A severe security vulnerability in the Insomnia API Client, a widely used tool by developers and security testers for interacting with APIs, has been uncovered by researchers at an offensive security consultancy.
Discovered by Technical Director Marcio Almeida and Head of Research Justin Steven, the flaw allows for arbitrary code execution through a mechanism known as Client-Side Template Injection (CSTI).
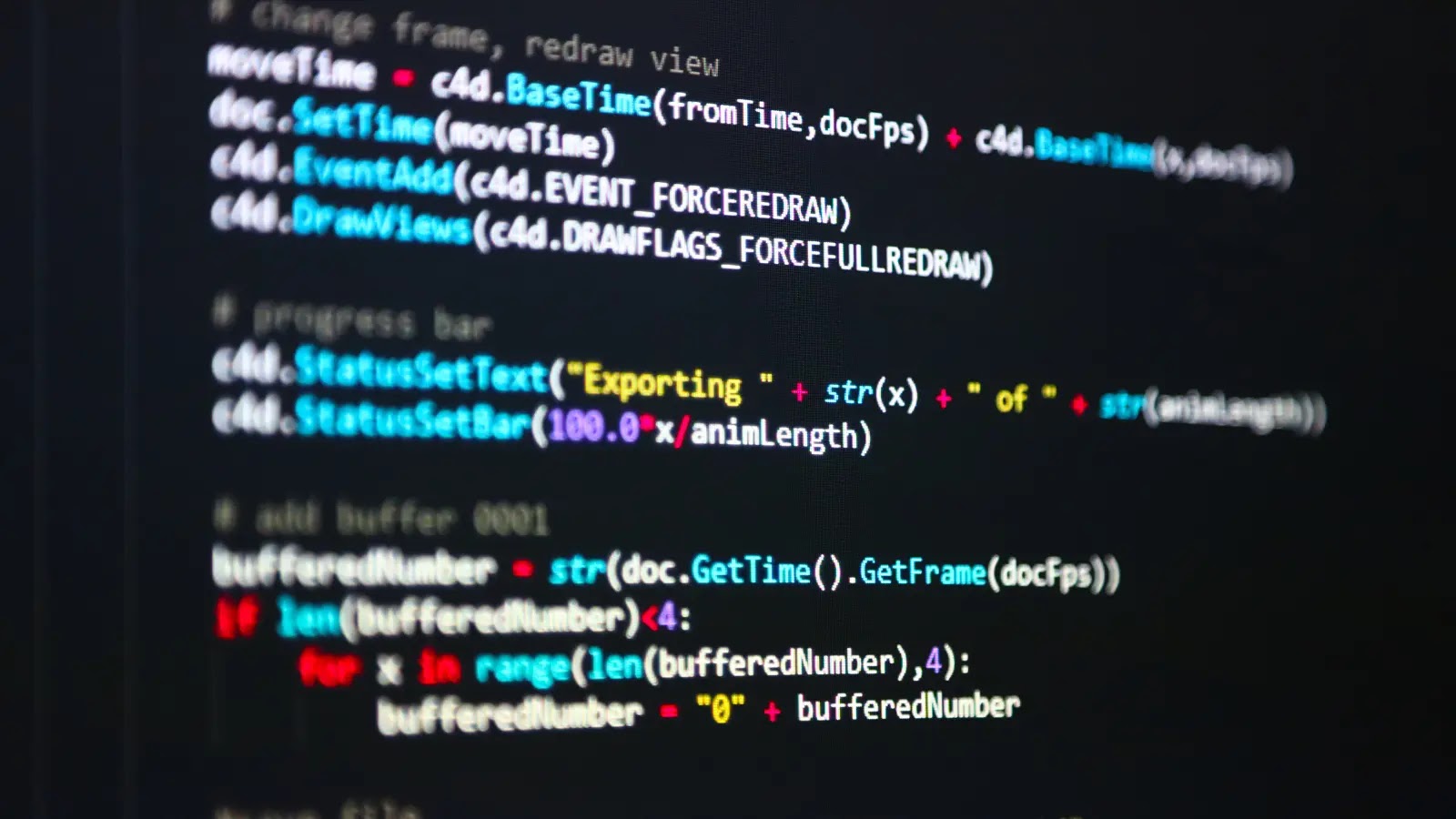
This critical issue, which persists in the latest version (11.2.0) as of June 2025, stems from Insomnia’s use of the Nunjucks templating engine, which processes untrusted input in a way that can be exploited by malicious actors.
The vulnerability, assigned CVE-2025-1087 with a CVSS score of 9.3, poses a significant risk to users handling untrusted files, data, or HTTP responses, potentially leading to complete system compromise.
Multiple Mitigation Attempts Bypassed
The issue was first identified during an API penetration test when Almeida noticed unexpected behavior in Insomnia: a template expression like {{7*7}} was locally evaluated to 49 before being sent to the target server, revealing a local template rendering flaw.
Further investigation confirmed that Insomnia’s environment variable feature, which relies on Nunjucks, enables attackers to inject malicious template strings via multiple vectors, including imported collection files, pasted data in UI fields (e.g., URLs or query parameters), and server-provided cookies via HTTP responses.
By crafting a payload leveraging Nunjucks’ global functions like joiner.constructor, attackers can execute arbitrary commands such as exfiltrating sensitive data or installing malware often with minimal user interaction.
A particularly alarming exploitation method involves setting a malicious cookie through the Set-Cookie header, which, when rendered by Insomnia during subsequent requests, triggers code execution remotely without user prompting.
Critical Flaw in Popular API Tool
Efforts by Kong, the creators of Insomnia, to mitigate this flaw have been repeatedly bypassed.
Initial attempts in versions 11.1.0 and 11.2.0, including sandboxing template rendering in a Web Worker and patching out specific Nunjucks functions like range, were circumvented using alternative methods such as module.require and joiner.constructor.
Despite collaborative reporting by the researchers starting in February 2025, and multiple rounds of feedback on bypasses, Kong has not fully resolved the issue, nor issued a comprehensive user-facing security notice beyond the CVE entry, which inaccurately suggests the flaw is fixed in version 11.0.2.
This ongoing vulnerability, known publicly since 2020 via a GitHub issue, underscores the dangers of using feature-rich templating engines with untrusted input and the challenges of retrofitting security into complex software architectures.
Given the persistent exploitability, users are strongly advised to exercise caution.
Avoid importing untrusted Insomnia files, inspect data for template expressions (denoted by {{double curly braces}}) before pasting into fields, and limit HTTP requests to trusted servers to prevent exposure to malicious cookies.
Disabling cookie storage on a per-request basis or patching out Nunjucks rendering, as suggested by the researchers, are potential workarounds, though they come with caveats regarding functionality.
As tools like Insomnia are integral to API development and security testing, this incident highlights the critical need for robust security in developer tooling, urging users to stay vigilant and prioritize updates while awaiting a definitive fix from Kong.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates