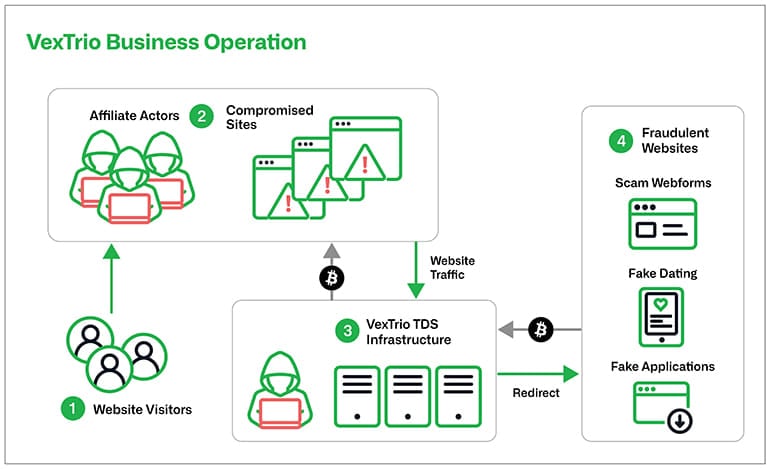
The platform acts as an intermediary traffic broker in exchange for money from cybercrime groups, redirecting visitors of the sites under its control to customers’ malicious destinations.
VexTrio also extends its reach by partnering with at least 60 entities, or affiliates, who forward traffic from their resources, such as compromised websites, to VexTrio’s TDS servers.
Source: Infoblox
Infoblox notes that these partnerships do not appear short-lived, as they observed cases that extended for up to four years, showing a high level of trust and mutual benefit.
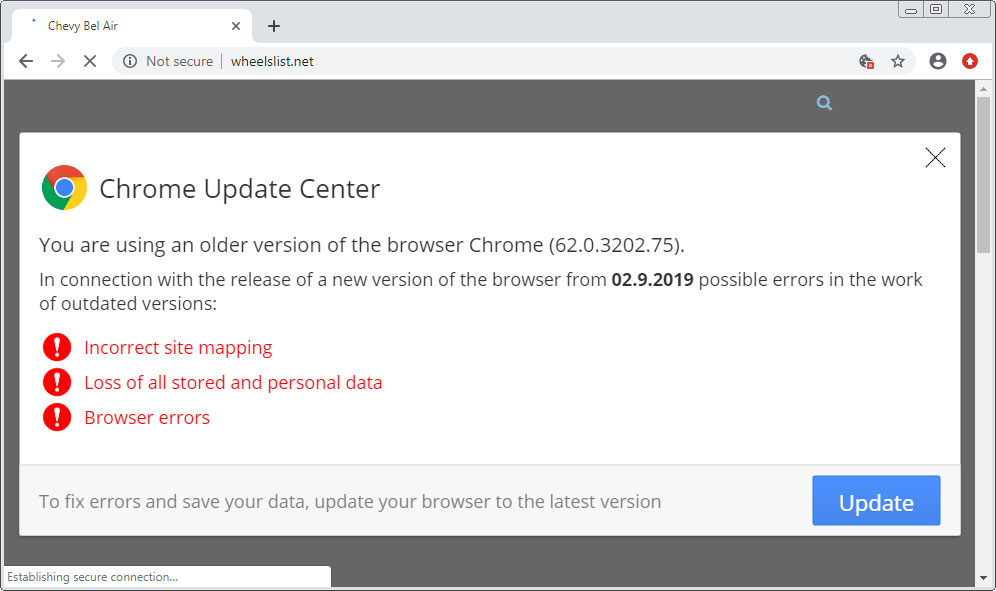
One of VexTrio’s partners is ClearFake, a malware campaign that displays prompts on hacked sites telling visitors to install fake browser updates, which install malware on the device.
ClearFake has been a VexTrio affiliate for five months, but instead of directly forwarding traffic to the platform’s TDS servers, it uses the Keitaro service as an intermediate redirection point.
The SocGholish malware campaign has also collaborated with VexTrio since at least April 2022, according to Infoblox, also relying on the Keitaro TDS service for a midpoint bounce. Historically, SocGholish was used by ransomware gangs to gain initial access to corporate networks.
Source: BleepingComputer
The variety and complexity in the attack chains, which involved multiple threat actors, make VexTrio activity hard to map, detect, and mitigate.
Diverse revenue sources
Moreover, the analysts have found that VexTrio and its affiliates often abuse referral programs from legitimate platforms to generate revenue by redirecting victims to trusted sites via affiliate links.
By intertwining their operations with legitimate services, VexTrio and its affiliates make it more challenging for both users and security systems to discern their malicious activities.
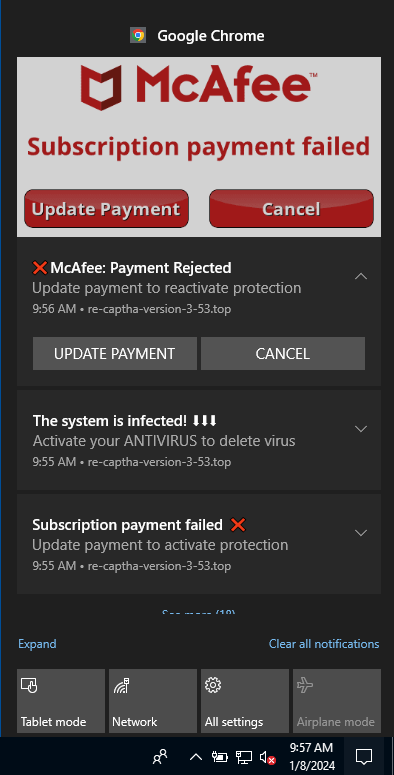
Infoblox’s report highlights a cunning and deceptive VexTrio campaign named ‘robot CAPTCHA,’ which the group uses in its referral generation efforts.
In this campaign, users visiting compromised sites are redirected to what appears as a legitimate CAPTCHA test, which tricks the user into clicking an ‘Allow’ button, inadvertently granting the website permission to send push notifications through the user’s browser.
Then, VexTrio’s servers can push bogus notifications to the victim anytime, masquerading as system warnings, AV alerts, and other seemingly credible alerts. VexTrio even ensures those alerts are in the correct language by using JS modules to dynamically adjust the language based on the user’s browser data.
Source: Infoblox
Clicking on the deceptive notifications may lead victims to landing pages that generate referral revenue for VexTrio.
Considering the complexity, resilience, and diversity in revenue streams and infection chains, VexTrio will be very hard to eradicate, although identifying and mapping its sites is a solid first step.
Infoblox suggests that users mitigate the threat by limiting their browsing only to SSL-certified sites, blocking push notifications on their browsers, and using ad-blocking tools that can prevent popup ads from loading.
