Iranian state-sponsored threat actors have intensified their cyberattacks against critical infrastructure in the United States, with a dramatic 133% increase in malicious activity recorded during May and June 2025.
The escalation coincides with heightened geopolitical tensions surrounding the recent Iranian conflict, as cybersecurity researchers track a coordinated campaign targeting primarily Transportation and Manufacturing sectors across American companies.
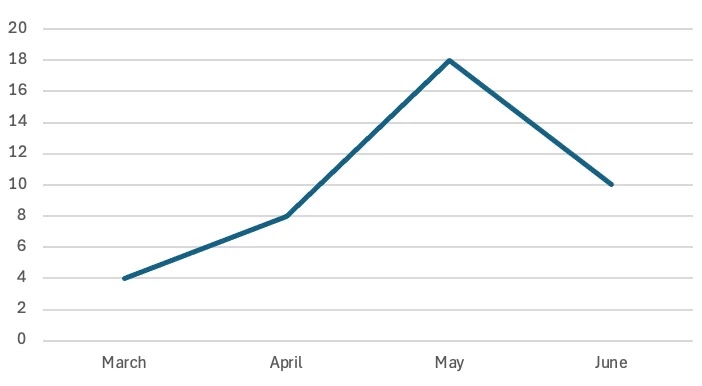
The surge in attacks represents a significant shift in Iranian cyber warfare strategy, with threat intelligence data revealing 28 documented incidents during the two-month period compared to just 12 attacks in the previous quarter.
.webp)
This aggressive campaign has prompted urgent warnings from the Cybersecurity and Infrastructure Security Agency (CISA) and the U.S. Department of Homeland Security, highlighting the critical need for enhanced security measures across industrial and critical infrastructure organizations.
Nozomi Networks Labs analysts identified six prominent Iranian Advanced Persistent Threat (APT) groups orchestrating these sophisticated attacks: MuddyWater, APT33, OilRig, CyberAv3ngers, FoxKitten, and Homeland Justice.
The threat actors have demonstrated remarkable persistence and technical sophistication, employing diverse attack vectors specifically tailored to compromise operational technology environments and industrial control systems.
MuddyWater emerged as the most prolific threat actor during this campaign, successfully breaching at least five separate U.S. companies predominantly within the Transportation and Manufacturing sectors.
APT33 followed closely, targeting three different American organizations, while OilRig, CyberAv3ngers, FoxKitten, and Homeland Justice each compromised at least two U.S. companies during the observed timeframe.
Malware Reuse and Infrastructure Persistence
A particularly concerning development involves CyberAv3ngers’ decision to reuse command and control infrastructure associated with their previous campaigns.
Security researchers discovered that the group deliberately recycled an IP address previously linked to the deployment of OrpaCrab, also known as IOCONTROL malware, which was first identified in December 2024.
This operational technology-focused malware represents a significant threat to industrial environments, capable of manipulating programmable logic controllers and other critical industrial systems.
The reuse of infrastructure demonstrates a calculated approach to resource management while potentially indicating confidence in their operational security measures.
Organizations are advised to monitor for indicators of compromise including the IP addresses 159.100.6[.]69, 169.150.227[.]230, and 95.181.161[.]50 among other malicious infrastructure identified in ongoing threat intelligence operations.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
