The EventLogs have long been the go-to source for incident investigators in the realm of Windows operating system forensics.
However, these logs often fall short when it comes to detecting suspicious behavior, necessitating the use of additional audit logs or tools like Sysmon.

Enter Event Tracing for Windows (ETW), a powerful yet often overlooked feature that offers a more comprehensive approach to Windows forensics. ETW is a robust system designed to manage events generated by the kernel and processes.
Initially created for application debugging, it has evolved into a crucial component for collecting and managing EventLogs.
.webp)
In recent years security analysts at JPCert observed that ETW has become an integral part of the detection logic employed by EDR products and antivirus software.
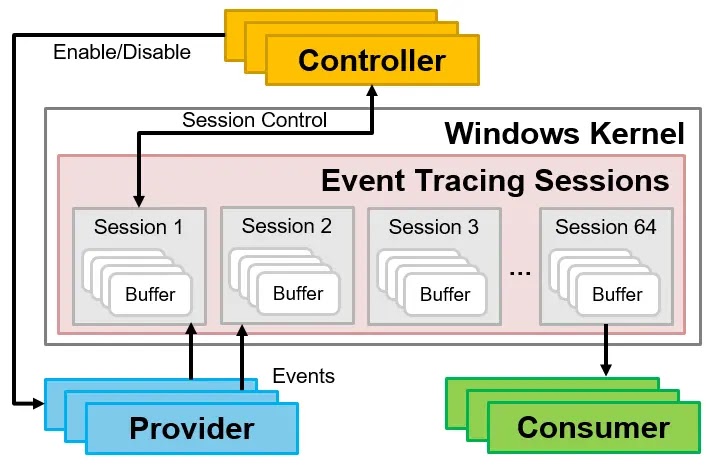
The architecture of ETW consists of four main components:
- Providers: Applications and drivers that send events
- Consumers: Applications that receive events
- Sessions: Relay events from providers to buffers
- Controllers: Create, start, and stop sessions
Free Ultimate Continuous Security Monitoring Guide - Download Here (PDF)
ETW’s Forensic Potential
What sets ETW apart is its ability to log various OS behaviors as events by default, offering a wealth of information beyond traditional EventLogs. This capability makes ETW an invaluable tool for forensic investigators and security professionals.
Several ETW providers are particularly useful for incident investigation and malware detection:
- Microsoft-Windows-Threat-Intelligence
- Microsoft-Windows-DNS-Client
- Microsoft-Antimalware-AMFilter
- Microsoft-Windows-Shell-Core
- Microsoft-Windows-Kernel-Process
- Microsoft-Windows-Kernel-File
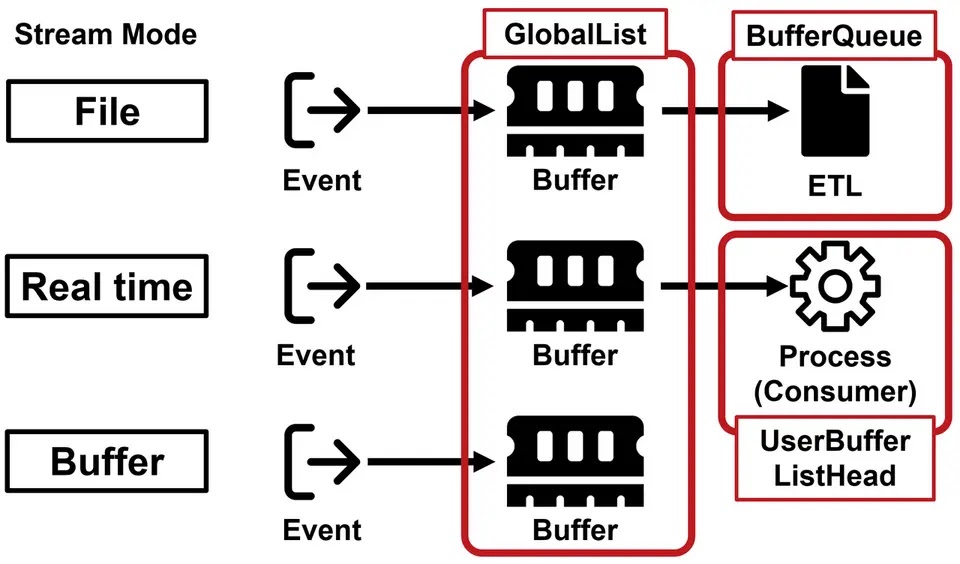
While some ETW events are saved as files by default, many are read from buffers in real-time. This means that even if an attacker deletes ETL files, valuable information may still reside in these buffers.
.webp)
JPCert has developed a Volatility plugin called ETW Scanner, which can recover ETW events from memory images, providing investigators with a powerful tool for incident response.
.webp)
The recovered ETW events can offer critical insights during investigations. For instance, the LwtNetLog ETW session, enabled by default, collects various network-related information.
By analyzing these events, investigators can uncover malware communication patterns, DNS queries, and other network activities that might otherwise go unnoticed.
.webp)
As Windows forensics continues to evolve, ETW emerges as a powerful ally for security professionals. Its ability to provide detailed system behavior logs, coupled with tools like the ETW Scanner, offers a new dimension in incident investigation and malware detection.
Besides this, by leveraging ETW, investigators can gain deeper insights into system activities, potentially uncovering threats that traditional logging methods might miss.
Analyze Unlimited Phishing & Malware with ANY.RUN For Free - 14 Days Free Trial.
