Claiming responsibility for the IRCCS MultiMedica cyberattack, LockBit ransomware has listed the Italian hospital as a victim, tweeted cybersecurity analyst and researcher Dominic Alvieri.
Throughout the day on 26 April, all outpatient activities, emergency room operations and the collection of reports in the MultiMedica hospitals in Milan and Sesto San Giovanni were suspended after a cyber attack, reported Italian daily Il Giorno.
IRCCS MultiMedica is a research hospital based in Milan, Italy. It is one of the only 3 IRCCSs specifically focusing on cardiovascular disease in Italy.
The name of IRCCS or technically “Istituto di Ricovero e Cura a Carattere Scientifico” indicates biomedical institutions of relevant national interest, which drive clinical assistance in strong relation to research activities.
It is not clear yet as to how the IRCCS MultiMedica cyberattack was conducted and the sum of ransom demanded. The website of the Italian healthcare provider was not functional at the time of writing.
The Cyber Express reached out to confirm the alleged IRCC MultiMedica cyberattack. However, we have not received a response so far.
The IRCCS MultiMedica cyberattack
The IRCCS MultiMedica was founded over 30 years ago and is recognized by the Ministry of Health. It houses a hospital, a teaching centre of the University of Milan, multi-specialist hospitals, an outpatient care centre, and research centres.
The group had an annual turnover of 229 million euros in 2021 which is likely why the LockBit ransomware group targeted it for financial gains. IRCCS MultiMedica also received research funding of € 2.227.909,41 from the Health Ministry in 2018.
The IRCCS MultiMedica cyberattack has put not just a large amount of patient data at risk but other affiliated national healthcare institutions too.
LockBit targets healthcare, daycare, and veteran care
The LockBit ransomware group targeted the Magnolia Care Center, a veteran’s home this week. Days after, the ransomware group added a daycare center named Keystone Smiles Community Leaning Center, Inc. It caters to preschool and pre-kindergarten children. A deadline of 15 May was mentioned on the ransomware group’s leak site post.
Several thoughts and comments were shared on online media as soon as the news came up about the group’s attack on a daycare. LockBit had publicly apologized after an affiliate attacked a children’s hospital, SickKids.
The group even went on to fire the affiliate and offered free decryptors for the encrypted files.
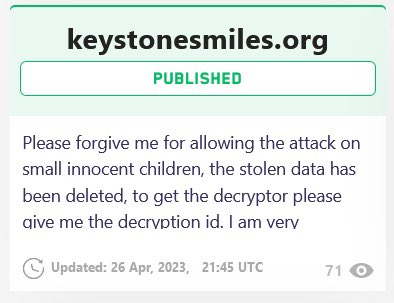
The LockBit administrator came down to apologize again amid the mixed reactions from people about the group’s recent string of cyberattacks. Dominic posted a screenshot of the apology rendered by the LockBit administrator again in a tweet titled, ‘Please forgive me.’
The administrator deleted the stolen data from the Keystone Smiles cyberattack, offered free decryptors if contacted with the decryption id and asked for forgiveness. They wrote, “I am very ashamed, but I cannot control all.”
A cybersecurity firm tweeted about the incident by saying, “Today LockBit ransomware group ransomed a day care center. When LockBit ransomware group administration discovered the victim they issued an apology and claim to have fired the affiliate.”
Expressing disdain over the targeting of children and the IRCCS MultiMedica cyberattack, and leaving apologies, Dominic wrote, “I was trying not to rant but LockBit posted IRCCS Multimedica, an Italian Hospital right after this apology.”
IRCCS MultiMedica, LockBit, and healthcare
LockBit 3.0, also known as LockBit Black, has been used by cybercriminals since June to target entities in the healthcare sector, which is similar to earlier versions of LockBit.
The U.S. Department of Health and Human Services’ Health Sector Cybersecurity Coordination Center issued a threat brief in December, warning healthcare and public health sector organizations.
“Historically, this ransomware employs a double extortion technique where sensitive data is encrypted and exfiltrated. The actor requests payment to decrypt data and threatens to leak the sensitive data if the payment is not made,” said the alert.
“With the new release, it appears that the ransomware is using a triple extortion model where the affected victim may also be asked to purchase their sensitive information.”
LockBit 3.0 has already affected entities in the healthcare sector, including a technology vendor called Advanced, which was attacked in August 2022. As a result, the National Health Service in the United Kingdom experienced IT service disruptions for weeks.
“Since its appearance, HC3 is aware of LockBit 3.0 attacks against the Healthcare and Public Healthcare (HPH) sector. Due to the historical nature of ransomware victimizing the healthcare community, LockBit 3.0 should be considered a threat to the HPH sector,” the alert said.