A hacking unit of North Korea’s Reconnaissance General Bureau (RGB) was linked to the JumpCloud breach after the attackers made an operational security (OPSEC) mistake, inadvertently exposing their real-world IP addresses.
The hacking group, tracked as UNC4899 by Mandiant, was previously observed using a combination of commercial VPNs and Operational Relay Boxes (ORBs) using L2TP IPsec tunnels to hide their actual location.
Mandiant says UNC4899 threat actors have used many VPN providers for this purpose in previous campaigns, including ExpressVPN, NordVPN, TorGuard, and others.
While North Korean state hackers are known for using commercial VPN services to mask their IP addresses and actual locations, during the JumpCloud attack, the VPNs they were using failed and exposed their location in Pyongyang while connecting to a victim’s network.
“Mandiant observed the DPRK threat actor UNC4899 connecting directly to an attacker-controlled ORB from their 175.45.178[.]0/24 subnet,” the researchers said.
“Additionally we observed the DPRK threat actor log directly into a Pyongyang IP, from one of their jump boxes. Our evidence supports that this was an OPSEC slip up since the connection to the North Korean netblock was short-lived.”
Apart from this OPSEC oversight, Mandiant security researchers also found attack infrastructure overlapping with previously associated hacks linked to North Korean hackers, further bolstering the attribution of the breach to North Korean hackers.
“We assess with high confidence that UNC4899 is a cryptocurrency-focused group that falls under the RGB. UNC4899’s targeting is selective, and they have been observed gaining access to victim networks through JumpCloud,” Mandiant added.
“Mandiant has observed UNC2970, APT43, and UNC4899 all utilize similar infrastructure.”
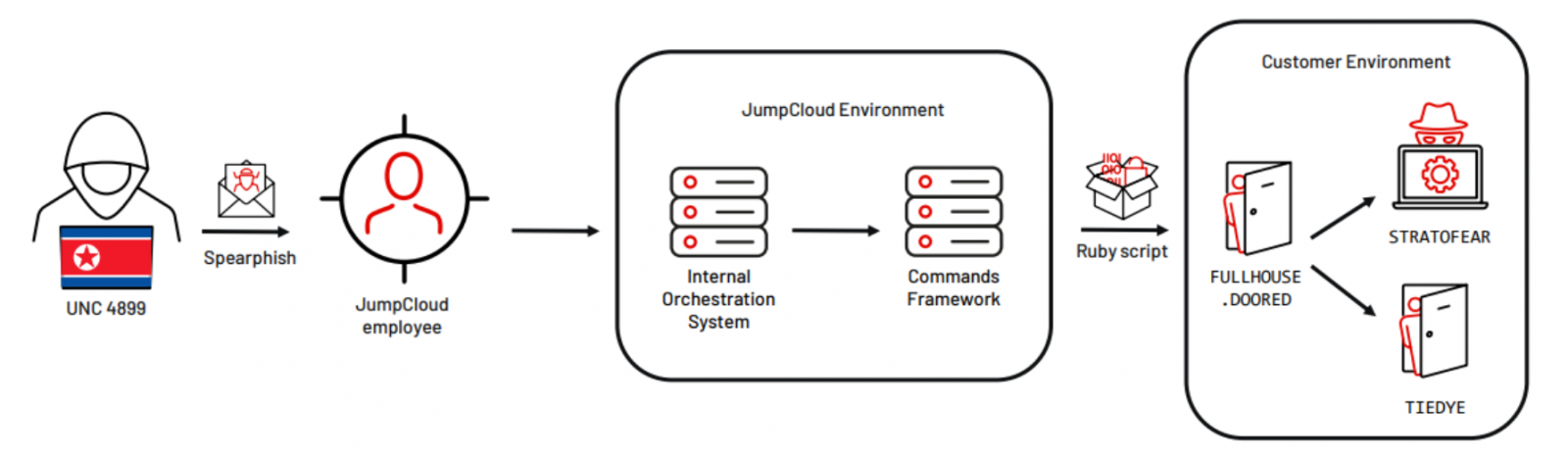
On Thursday, JumpCloud also confirmed that a North Korean APT group was behind the June breach following attribution from security researchers at SentinelOne and CrowdStrike earlier that day.
Senior Incident Response Consultant Austin Larsen told BleepingComputer that the attackers also hit a downstream victim following their breach of JumpCloud.
Mandiant foresees that additional victims may be currently dealing with the repercussions of this attack.
JumpCloud force-rotated all admin API keys on July 5th, one week after the hacker breached its network via a spear-phishing attack.
While the company has now attributed the attack, it has not yet disclosed the number of impacted customers.
Colorado-based JumpCloud is an operational directory-as-a-service platform that offers single sign-on and multi-factor authentication services to a vast network of over 180,000 organizations spanning more than 160 countries.
