The Iranian threat group Educated Manticore, also tracked as APT35, APT42, Charming Kitten, or Mint Sandstorm, has intensified its cyber-espionage operations targeting Israeli cybersecurity experts, computer science professors, and journalists.
Associated with the Islamic Revolutionary Guard Corps’ Intelligence Organization (IRGC-IO), this advanced persistent threat (APT) group has been under scrutiny by Check Point Research for several years.
Spear-Phishing Campaigns
Since mid-June 2025, the group has launched sophisticated spear-phishing campaigns, impersonating fictitious employees of cybersecurity firms to deceive high-profile individuals from leading Israeli universities.
These attacks often begin with polished emails or WhatsApp messages that leverage AI-assisted writing for credibility, though subtle discrepancies, such as mismatched sender names, have occasionally exposed their fraudulent nature.

Educated Manticore’s tactics rely heavily on custom phishing kits designed to mimic legitimate authentication flows for services like Google, Outlook, and Yahoo.
These kits, built as React-based Single Page Applications (SPAs), use obfuscated code and dynamic routing to render authentication steps without page reloads, enhancing their deceptive appearance.
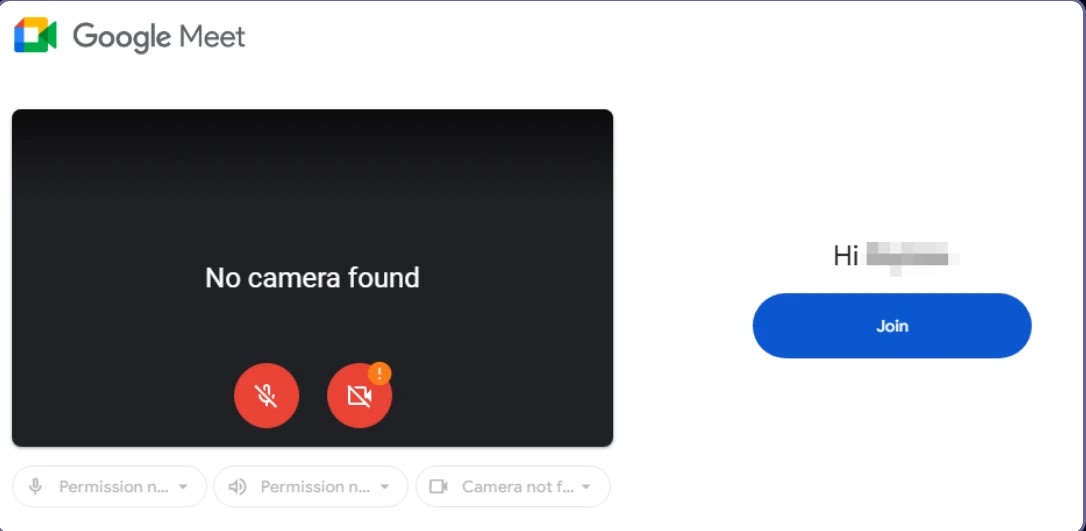
Victims are lured to fake Gmail login pages or Google Meet invitations after initial contact, where their email addresses are pre-filled to boost trust.
Advanced Phishing Kits
The phishing infrastructure supports complex authentication mechanisms, including two-factor authentication (2FA) relay attacks, capturing passwords, SMS codes, and even keystrokes via a real-time WebSocket keylogger.
Since January 2025, over 130 unique domains and numerous subdomains, mostly registered through NameCheap, have been linked to this campaign, resolving to a dozen IP addresses. Some of these align with the GreenCharlie sub-cluster, indicating a broader network of malicious infrastructure.
The group’s use of Google Sites to host multi-stage phishing pages further adds legitimacy by exploiting the trusted Google domain.
According to the Report, Once victims interact with fake meeting invitations, they are redirected to attacker-controlled servers hosting credential-harvesting pages.
This persistent and agile operation, characterized by rapid domain setup and takedowns, continues to pose a significant threat, especially during the ongoing Iran-Israel conflict.
Educated Manticore’s focus on sensitive targets in trust-based environments suggests a strategic intent to steal identities and credentials aligned with Iranian regime interests, making their campaigns a critical concern for cybersecurity defenders.
Indicators of Compromise (IOC)
| Indicator Type | Details |
|---|---|
| IPs | 185.130.226.71, 45.12.2.158, 45.143.166.230, 91.222.173.141, 194.11.226.9 |
| Domains | conn-ectionor.cfd, optio-nalynk.online, ques-tion-ing.xyz, sendly-ink.shop, idea-home.online |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Update
