A massive new botnet dubbed “Kimwolf” has infected over 2 million devices globally, transforming innocent users’ home internet connections into secret proxy nodes for cybercriminals.
According to a new report by security firm Synthient, the botnet has grown explosively by exploiting unsecured Android TV boxes and a critical vulnerability in major residential proxy networks.
The Kimwolf infection is widely distributed, with heavy concentrations in Vietnam, Brazil, India, Russia, Saudi Arabia, and the United States.
Security researchers have determined that approximately two-thirds of the infected devices are off-brand Android TV boxes often sold on major e-commerce platforms like Amazon and Walmart that lack basic security or authentication measures.
How the Attack Works
Unlike traditional malware that spreads through direct downloads, Kimwolf uses a sophisticated tunneling method.
In November 2025, researchers from Quokka published a report (PDF) detailing serious security issues in Android-based digital picture frames running the Uhale app including Amazon’s bestselling digital frame as of March 2025.
Benjamin Brundage, founder of Synthient, discovered that the botnet operators exploited a flaw in residential proxy services, explicitly targeting the China-based provider IPIDEA.
The vulnerability allowed attackers to “go upstream” through the proxy network. By manipulating Domain Name System (DNS) settings to match local network addresses (such as 192.168.0.1), attackers could bypass protections and talk directly to devices on the internal networks of proxy users.
Once inside a home network, the malware scans for devices that were shipped with “Android Debug Bridge” (ADB) enabled a diagnostic tool that should be turned off on consumer products.
“The short version is that everything you thought you knew about the security of the internal network behind your Internet router probably is now dangerously out of date,” the report warns.
The Proxy Economy and Hidden Dangers
The malware is often bundled with mobile apps, games, or pre-installed on “jailbroken” streaming devices that promise free access to subscription content.
When a user installs these apps or plugs in a compromised TV box, their device becomes a “residential proxy.”
Criminals rent these proxies to disguise their location and traffic. However, Kimwolf takes this a step further.
Infected devices are forced to participate in Distributed Denial-of-Service (DDoS) attacks capable of knocking websites offline, as well as ad fraud, content scraping, and account takeovers.
Following notifications from Synthient, major proxy providers like IPIDEA and Oxylabs claim to have patched the specific vulnerabilities that allowed local network access.
IPIDEA’s security officer stated that the flaw was traced to a legacy testing module which has since been removed.
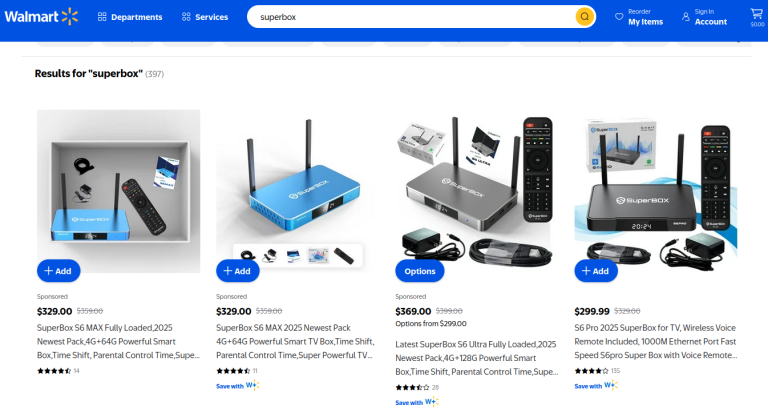
Experts advise consumers to be wary of cheap, no-name electronics. “I want the consumer to be paranoid of these crappy devices,” said Chad Seaman, a principal security researcher at Akamai Technologies.
To protect themselves, users are urged to:
- Avoid “fully loaded” Android TV boxes that promise free pirated content.
- Isolate IoT devices on a “Guest” Wi-Fi network to prevent them from accessing other devices on the home LAN.
- Check Synthient’s newly released list of compromised device models and remove them immediately if found on their network.
As the Kimwolf botnet continues to rebuild itself despite takedown attempts, the incident highlights the fragility of home network security in an era of cheap, interconnected devices.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
