North Korean state-sponsored threat actors have escalated their cyber operations with the deployment of sophisticated new malware variants designed to establish persistent backdoor access to compromised systems.
Recent investigations by threat intelligence researchers have uncovered two distinct toolsets from prominent DPRK-aligned hacking groups: Kimsuky’s newly identified HttpTroy backdoor and an upgraded version of Lazarus’s BLINDINGCAN remote access tool.
Both campaigns demonstrate the continued evolution of North Korean cyber capabilities and their commitment to espionage operations targeting strategic victims across multiple countries.
The discoveries underscore a troubling trend in advanced persistent threat actor behavior, where established groups continuously refine their tradecraft to evade detection while maintaining operational effectiveness.
Security researchers emphasize that these tools represent significant developments in the DPRK cyber arsenal, incorporating multiple layers of obfuscation and sophisticated persistence mechanisms that challenge traditional defensive measures.
The Kimsuky operation targeted a single victim in South Korea using a social engineering approach designed to appear as legitimate business correspondence.
The attack chain began with a ZIP archive masquerading as a VPN service invoice, specifically named to reference a Korean company and SSL VPN management services.
Once executed, the malicious payload initiated a multi-stage infection process that ultimately delivered the HttpTroy backdoor to the compromised system.
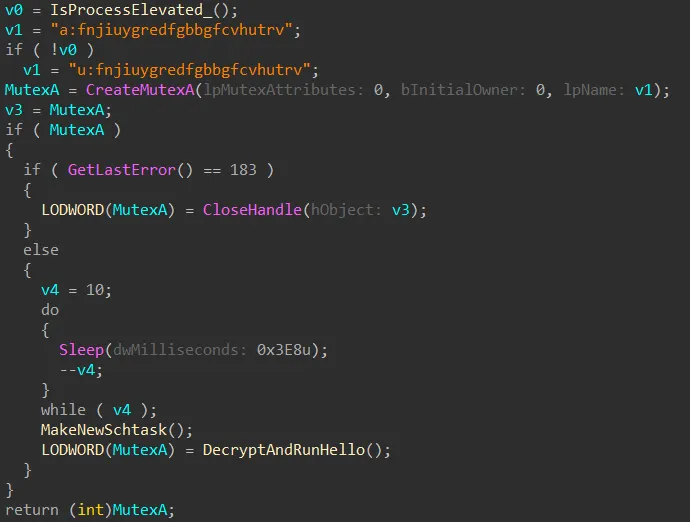
The infection sequence involves three distinct components working in concert to establish persistent access. First, a lightweight Go-based dropper containing three embedded files performs initial system compromise while displaying a decoy PDF document to maintain the illusion of legitimacy.
This dropper uses simple XOR encryption with the key 0x39 to decrypt its embedded payloads before writing them to disk. The attack chain then progresses to MemLoad_V3, a first-stage backdoor responsible for establishing persistence through a scheduled task impersonating AhnLab antivirus update functionality.
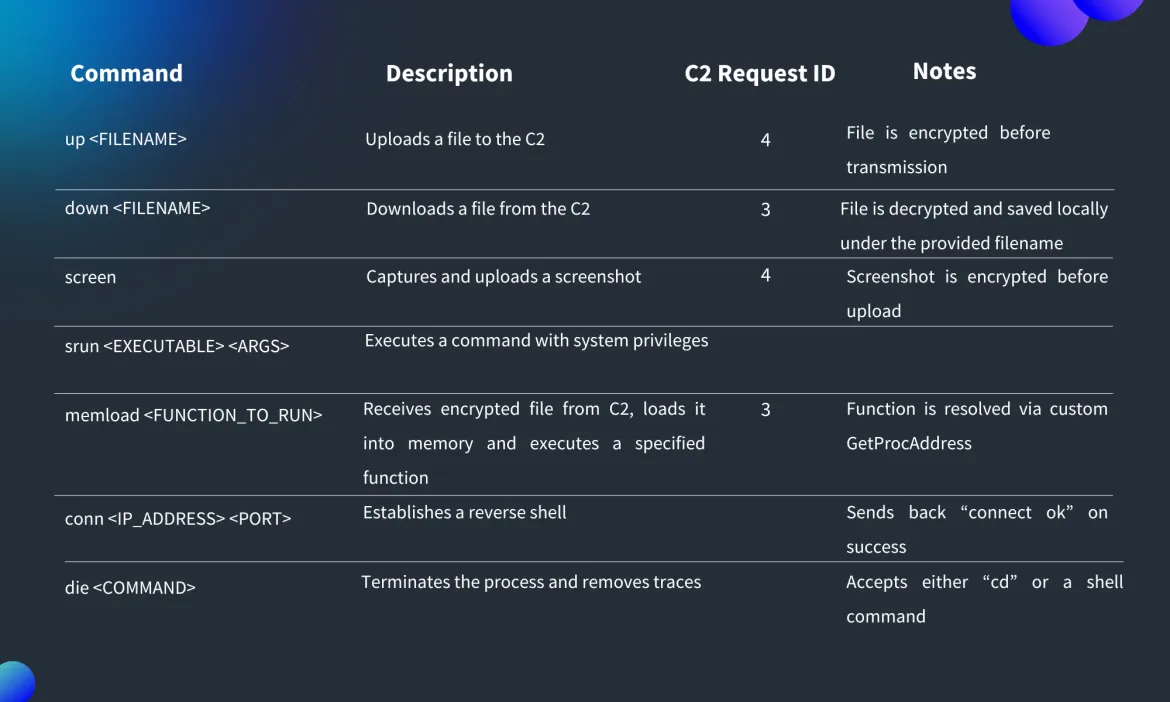
The final HttpTroy payload represents a highly capable backdoor offering attackers comprehensive control over infected systems.
Its functionality includes file upload and download capabilities, screenshot capture and exfiltration, command execution with elevated privileges, in-memory executable loading, reverse shell establishment, and process termination for trace removal.
Communication with command-and-control infrastructure occurs exclusively through HTTP POST requests, with all data obfuscated using XOR encryption and Base64 encoding.
BLINDINGCAN Remote Access Capabilities
Parallel to the Kimsuky campaign, Lazarus Group targeted two victims in Canada with an updated variant of their established BLINDINGCAN remote access tool.
Researchers intercepted this attack mid-chain, observing a new version of the Comebacker malware facilitating deployment of the enhanced BLINDINGCAN variant.
While technical details of this specific campaign remain under investigation, the operation demonstrates Lazarus’s ongoing commitment to maintaining and improving their existing malware frameworks.
Both campaigns share common characteristics typical of DPRK cyber operations, including heavy use of obfuscation techniques to complicate analysis and evade security solutions.
HttpTroy specifically employs custom API hashing, dynamic string reconstruction during runtime, and SIMD instruction-based obfuscation to resist both static and dynamic analysis attempts.
All transmitted data (both commands and responses) is obfuscated using a two-step process: XOR encryption with the key 0x56, followed by Base64 encoding.

Security professionals recommend organizations implement multiple defensive layers to mitigate threats from sophisticated state-sponsored actors.
Critical measures include treating unexpected email attachments with extreme caution, recognizing that files with extensions like .scr are executable programs rather than documents, maintaining updated security software with current threat intelligence, and implementing behavioral detection capabilities that can identify suspicious post-compromise activities.
The emergence of these new tools reinforces the persistent and adaptive nature of North Korean cyber threat actors, requiring continuous vigilance and updated defensive strategies from potential target organizations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
