Security researcher has revealed a robust method for gathering threat intelligence on Cobalt Strike beacons using Shodan and PowerShell, filling the gap left by the popular @cobaltstrikebot Twitter account that went offline in June 2023.
The technique allows security professionals to independently collect valuable configuration data from active Cobalt Strike servers, specifically focusing on beacon SpawnTo values and watermarks – critical artifacts for detection and attribution.
The researcher outlines that accessing this threat intelligence requires at minimum a Shodan “membership” account, which costs approximately $50 as a one-time fee.
This basic membership level enables users to utilize the crucial search filter “product:Cobalt Strike” that identifies active Cobalt Strike command and control servers.
What makes this approach particularly valuable is that Shodan automatically queries beacon configurations from these servers and presents them as banner information within search results.
The awesome part about this data being captured and presented is that we can hit the download button and get it all into a compressed JSON file for processing.
After executing the search, researchers can download approximately 500 beacon configurations in compressed JSON format either through the web interface or via the Shodan CLI tool using the command: shodan download beacon_data product:"Cobalt Strike".
The researcher notes that while not all configurations will parse cleanly, the volume of data provides substantial intelligence value for security teams.
The most challenging aspect of the process involves parsing the Cobalt Strike configurations.
According to the researcher, JSON parsing presented numerous difficulties in Python, leading to the development of a combined approach using the Shodan CLI tool and PowerShell.
After initializing the CLI tool with an API key, users can extract just the beacon configuration information using: shodan parse --fields cobalt_strike_beacon.x86 .beacon_data.json.gz > beacon_data.json.
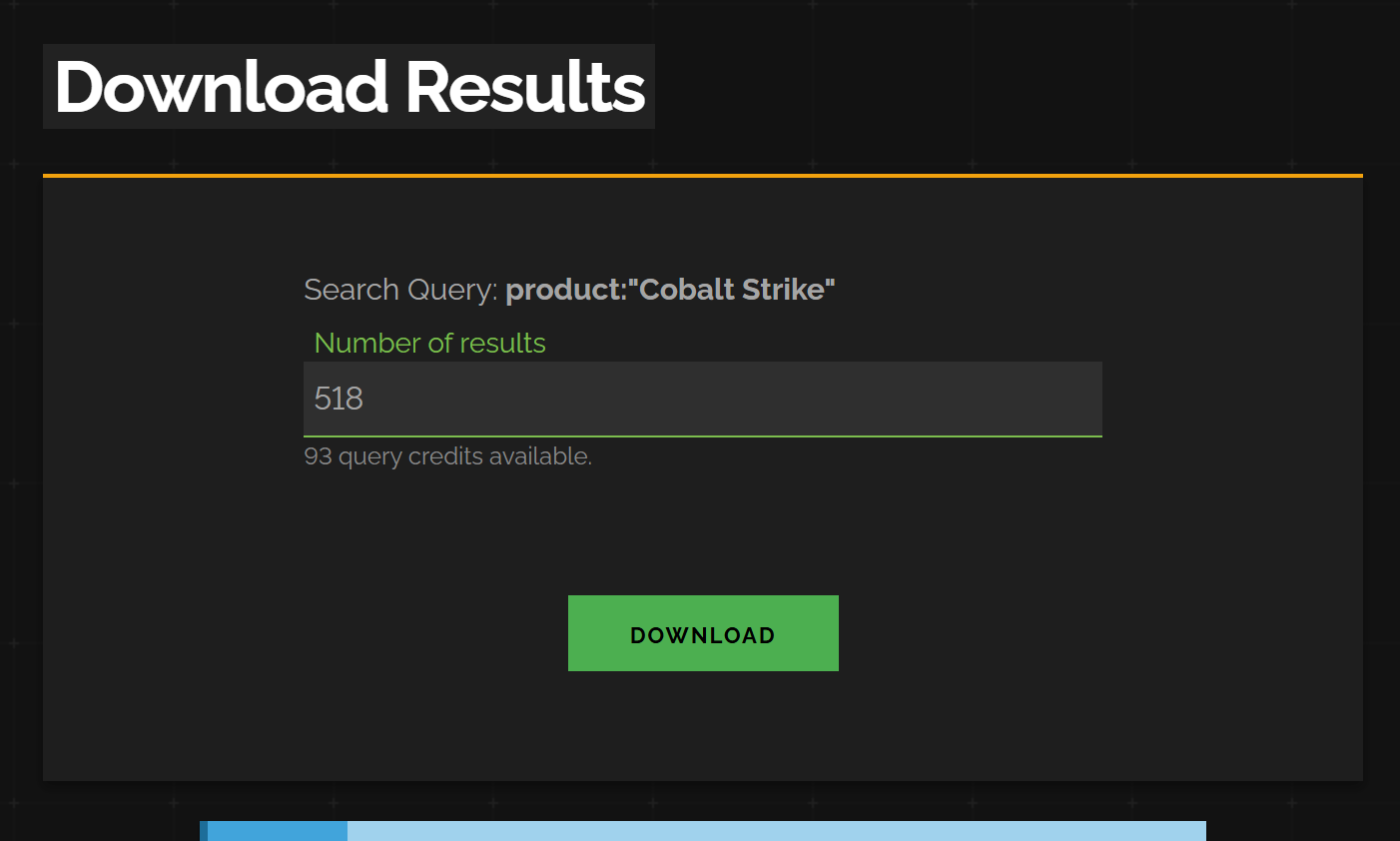
When downloading via the web interface, the file will get a goofy GUID for a name, I recommend changing it to something memorable like beacon_data.json.gz.
The researcher provides a PowerShell script that processes this data to extract two critical intelligence elements: SpawnTo values and watermarks.
The script organizes these values into arrays that can be sorted by prevalence.
The analysis reveals that the most common SpawnTo values are “%windir%syswow64rundll32.exe” and “%windir%sysnativerundll32.exe,” while popular watermarks include “987654321” and “666666666” – the former being associated with pirated versions of Cobalt Strike.
Practical Applications for Security Teams
These extracted data points offer significant value for security professionals developing detection rules.
For instance, the researcher demonstrates how SpawnTo values can be incorporated into Sigma rules to detect suspicious process executions, such as dllhost.exe running without command line parameters.
The watermark values provide additional intelligence for attribution, with some values being linked to specific threat actors or campaigns, such as watermark “391144938” which corresponds to activities in the Asian gambling sector according to previous threat research.
The researcher notes that several Sigma rules leveraging these insights already exist in the SigmaHQ repository, highlighting the practical application of this intelligence gathering method.
By continuously monitoring and analyzing these configurations, security teams can stay ahead of adversaries using Cobalt Strike in their operations, effectively replacing the intelligence previously provided by automated services like @cobaltstrikebot.
Through this methodology, security professionals gain independent access to valuable threat intelligence that can improve detection capabilities and enhance understanding of adversary tradecraft in the wild.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
