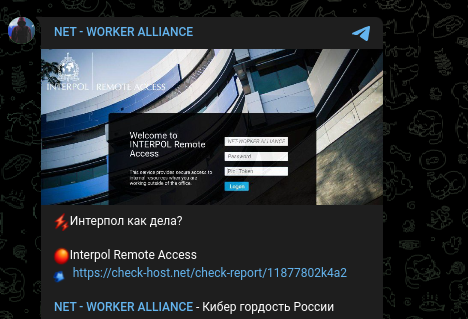
The NET-WORKER ALLIANCE, a relatively obscure threat actor, has claimed responsibility for the INTERPOL Remote Access data breach. This claim was posted on their secretive dark web channel.
The claim made by NET-WORKER ALLIANCE included a screenshot of the compromised INTERPOL Remote Access website and a check-host link, intended to solidify their claims of successfully breaching INTERPOL’s remote access portal. The motive behind this attack remains unclear.
The Cyber Express has reached out to INTERPOL for further insights into this alleged INTERPOL Remote Access data breach. We will update this report on receiving their response.
INTERPOL Remote Access Data Breach, Rise of NET-WORKER ALLIANCE
It is worth noting that this isn’t NET-WORKER ALLIANCE’s first foray into cyberattacks.

The group previously gained popularity when it claimed responsibility for a cyber assault on Poland, specifically targeting critical institutions such as the Warsaw Stock Exchange (GPW), Warsaw Chopin Airport (WAW), PGZ Stocznia Wojenna, and Port of Gdynia Authority S.A.
The Warsaw Stock Exchange, a linchpin of Poland’s financial landscape, was also added to the cyber attack, as did the Warsaw Chopin Airport, a vital travel hub.
The impact on significant maritime organizations, including PGZ Stocznia Wojenna and Port of Gdynia Authority S.A., was equally concerning.
However, the motives driving these attacks remain shrouded in mystery, as NET-WORKER ALLIANCE’s true intentions continue to elude scrutiny.
In a concerning parallel, NET-WORKER ALLIANCE has also claimed to have targeted the website of Europol in a separate attack.
Much like their modus operandi in the INTERPOL Remote Access breach, this assault featured an image of the EUROPOL website and a check-host link to substantiate their claims.
Hackers using Interpol to launch phishing attacks
In a prior incident, INTERPOL had reported an online phishing attack in which malicious actors exploited INTERPOL’s name to deceive victims into divulging sensitive information.
INTERPOL quickly clarified that it never directly contacts members of the public, requests money from individuals, or solicits bank details or funds transfers.
The organization cautioned the public against falling prey to scams that misuse its name, emphasizing that such fraudulent activities are designed to deceive individuals into sending money to scammers who leverage INTERPOL’s name for a veneer of legitimacy.

These scams have taken various forms, with perpetrators sometimes impersonating INTERPOL’s Secretary General, Jürgen Stock, in an attempt to intimidate victims. INTERPOL has reiterated that it does not maintain a database of hacked individuals or contact individuals in such databases.
Furthermore, it does not issue any form of authorization letter related to unlocking funds.
As the INTERPOL Remote Access data breach investigation unfolds, organizations and individuals alike must prioritize cybersecurity practices to protect their digital assets and personal information.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.