Johns Hopkins University released a cyber attack notice on its website confirming that it had suffered a data breach. The network of Johns Hopkins University and Johns Hopkins Health Systems were investigating the cyber attack. The Johns Hopkins University cyber attack was a result of the MOVEit data breach
Details of the Johns Hopkins University cyber attack
Following the cyber attack on the file transfer service provider MOVEit, several of its clients were exposed to hackers. The Cl0p ransomware group claimed the MOVEit cyber attack and set the deadline of 12 June initially which was later shifted to June 14.
According to the FAQ section of the JHU cyber attack notice, the question regarding the timing of the breach received the following response: “The breach took place on May 31. Johns Hopkins swiftly implemented measures to safeguard our systems, and our cybersecurity team is actively collaborating with data security experts and law enforcement to assess the extent of the compromised information.
The data stolen by the Cl0p ransomware group from the Johns Hopkins University cyber attack has not been disclosed yet. However, the JHU data breach notice read that sensitive personal and financial information may have been stolen by the hackers.

The stolen data from the systems of Johns Hopkins University and Health Systems may include names, contact information, and health billing information.
The university notice read that the Johns Hopkins University cyber attack has had no negative impact on the operations of the university or healthcare.
The officials of JHU will be alerting impacted individuals from the Johns Hopkins University and Johns Hopkins Health Systems data breach.
After the Johns Hopkins University cyber attack, the website remained operational.
MOVEit data breach and its impact on multiple targets
The Cl0p ransomware group claimed to have attacked several companies via the MOVEit Transfer security breach. Britain-based companies including BBC, British Airways, and Boots were named as victims on the hacker’s website.
Aer Lingus was named however, not all the organizations Cl0p breached were solely due to the MOVEit cyber attack.
Through MOVEit, the hackers gained access to the payroll service provider Zellis which had data stored from other clients that the hackers misused.
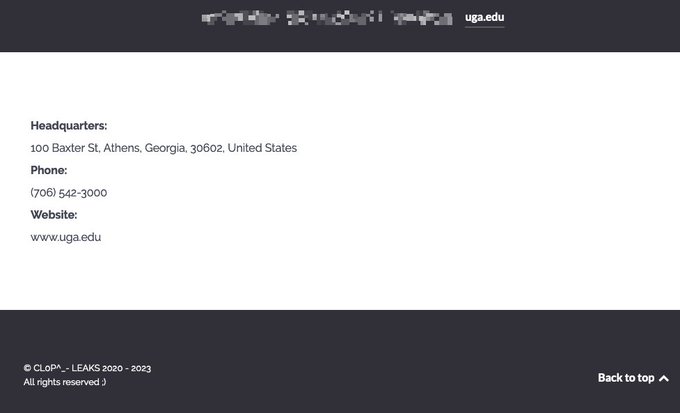
Besides Johns Hopkins University cyber attack, Cl0p has recently posted the University of Georgia to its victim list, according to a tweet by a Threat Analyst, Brett Callow. Ernst & Young has been informing its clients of the MOVEit data breach, Brett added.
Contrary to the hackers’ threat of data leakage on June 14, no data has been reported leaked so far. Furthermore, it remains uncertain whether the organizations mentioned were involved in the MOVEit cyber attack.
The Cl0p hackers also posted another five names on its website as victims, Brett’s tweet stated.
Contrary to the hackers’ threat of data leakage on June 14, no data has been reported leaked so far. Furthermore, it remains uncertain whether the organizations mentioned were involved in the MOVEit cyber attack.
Cl0p claimed that it will wait for another 7 days until they leak data from the named organizations.
JHU is the 27th victim of the MOVEit cyber attack, Brett tweeted.
