Critical vulnerability chain in Ivanti Endpoint Manager Mobile (EPMM) has exposed enterprise mobile device management systems to pre-authenticated remote code execution (RCE) attacks.
The flaws, tracked as CVE-2025-4427 (authentication bypass) and CVE-2025-4428 (remote code execution), allow attackers to compromise systems without credentials by chaining these vulnerabilities.
Security firm watchTowr Labs confirmed active exploitation attempts against high-value targets, escalating concerns for organizations using Ivanti’s widely deployed MDM solution.
The vulnerabilities center around Ivanti EPMM, a mobile device management platform used by organizations to enforce policies, deploy software, and manage endpoints.
Researchers identified two distinct issues enabling full system compromise:
- Authentication Bypass (CVE-2025-4427): A misconfigured API endpoint validation allows unauthenticated access to protected administrative functions through specially crafted requests. This flaw stems from improper route security configurations in Spring Framework implementations, where certain endpoints lacked authentication enforcement.
- Expression Language Injection (CVE-2025-4428): A code injection vulnerability in Hibernate Validator message templates enables arbitrary command execution via malicious payloads. Attackers can exploit improper sanitization of user-supplied input in error message generation to execute OS commands with system privileges.
When combined, these vulnerabilities permit attackers to bypass authentication controls and execute malicious code on unpatched Ivanti EPMM servers.
Let’s also confirm it with our debugger
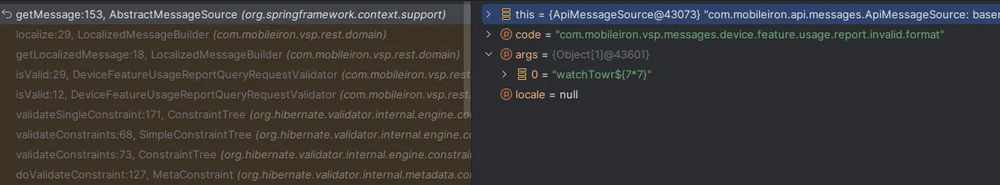
Ivanti mentioned a 0day in a 3rd party library – perhaps, we thought, maybe there are “fancy” protections in place to protect against dangerous EL payloads that can be bypassed, due to a supposed 0day in the hibernate-validator?
Ivanti’s advisory confirms limited targeted attacks leveraging this chain, with CVSS scores of 5.3 and 7.2 respectively underestimating the combined criticality.
Mechanism of the Exploitation Chain
The attack sequence begins by exploiting the authentication bypass vulnerability to access privileged API endpoints.
Researchers discovered that requests could bypass authentication checks due to inconsistent security filter configurations in Spring Security.
This allows unauthenticated attackers to submit malicious payloads to vulnerable endpoints.
The RCE vulnerability emerges from improper handling of user input in validation error messages.
When processing the format parameter, the system passes unsanitized input to Hibernate Validator’s message interpolation engine:
javacontext.buildConstraintViolationWithTemplate(formatMessage).addConstraintViolation();
This enables Java Expression Language (EL) injection through payloads like ${"".getClass().forName('java.lang.Runtime').exec('command')}.
Successful exploitation was demonstrated by executing OS commands to create files and retrieve system information from unpatched servers.
watchTowr’s analysis revealed that patched versions (12.5.0.1+) remediate the issue by removing user input from error messages and enforcing authentication checks across all API endpoints.
The vulnerabilities originate from third-party open-source components (Spring Framework and Hibernate Validator), highlighting supply chain risks in enterprise software.
Urgent Patching Requirements
Ivanti has released emergency updates addressing these vulnerabilities in EPMM versions 11.12.0.5, 12.3.0.2, 12.4.0.2, and 12.5.0.1. Security teams should:
- Immediately apply patches to all EPMM instances.
- Audit authentication logs for suspicious API access attempts.
- Monitor for abnormal process execution patterns on MDM servers.
Network defenders can detect exploitation attempts by checking web server logs for EL payload patterns like ${ in URL parameters.
Organizations should prioritize segmentation of MDM systems and review third-party component dependencies in critical infrastructure.
As MDM solutions increasingly become attack targets, this incident underscores the need for continuous vulnerability management in enterprise device governance platforms.
With active exploitation confirmed, unpatched systems risk becoming entry points for large-scale network compromises.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!