Cybersecurity researchers have uncovered a sophisticated campaign targeting global retail and consumer services organizations through credential theft and gift card fraud.
Dubbed “Jingle Thief,” this operation exploits the festive shopping season when companies are most vulnerable to financial fraud schemes.
The campaign, tracked by Unit 42 as cluster CL-CRI-1032, is orchestrated by financially motivated threat actors operating from Morocco who have been active since 2021.
Security experts assess with moderate confidence that this activity overlaps with threat groups publicly known as Atlas Lion and STORM-0539, representing a persistent and evolving threat to enterprise cloud infrastructure.
What distinguishes Jingle Thief from typical cybercriminal operations is the attackers’ ability to maintain undetected access within compromised organizations for extended periods—sometimes exceeding one year.
During this time, they thoroughly map the victim’s environment, learning how to navigate critical systems and access gift card issuance platforms.
This operational patience, combined with sophisticated reconnaissance techniques, makes detection and remediation particularly challenging for security teams.
The threat actors operate almost exclusively within cloud environments after obtaining initial credentials through phishing and SMS-based smishing attacks.
Unlike conventional cybercriminals who deploy malware or exploit endpoint vulnerabilities, these attackers leverage Microsoft 365 capabilities—including SharePoint, OneDrive, Exchange, and Entra ID—to impersonate legitimate users and conduct large-scale fraud operations.
In one observed campaign, attackers maintained access for approximately 10 months and compromised over 60 user accounts within a single global enterprise.
The threat actors strategically align their operations with holiday periods, capitalizing on reduced staffing levels and increased gift card transaction volumes to obscure their fraudulent activities.
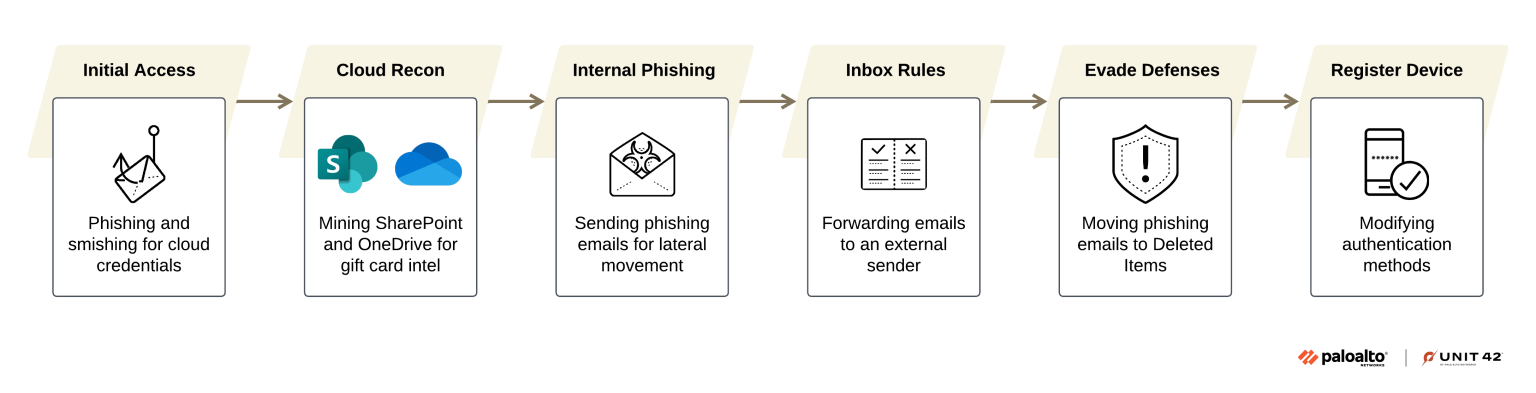
Sophisticated Attack Chain
The Jingle Thief attack lifecycle begins with highly customized phishing campaigns designed to harvest cloud credentials.
Threat actors invest significant effort in reconnaissance, gathering intelligence on target organizations including branding elements, login portals, email templates, and domain naming conventions. This enables them to craft convincing phishing content that bypasses both user awareness and security tools.
A credential phishing page crafted by the threat actors to impersonate a legitimate Microsoft 365 login portal, tailored to the victim organization’s branding.