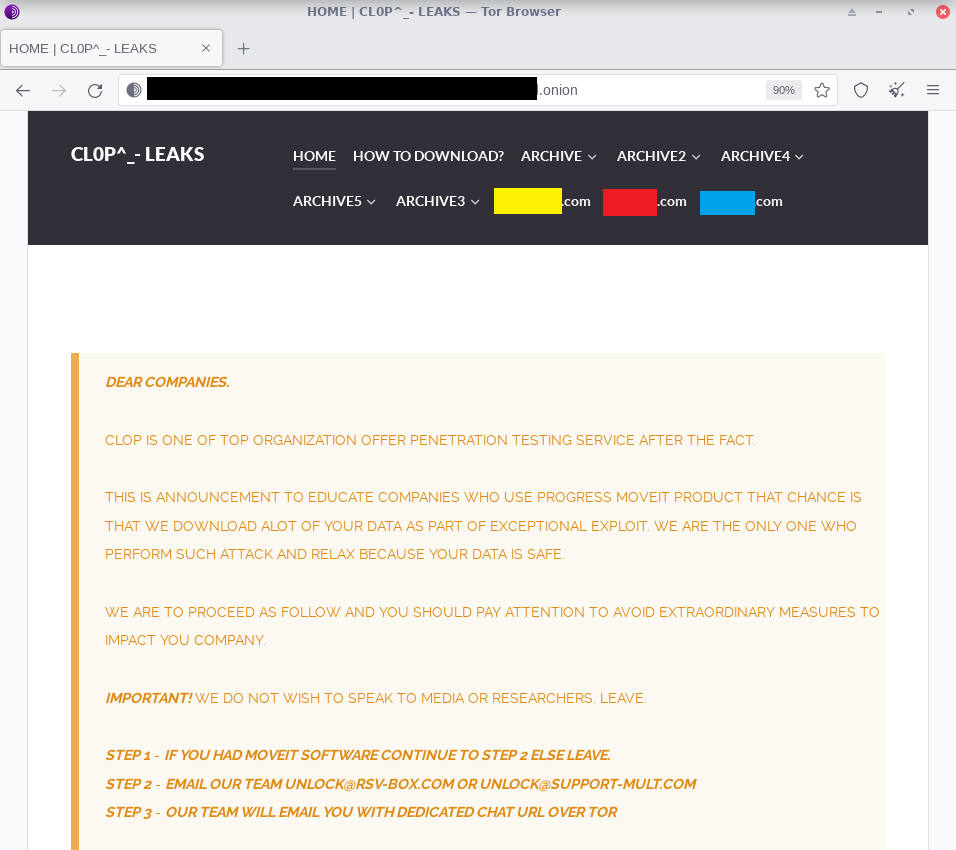
Cybersecurity researchers John Hammond tweeted the above image about the MOVEit cyber attack and wrote that Cl0p had added 3 references on their leak site for victims that didn’t respond to the hacker’s demands.
The screenshot also showed Cl0p’s website which the hackers enhanced with menus and tabs to have an archive of stolen data.
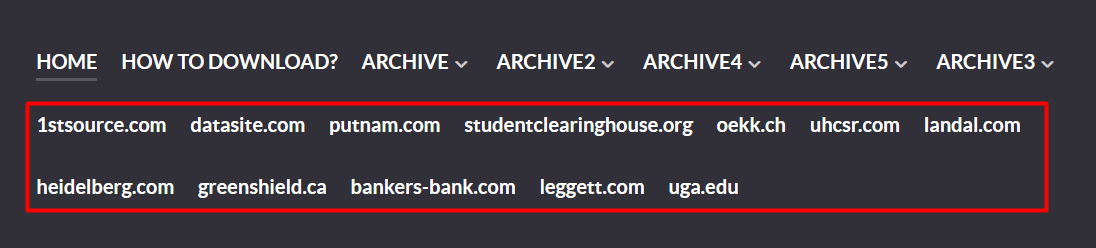
Cybersecurity researchers have been tweeting about the names added by Cl0p post the passing of the deadline for ransom negotiations. German Fernandez posted the above screenshot. However, the authenticity of the claims has not been proven yet. These are just names posted by the hackers, so far.
Cl0p and file transfer service providers
Cl0p has used the same tactic in the past by hacking Fortra’s GoAnywhere, a file transfer service provider. Through the GoAnywhere vulnerability exploitation, the ransomware group managed to gain access to hundreds of its clients.
Furthermore, in December 2020, Cl0p targeted another file transfer service provider Accellion via a zero-day vulnerability through which it gained access to Accellion’s clients.
This makes it clear that file transfer service providers need to have a robust team to hunt bugs and patch them ASAP because hackers from the Cl0p ransomware group are looking for them.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
