SEQRITE Labs’ Advanced Persistent Threat (APT) Team has uncovered a sophisticated campaign targeting Israeli organizations through weaponized Microsoft Word and PDF documents disguised as legitimate antivirus software.
The operation, tracked as UNG0801 or “Operation IconCat,” exploits the trusted branding of security vendors SentinelOne and Check Point to deceive victims into deploying malicious payloads.
The threat cluster, believed to originate from Western Asia, has been active since mid-November 2025, focusing on enterprise environments across Israel’s information technology, human resources, and software development sectors.
The campaigns leverage Hebrew-language phishing lures that mimic routine corporate communications, including compliance updates, security advisories, and webinar announcements, to establish legitimacy and increase victim interaction rates.
PYTRIC and RUSTRIC Implants
Operation IconCat comprises two distinct infection chains, both sharing a familiar operational playbook centered on antivirus icon spoofing.
The first campaign, initiated on November 16, 2025, distributes a malicious PDF titled “help.pdf” that instructs recipients to download a “Security Scanner” from Dropbox using the password “cloudstar.”
This document features authentic Check Point branding and detailed usage instructions to reinforce its appearance as legitimate security software.
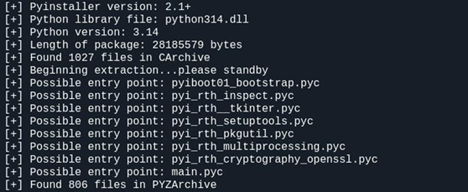
The payload delivered through this chain is PYTRIC, a PyInstaller-packaged Python executable that masquerades as a security tool.
Technical analysis reveals PYTRIC functions as a destructive wiper, capable of performing system-wide data deletion, removing backups, and communicating with command-and-control infrastructure via a Telegram bot named “Backup2040.”
The implant executes administrative-level commands that irreversibly compromise target systems, indicating a destructive rather than espionage-focused objective.
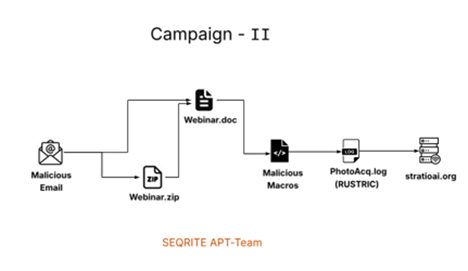
The second campaign, detected on November 17, 2025, employs spear-phishing emails impersonating L.M. Group, a legitimate Israeli human resources firm.
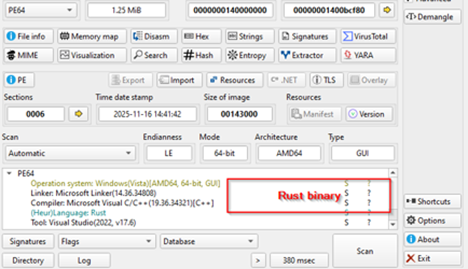
These emails carry malicious Word documents and ZIP files containing macro-enabled attachments that drop RUSTRIC, a Rust-based reconnaissance implant.
Unlike PYTRIC, RUSTRIC focuses on intelligence gathering, enumerating 28 different antivirus products installed on compromised systems including Quick Heal, CrowdStrike, Microsoft Defender, Kaspersky, and Norton while executing system reconnaissance commands such as whoami.exe, hostname.exe, and nslookup.exe.
Infrastructure and Attribution
Infrastructure analysis reveals contrasting command-and-control approaches. The first campaign relies entirely on Telegram for communication.
The macro obtains a handle to the Win32_Process class via the rootcimv2 namespace and invokes the Create method to spawn a new process.
In contrast, the second utilizes a dedicated C2 server that exhibits configuration residue from a previous domain, netvigil.org.
This incomplete server reconfiguration, including retained TLS certificates and CNAME records, suggests the threat actors are using repurposed or low-cost virtual private servers a hallmark of resource-constrained operations.
SEQRITE Labs groups both campaigns under the UNG0801 cluster based on shared operational timing, geographic targeting, and the consistent abuse of antivirus branding.
However, the divergent objectives PYTRIC’s destructive capabilities versus RUSTRIC’s espionage functions introduce complexity to attribution efforts.
While behavioral patterns suggest a unified operator or shared playbook, the tactical differences indicate potential collaboration between multiple threat groups or evolving operational priorities within a single entity.
Organizations in Israel’s technology and services sectors should implement enhanced email filtering, turn off macro execution by default, and monitor for suspicious PowerShell activity and external communications to Telegram or unverified C2 domains.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
