Newly disclosed information-stealing malware dubbed Katz Stealer has emerged as a significant threat to users of Chromium and Gecko-based browsers, with capabilities to extract sensitive data from over 78 browser variants.
Developed in C and Assembly (ASM) for lightweight efficiency, the malware targets credentials, cookies (including version 20+), autofill data, CVV2 codes, OAuth tokens, cryptocurrency wallets, and messaging platforms like Discord and Telegram.
The threat actor behind the stealer has released a customizable build panel with anti-virtual machine (anti-VM) safeguards and a web-based command-and-control (C2) interface for managing stolen data, signaling a concerning evolution in infostealer sophistication.
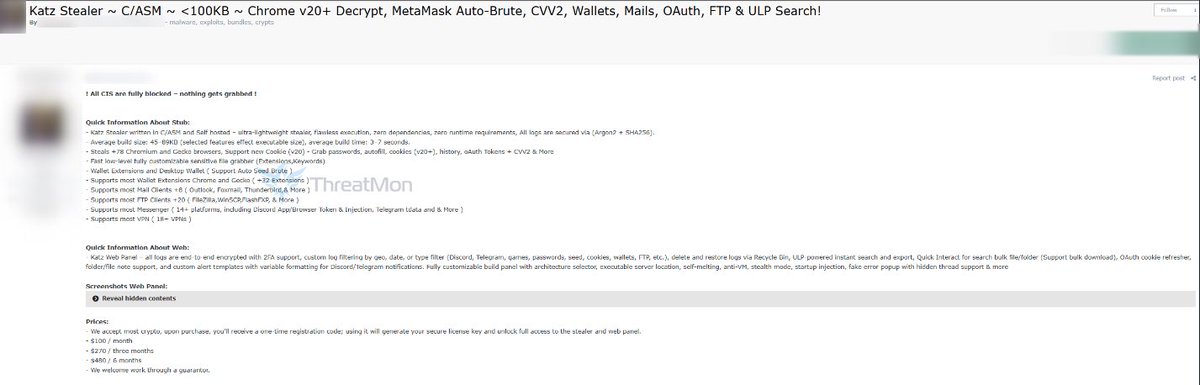
Katz Stealer distinguishes itself through its broad targeting of browser architectures and third-party applications.
The malware actively exfiltrates data from Chromium-based browsers like Google Chrome, Microsoft Edge, and Brave, as well as Gecko-based browsers such as Mozilla Firefox and Waterfox.
Its data harvesting extends beyond typical credential theft to include OAuth tokens-critical for maintaining authenticated sessions-and CVV2 codes stored in autofill profiles, which could enable financial fraud at scale.
The stealer also compromises cryptocurrency wallets (e.g., MetaMask, Exodus) and extracts credentials from email clients like Thunderbird and FTP clients such as FileZilla.
Notably, its ability to parse messaging platforms like Discord and Telegram suggests threat actors aim to hijack communication channels or exploit authenticated sessions for social engineering.
Security researchers highlight that the inclusion of cookie theft for modern browser versions (v20+) indicates active development to bypass recent security updates in these platforms.
Anti-Detection Mechanisms
The malware’s operational flexibility stems from its customizable build panel, which allows attackers to tailor payloads based on target environments.
Developers can enable anti-VM checks to hinder analysis in sandboxed environments and activate privacy-focused features to minimize detection by endpoint protection tools.
This modular approach enables threat actors to deploy lighter versions for broad campaigns or fully equipped variants for high-value targets.
Katz Stealer’s web-based C2 panel provides adversaries with streamlined log management through encrypted log storage, batch search functionality, and export tools.
The panel’s search feature supports filtering by data type (e.g., “cryptocurrency wallets” or “CVV2”), enabling rapid monetization of stolen information.
Analysts warn that this enterprise-grade C2 infrastructure lowers the barrier to entry for less technically skilled threat actors, potentially increasing the malware’s proliferation.
Implications for Cybersecurity Defenses
According to the Report, The emergence of Katz Stealer underscores the escalating arms race between malware developers and security teams.
Its use of low-level languages like ASM optimizes performance while complicating reverse-engineering efforts.
Organizations relying on Chromium or Gecko-based browsers must prioritize monitoring for anomalous cookie exports or unauthorized OAuth token usage, as these represent primary exfiltration vectors.
Defensive recommendations include enforcing multi-factor authentication (MFA) for all OAuth-integrated services and segmenting cryptocurrency wallet access from general browsing activities.
Network defenders should also scrutinize processes interacting with browser profile directories for unauthorized access.
While no specific mitigation tools are confirmed yet, behavior-based detection strategies focusing on ASM-level memory operations may help identify infiltration attempts.
As Katz Stealer’s operators continue refining its capabilities, the malware poses a persistent threat to both individual and enterprise security postures.
Its modular design and dark web availability suggest imminent adoption by cybercriminal groups, necessitating proactive defense adjustments across industries.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