Phishing messages often employ deceptive URL formatting techniques and are frequently delivered through self-hosted PHP mailer scripts sent from compromised WordPress servers.
Some lures impersonate nonprofit organizations to enhance credibility and increase victim engagement. Once credentials are harvested, attackers authenticate directly to Microsoft 365 environments without requiring malware deployment.
After gaining initial access, the attackers perform extensive reconnaissance within SharePoint and OneDrive, searching for internal documentation related to gift card issuance workflows, ticketing system exports, VPN configurations, and organizational infrastructure details.
This intelligence gathering helps them identify pathways to gift card systems while maintaining a low detection profile.


To expand their foothold, threat actors conduct internal phishing campaigns from compromised accounts, sending fake IT service notifications that mimic ServiceNow alerts or account inactivity notices.
They also create malicious inbox rules to automatically forward emails containing gift card approvals and financial workflows to attacker-controlled addresses, enabling passive monitoring of internal communications.
Why Gift Cards Attract Cybercriminals
Gift cards represent an ideal target for financially motivated actors due to their rapid monetization potential. Threat actors resell stolen gift cards on gray-market forums at discounted rates, enabling near-instant cash flow.
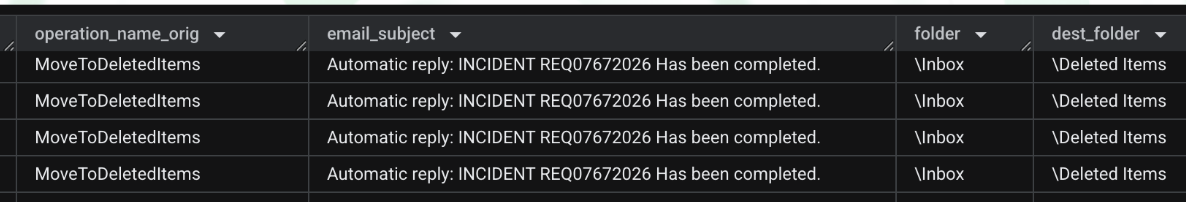
The attackers moving phishing email replies from the Inbox folder to the Deleted Items folder.

These digital assets require minimal personal information for redemption, are difficult to trace, and can facilitate low-risk money laundering across international jurisdictions.
Retail environments are particularly vulnerable because gift card systems often have weak access controls, broad internal permissions, and limited monitoring capabilities.
In observed attacks, threat actors made repeated attempts to issue high-value cards across different programs, potentially using them as collateral in money-laundering schemes to convert digital theft into untraceable currency.
Attribution and Infrastructure Analysis
Campaign activities almost exclusively originated from IP addresses geolocated in Morocco, with recurring device fingerprints and login behaviors observed across multiple incidents.
Unlike many threat actors who obscure their origins through VPN services, Jingle Thief operators frequently made no attempt to hide their Moroccan location, only occasionally using Mysterium VPN when accessing compromised accounts.
Network metadata consistently matched Moroccan telecommunications providers including MT-MPLS, ASMedi, and MAROCCONNECT.
In April and May 2025, the threat actors launched coordinated attacks across multiple global enterprises, demonstrating their continued operational capability and targeting focus.
This activity was identified through behavioral anomalies detected by Cortex User Entity Behavior Analytics (UEBA) and Identity Threat Detection and Response (ITDR) systems.
The Jingle Thief campaign underscores the critical shift in enterprise security toward identity-based threat detection. As attackers increasingly operate entirely within cloud environments by abusing legitimate platform features, organizations must prioritize monitoring user behavior, login patterns, and identity misuse to enable early detection and effective response against these sophisticated fraud operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
